[2021 Issue 04] See how Zyxel’s Secure WiFi enables employees to work from home in a secure manner
 Zyxel Employee
Zyxel Employee

Due to the pandemic, businesses now need to ensure their networks can be accessed securely outside of the office by their employees working remotely, while still providing the same level of corporate security. Here are the best practices from Zyxel, to help our customers to tackle these new challenges.
The best practice to duplicate that working experience from the office to the employee's home, is to extend the office network with a tunnel working at layer 2.
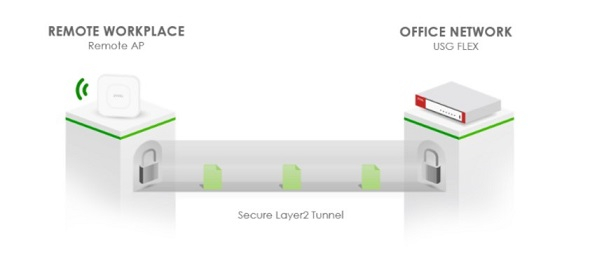
That means the device located at the employee's home will share the same IP address, connect to the same SSID as seen in the office, assigned to the designated VLAN, authenticated based on the credential provided, then conduct the required tasks accessing authorized applications, and even calling to other employees' desk phone. All these services can be provided over a wireless network so that IT could deliver the agile network infra to maintain the best productivity.
To
achieve the scenario above, the IT professional shall consider deploying a
company-owned Wireless Access Point, which can build a layer 2 tunnel to the
office network. Since the L2 tunnel traverses over the Internet, the tunnel
shall be encrypted with a strong cipher. The SSID shall be provisioned from IT,
hosting office SSID, and optionally another SSID for private use.
Provisioning both office SSID and also personal SSID for private use

Now you have built an agile network with layer two support delivering good productivity. But wait how about security?
Ask yourself these two questions:
(1) Is every endpoint (laptop/mobile) being used to access the office network is owned, issued, and managed by the company?
(2) Are all users, devices, and applications located in fixed locations, usually on a company network behind a firewall?
For most SMBs, the answers are "no" to both questions when they adapted to the work-from-home scenario.
Back in 2009, Forrester Research's John Kindervag had defined the principle for “Zero Trust” as “never trust, always verify.” In other words, always assume that every part of your network is potentially hostile, as if it were directly connected to the internet, and treat access requests accordingly. Threats that manage to bypass the firewall (through compromised user credentials or a vulnerable web-facing application, for example), or that start within the internal “trusted” network, should be stopped by extra security controls that prevent lateral movement and thereby minimize the impact of a security breach.
(1) Verify user identity: never granting trust by default to anyone attempting to access or process data. According to the Zero Trust security principle, every user connection attempt should be re-evaluated, identities should be strictly authenticated, and access should be granted after the entire context of connection is inspected. Consider deploying multi-factor authentication in the work-from-home scenario by adding an extra layer of security to verify the user identity. Since the endpoint connected from an untrusted location, an additional layer of verification is highly recommended. With the Zyxel solution, the Remote AP can be configured to enforce MFA with WPA2 Enterprise (802.1x), plus Google Authenticator to avoid the risk of identity theft.
SSID with 802.1X authentication will bind with Google Authenticator

(2) Once the user identity is confirmed, then follow the least privilege principle to authorize access privilege to appropriate resources. This can be achieved by network segmentation e.g., mapping to VLANs based on the role. The benefit to doing so is even when the endpoint is compromised, while IT could prevent the lateral movement of the security breach.
(3) Building device trust is another important factor, particularly those unattended devices e.g. IoT devices. With the MAC filter plus DPPSK (Dynamic Pre-Share Key), the IT could add strong two-factor authentication that could improve the visibility of those unattended IoT devices. Furthermore, do take a practical approach to minimize the attack surface through network segmentation. Traffic to and from devices should be highly restricted, allowing only the minimal communication required for proper functioning.
(4) Since the remote AP is building a full tunnel, where the endpoint's outgoing traffic will be all forwarded to the office network, then this network traffic could be inspected by the security fabric of the headquarters’ NGFW e.g., malware detection, reputation filters, intrusion prevention. The IT could also have full visibility about application usage e.g., type of applications and take it a step further to enforce the policy usage of a particular application by throttling or blocking the use of that application. All these could be provided by Zyxel's latest Nebula solution with the addition of the USG FLEX firewall and RAP.
(5) Some security breaches can go undetected for months. In fact, it typically takes an average of 280 days to identify and contain a breach, according to Ponemon Institute's "2018 Cost of Data Breach Study". To address this challenge following the Zero Trust security principle, the IT shall leverage a tool to improve visibility into their entire security posture, by continually logging, monitoring, correlating, and analyzing every networking event across the entire network. With Zyxel, we provide the renowned SecuReporter to give in-depth analytics of the security events, which enables IT to have full visibility about what's going on in the company network. Once the security breach is identified, the Nebula Control Center will automatically contain the threat at the network edge by collaborating with the RAP to block that endpoint or quarantine it to prevent it from involving in further lateral movement, to mitigate the risk effectively.
SecuReporter provides network administrators with centralized view of network activities

Leaving an office network means missing out on some basic security protections provided by the company's security products that run on corporate networks, many of them invisible to the employee. We would like to share best practice advice for all employees to keep devices and data secure when working from a location other than the office network.
First off, employees must consider the environment in which they are working. For many, "home" means working from a safe and secure location where they will not be overlooked and are at no immediate risk of having a device stolen or tampered with, but not every employee will enjoy this luxury.
Here comes 10 tips that will greatly help you improving security level:
(1) Those working in shared or public locations should lock their screens when not in use and always have physical possession of the device.
(2) A VPN should always be used when working from home.
(3) Do not allow family members or friends to access work devices for non-work tasks.
(4) Create and maintain strong passwords. Do not write down the password on a post-it.
(5) Always apply new security updates to operating systems and applications immediately!
(6) Update the security of other devices on the home network, such as the home router, with the latest firmware and always change the default password.
(7) Do not connect non-work USB drives to your work device.
(8) Do not transfer data from personal devices to work devices or vice versa.
(9) Use a headset to avoid having calls overheard.
(10) Know how to contact the company IT for advice in the case of anything suspicious.
The Nebula solution helps IT to deploy and maintain a distributed network infrastructure to service remote employees securely. Imagine you are about to deploy tens or even hundreds of Remote Access Points, is there an effective way to do so?
Well, it's time to talk about how Zyxel can help IT optimize the workflow and increase productivity when managing these distributed networks:
- Preconfigured without unboxing, with the template: IT could always use a template, to duplicate setting across all edge devices e.g. Remote Access Points. The best part is these could be solely done on Nebula Control Center, you do not have to do the configuration one after another. This greatly improves productivity.
- Plug-and-play: unbox the AP, plug in the Ethernet cable, power it up, and the AP will phone home automatically. Then the Nebula Control Center will do the rest for you: upgrade to the current firmware, push settings to the AP, and it will be up and running in minutes!
- Provisioning of network and security policy from a single platform. Within the same dashboard, IT could conduct provisioning of network devices and also security policies for enforcement points e.g. the RAP, and also the firewall.
In Zyxel, we aim to help SMB customers to deploy and maintain an effective distributed network while achieving the same security across all networks.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight