Best Of
Re: 2FA authentication by EMail
since this old thread now and then gets some new feeding, i take the point to ask a general question for anyone in Zyxel: why are you not developing 2FA by email on H series? I am a bit astonished because, apart judging whether it is useful or not (this is personal), it was something existing back to the old usg40/60 series, why should we reduce features instead of increasing them?
Is there any technical problem that i don't see that makes this development difficoult? The firewall already sends email, the page for the code already exist… i must be missing something.
Most of my firewalls are ATP, most of my configuration involve VPNs with 2FA, most of my users prefer email to Google Authenticator.
Some employees use personal smartphone and are not willing to install another app (i know, it seems strange nowadays that someone doesn't use 2FA at all but most of the times that i implement google 2FA the new user has to install the app for the first time)
So please Zyxel let 2FA by email work on H series
Re: Domain zone forwarder through tunnel
Hmm ok, is there a reason why this is now like this? Will have to test this out. Or will it in future firmwares be possible again to do it the old way?
Domain zone forwarder through tunnel
In FLEX (non H) series I was able to add a Domain Zone Forwarder in DNS to an IP-Address behind a tunnel. So the other site could resolve server.domain.local for example. I could select Private DNS Server then and then it mentioned "query via tunnel".
In FLEX H Series I don't have that option anymore, can only select one of the interfaces, but not tunnel. How can I resolve this? Do I have to work through routing rule?
Re: 2FA authentication by EMail
So I had another topic running
Domain zone forwarder through tunnel — Zyxel Community
And I mentioned my problem of 2FA not possible with EXT-GROUP-USER which now works fine in older FLEX Series. This answer from ZyXEL_Melen concerns me a bit:
Why would ZyXEL implement a 2FA method from a concurrent (Cisco)?
We use now for years at all our clients IS Decisions Userlock, so if we have to move to a payed model, I'd prefer to use Userlock, and not 2 products like Cisco Duo. In that way 2FA through mail was very acceptable. I also see that Cisco Duo will only work with SecuExtender and not the new implementation of OpenVPN?
But as I see ZyXEL will implement it for local users, then why not for EXT-GROUP-USERS?
I have now 90 FLEX non H firewalls in production en 6 H firewalls. In future if the old FLEX Series become out of support I have to replace them to newer models, but features like 2FA through mail with EXT-GROUP-USER will have to be migrated to off course, or at least decent support by multiple other 2FA suppliers(if it's Google authenticator, that's fine by me) and of course with OpenVPN which we all have been waiting for years on the old FLEX series now.
I have a client with Barracuda firewall and 30 VPN Users which also use 2FA. I finally was able to let that client to decide to replace his Barracuda firewall to a FLEX H in combination with 4 extra firewalls on different sites, but if I can't implement proper 2FA on EXT-GROUP-USER with OpenVPN, I will have a problem.
Re: Domain zone forwarder through tunnel
I have for this moment solved it by adding manual DNS records in DNS Server on Firewall
Re: Domain zone forwarder through tunnel
It's the 3rd issue I have with my upgrades/new installations to FLEX H series…(done 5 so far)
In a way it doesn't feel like complete product, but I like it because of the full Nebula integration.
My issues so far:
- At first no EXT-GROUP-USER available to connect AD → solved now
- No 2FA possible with EXT-GROUP-User → waiting for firmware update?
- Domain zone forwarder through tunnel → workaround as mentioned above maybe, but if it's in the roadmap to be solved soon, I prefer to wait. However I will need it at another client in may/june.
Re: XGS1930 and MAC filtering on a port
Hi @Venta
For this purpose, you need to configure via device's local GUI since it is not supported on Nebula control center.
Here are the steps:
- Upgrade your XGS1930 to V5.00 firmware version.
- Finish other configurations on Nebula first.
- Access device local GUI to configure port security & Static MAC Forwarding.
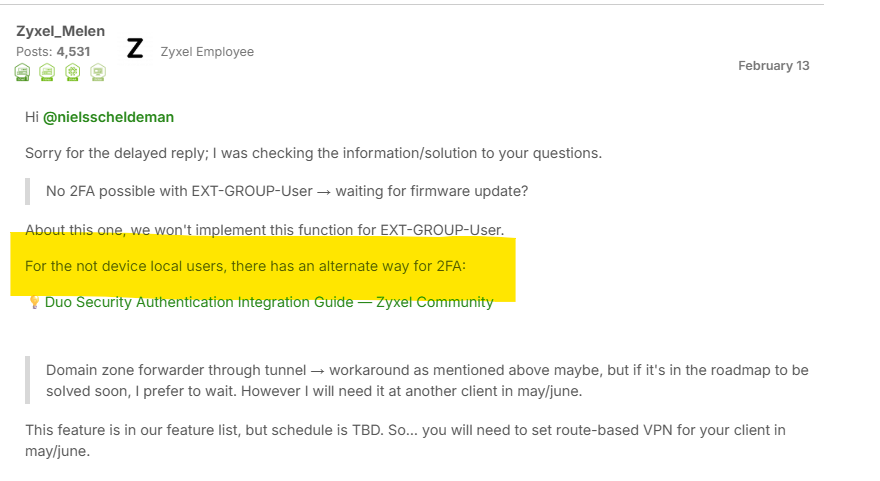
- Set port security:
Path: Menu > Security > port security.
- Activate port security.
- Activate port security for specific port(s).
- Inactivate address learning.
- Limited number of learned MAC address needs to be 0.
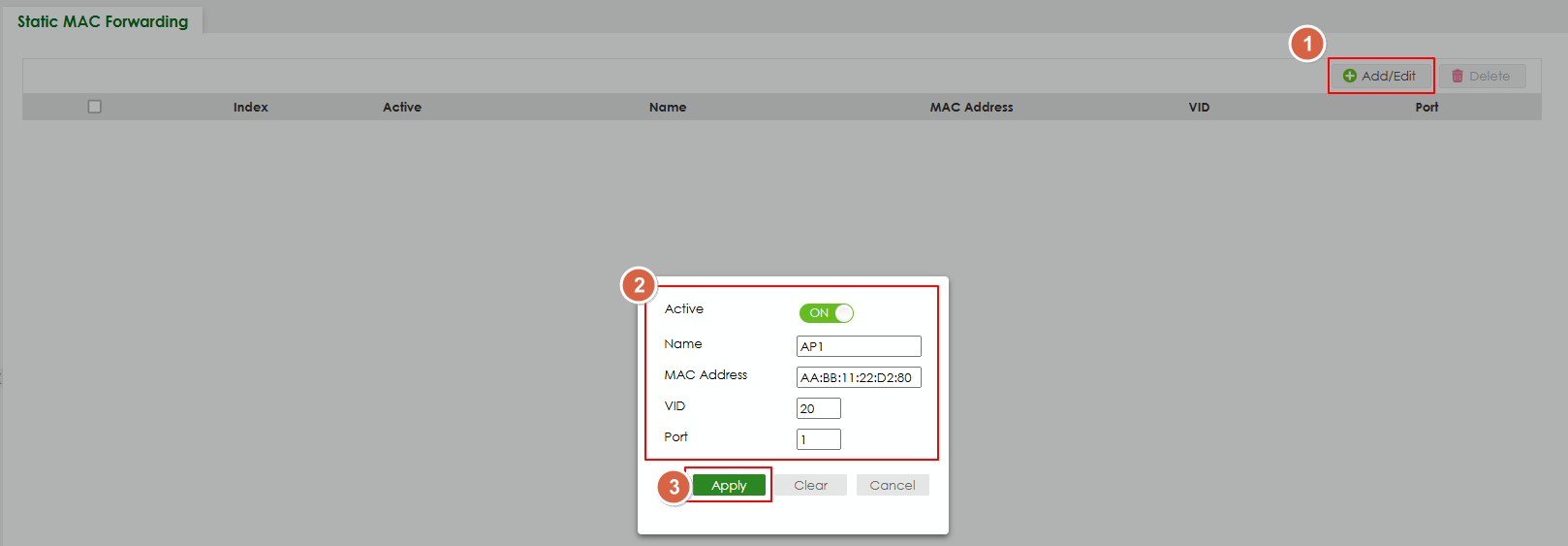
- Set static MAC forwarding:
Path: Menu > Switching > Static MAC Forwarding.
- Click Add/Edit button to add the MAC address.
- Enter the MAC address and other value.
- Click apply button.
- Set port security:
Note:
- The configuration that edited/configured from device's local GUI will not sync to Nebula.
- Change configuration on Nebula might cause these configurations been overwritten.
- Local device's local GUI requires to use your site's local credential. Please reference this FAQ to find it.
Hope this helps.
Re: Interface Connectivity Check and Policy route Connectivity Check don't work together
Hi @PeterUK
We have addressed this issue, and it will be fixed in the future firmware release. (About 2026 Q2.)
Re: Cloud-Saving Mode enabled when last logged in just 4 days ago
Hi @Lewpy
Thanks for reporting it. I have started the investigation and will update you once we have further information.
PSA Integrations for MSP
Hoping we can get some PSA integrations for the MSPs in the group. It would be great to have client, site and hardware data along with licensing passed to a PSA so things are easier to manage - especially licensing renewals.
Currently, we are using HaloPSA but also see a need to integrate with Connectwise Manage and autotask.
There is a pretty cool company (https://www.mspcentric.io/) that already has the API integrations for all of the popular PSA tools, you would just need to work and get the nebula API connected.
This really is the next step for the MSP license to help us MSPs!