Best Practices to Secure a Distributed Network Infrastructure
 Zyxel Employee
Zyxel Employee



Best Practices to Secure a Distributed Network Infrastructure
In the post-pandemic era, more and more employees are forced to work
primarily from home, thus the way people get connected and the way people
accessing corporate resources has changed forever. Now that the network
perimeter is no longer fixed in the office, securing a distributed network
infrastructure to support a more fluid type of working has become a challenge
for IT professionals.
A fundamental way to enhance network infrastructure security is to safeguard networking devices with secure configurations. Administrators should implement the following recommendations to secure your network infrastructure
1. Secure setup for restricted remote management
- When possible, disable the access from HTTP, HTTPS, PING, SSH, SSL VPN, and TELNET services to your firewall
Default_Allow_WAN_To_ZyWALL and remove all unnecessary services

- Restrict access from trusted host
If you allow the remote access for Web management and SSL VPN service, Zyxel firewall auto scans your current device settings and returns security warning windows after login if the security risk found. To reduce the attack surface:
- Restrict access to trusted hosts/geolocations only. Change the service's
listening port to a non-standard port number

- Configure 2FA authentication for your administrative login will add extra layer of security Zyxel firewalls support 2FA for VPN connection and admin access. Here it is the tutorial about how to implement 2FA feature Case 1: 2FA for SSL VPN connection Case 2: 2FA for admin access
2. Privilege account control, monitoring, and alerts
- Keep monitoring all the user accounts on your device.
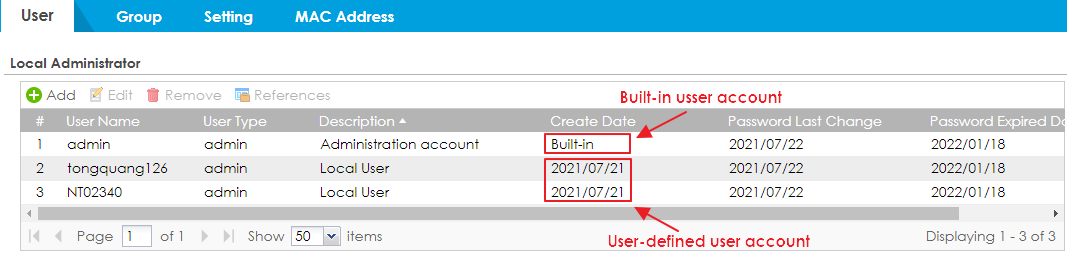
- Be aware of built-in and user-defined users account:
Built-in user
account: created by device helps you get access the device
(admin account) or
easily manage the external and guest users
(ad-users/ldap-users/radius-user/
ua-users). These users can’t be deleted.
User-defined user
account: created by device administrator, and can be
modified or deleted.
- Privileged accounts should be monitored and reviewed continuously in order
to identify outsiders leveraging stolen credentials. Remove unused and
unauthorized accounts, and limit the administrative account to as few people as
possible.
Zyxel device separates local administrator and other users (local user, external user, limited administrator) into two tables for simple privileged access management. With local administrator, you can setup and monitor the password expiration date.

- Detect the suspicious account by scanning the user name or create date. If you found any unknown account on your device, review and adjust your security settings to keep your network secure.

- Keep an eye on login user
Zyxel device provides the login users page helps administrator easily discovers information of the current login users, like username, IP address, access type, and physical location
-Monitor > System Status > Login Users

- Setup email alert for suspicious login activity
Zyxel device also supports to send email alert if user account changes or suspicious login activities are detected.
- Go to Configuration > Log & Report > Log Settings, configure mail server,
sender and recipient email address
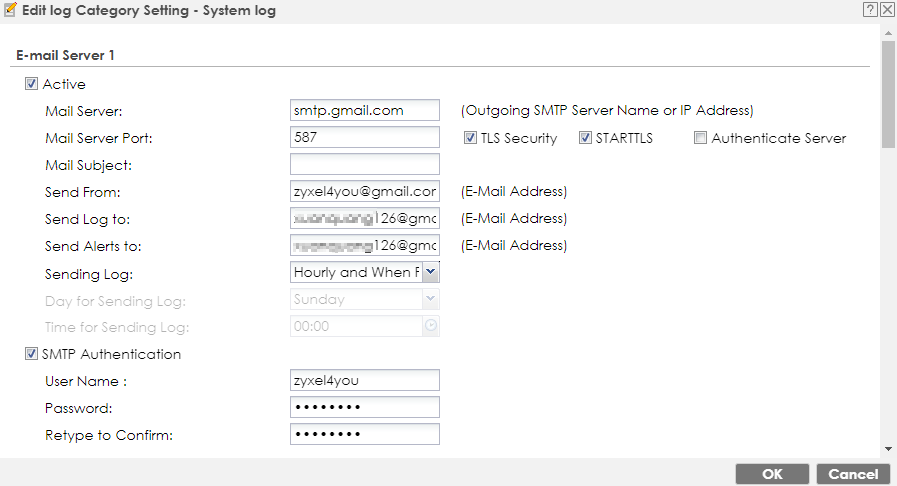
- Then enable alert for User log category

Here is an example of email alert device notifies user for a suspicious login activity

3. Periodical reminder for admin password change
It's
recommended to change administrator account passwords regularly. Not only
enforce local administrator to change their password periodically, but Zyxel
device also is able to check the new password must meet complexity requirements
- Configuration > Object > User/Group > Setting

Local administrator will get the notification about the last password change and expiration date when login

4. Firmware upgrade push and alert (patch, patch, patch)
An essential part of keeping your infrastructure safe from cyber threats is to ensure device firmware always up to date.
Zyxel device
shows notification icon on Web GUI once a new firmware is available. You can
click to the icon to read the new enhancements before deciding to upgrade
- Maintenance > File Manager > Firmware Management


5. Use Two-Factor Authentication (2FA)
2FA is an extra layer of security to the authentication process by making it harder for attackers to gain access your network, even if the victim's password is hacked. With 2FA, users must not only enter username/password but also submit the verification code to get the access. Zyxel devices provide 2FA for local administrator, local user and VPN access.
- Local administrator and users can select either Google Authenticator or
Email/SMS to retrieve their verification code
-Configuration > Object > User/Group > User
For administrator, you can apply 2FA for Web, SSH, and Telnet accesses
-Configuration > Object > Auth. Method > Two-factor Authentication
VPN users can get the authorized link URL with verification code via Email/SMS for SSL, IPSec, and L2TP/IPSec VPN accesses.
-Configuration > Object > Auth. Method > Two-factor Authentication

6. Back up the device configuration
We recommend that you schedule the device configuration backups for that period. With backups of the configuration file, you can quickly replace the functionality of a piece of network equipment after a failure.
Zyxel device offers fully automated configuration backup, it is able to send a backup of running configuration by mail at scheduled times. Device also can encrypt configuration file in a ZIP file with a user-defined password.
-Maintenance > File Manager > Configuration File > Schedule Backup

You also manually select specific configuration file to download or send
-Maintenance > File Manager > Configuration File > Configuration
7. Add Private Encryption Key for your Configuration File

Comments
-
@Zyxel_Jerry - can you explain why moving the policy to be the first rule will limit the attack surface? The policy still allows traffic from WAN to ZyWALL because the policy is to allow traffic, not deny.1
-
Yup, I think the WAN to ZyWALL, maybe that should be deny…all0
-
Hi @rookierunner
The first rule is for build-in VPN service. (e.g. IPSec VPN, L2TP VPN)
You can also make sure the group objects are not include HTTP/HTTPS in allows rules.
Then HTTP/HTTPS request traffic from WAN to ZyWALL will block by default rule.1 -
Thanks @Zyxel_Stanley! That makes sense. I think I am going to update the name of the service to “Default_Allow_VPN_From_WAN_To_ZyWALL” to make it more clear about what that service allows.
Also, if I only use the L2TP VPN, can I disable the default “SSL_VPN_to_Device” rule (#12 in your picture above) and the default “TUNNEL_to_Device” rule (#13 in your picture above)?
0 -
Hi @ rookierunner
“SSL_VPN_to_Device” and “TUNNEL_to_Device” are configurations for SSL VPN and VPN tunnel traffic.
After creating VPN rules, then system will join the VPN tunnels as zone member automatically.
You can move your mouse to the zone and make sure if there is any member exist in drop-down list.
If not, you can inactivate the rule from your policy control rule.

0
Categories
- All Categories
- 435 Beta Program
- 2.7K Nebula
- 176 Nebula Ideas
- 118 Nebula Status and Incidents
- 6.1K Security
- 428 USG FLEX H Series
- 298 Security Ideas
- 1.6K Switch
- 79 Switch Ideas
- 1.2K Wireless
- 44 Wireless Ideas
- 6.7K Consumer Product
- 274 Service & License
- 422 News and Release
- 88 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.2K FAQ
- 34 Documents
- 34 Nebula Monthly Express
- 83 About Community
- 89 Security Highlight
 Freshman Member
Freshman Member




