How to create a VLAN ?
Hello guys,
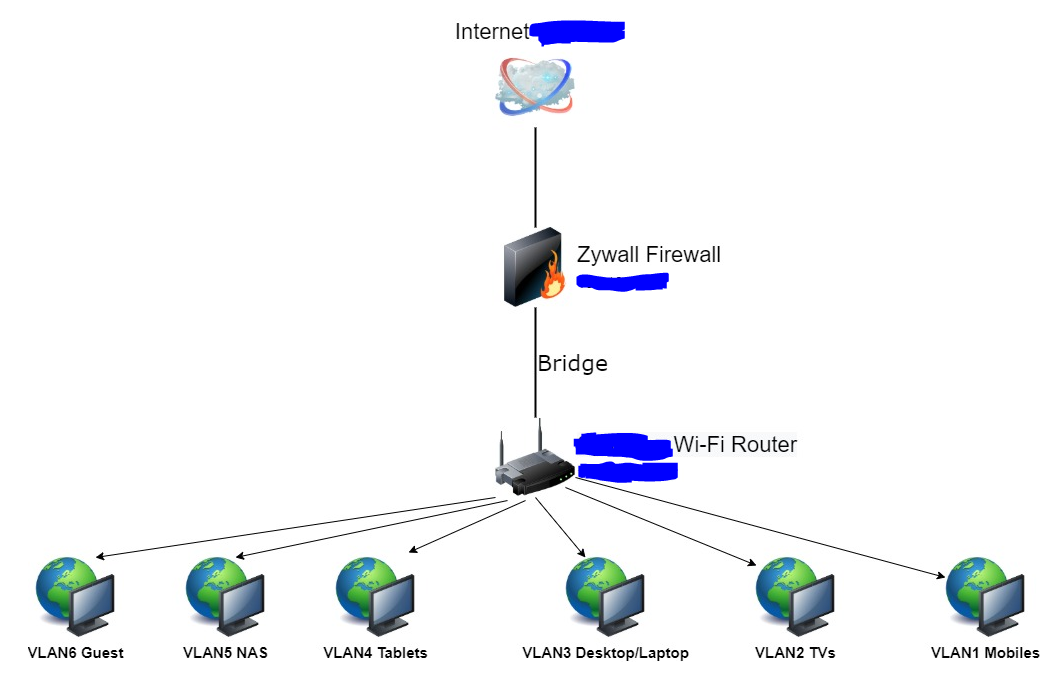
Before asking how and what I want to do, I attached the schema below:
The connection between my Wi-Fi Router and Zywall is in bridge with DHCP automatically, so all the IPs are coming from Firewall. Also, the Wi-Fi Router is in P4 LAN:
After I put the Wi-Fi Router in bridge, I create a VLAN with Interface internal, Zone LAN1 and Base port lan1. I assigned an IP from 192.168.x.x different than the one from LAN1 and also, a DHCP server. Please have a look below:
From what I understand from other discussions from the forum, this configuration must work.
Another thing what I did is to add VLAN1 in the same zone with LAN1
Also in Security Policy->Policy Control, it can be seen
May I know what I have to do ?
I'm asking because when I put manual the IP in my tablet from VLAN, it doesn't work.
Thank you,
Alex
Accepted Solution
-
The GS2210-8 will do.
I'm asking because from your message I saw that I have to create each VLAN in Zywall and in Switch as well.
Yes the Switch takes untagged devices or network/AP to be tagged to the Zywall VLAN ID interface gateway
5
All Replies
-
The way you think it works will not work as devices need to be tagged for the given VLAN as it is all your devices are untagged.
You will need much more equipment to do what you want.
0 -
Hello Peter,
So you think, I have to add also a Switch ? It doesn't work with Wi-Fi Router which I had ?
I'm asking because I have 2 devices on LAN via Wi-Fi Router and all the other devices are via Wi-Fi (mobiles, tablets, laptops, TVs).
Also, how do i tag my devices ?
0 -
Yes you need a VLAN Switch like this one
GS1920-24v2
So VLAN ID 1 should not be used for starting a VLAN setup or is used to Untag all ports on the Switch. Most devices can't be tagged so you need a VLAN Switch to take a Untagged devices to tagged to the VLAN ID.
Its also best to make a new Zone name for the VLAN like VLAN10 for the firewall rules to allow from VLAN10 to WAN instead of LAN1 to WAN.
Here is a setup with two VLAN's you can add AP that are untagged to give wireless.
0 -
Dear @PeterUK ,
Please correct to see if I understand correctly or not, from your previous message.
From what I saw regarding what you sent is a little bit unclear to me, who is each IP ?
I suppose:
- 192.168.1.1 is the IP from Zywall;
- 192.168.2.1 is the IP from Switch;
- 192.168.3.1 is the IP from Wi-Fi Router;
- 192.168.4.1 is the IP from Desktop
- 192.168.5.1 is the IP from NAS
If I put like this, how I will manage the VLANs for Tablets, Mobiles Phones, Laptops, TVs and Guest?
I'm asking because from your message I saw that I have to create each VLAN in Zywall and in Switch as well.
Thank you
Regards,
Alex
0 -
The GS2210-8 will do.
I'm asking because from your message I saw that I have to create each VLAN in Zywall and in Switch as well.
Yes the Switch takes untagged devices or network/AP to be tagged to the Zywall VLAN ID interface gateway
5 -
@zappu - I’m curious. Why are you segregating the network into 6 vlans?
Any network traffic that needs to go from a device in one Vlan to a device in another Vlan will need to go thru the router/firewall. That means if your laptop needs data from the NAS the traffic has to go from the NAS to the router and then to the PC. It will not go directly from the NAS to the PC.
I have a network with over 150 devices on it that makes use of many vlans but the vlans are set up for specific purposes and keeping network traffic separate. For example a management Vlan for switches, a security camera Vlan, a user device Vlan for laptops, desktops, tablets, and phones, and a guest Vlan.
Your vlans seem to be set up by device type (other than guest) rather than how the devices need to interact or how they should be isolated from each other.
0 -
Hi @zappu
You scenario should be supported by the Zywall 110. Is only VLAN 1 doesn't work or all the other VLANs don't work as well??
BTW, the switches Peter suggested is mainly to add the VLAN tag to let the Zywall 110 recognize it or there won't be any VLAN tagged packets pass to the Zywall 110 and the Zywall 110 can't separate different traffics from different area.
0
Categories
- All Categories
- 438 Beta Program
- 2.7K Nebula
- 188 Nebula Ideas
- 121 Nebula Status and Incidents
- 6.2K Security
- 454 USG FLEX H Series
- 303 Security Ideas
- 1.6K Switch
- 81 Switch Ideas
- 1.3K Wireless
- 44 Wireless Ideas
- 6.8K Consumer Product
- 278 Service & License
- 435 News and Release
- 88 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.2K FAQ
- 34 Documents
- 34 Nebula Monthly Express
- 85 About Community
- 91 Security Highlight
 Freshman Member
Freshman Member








 Guru Member
Guru Member



 Ally Member
Ally Member
 Zyxel Employee
Zyxel Employee




