How to Configure Remote Access VPN Authentication with My AD Server on NSG?
 Zyxel Employee
Zyxel Employee



Background
Use AD server to authenticate VPN users.
Scenario and Topology
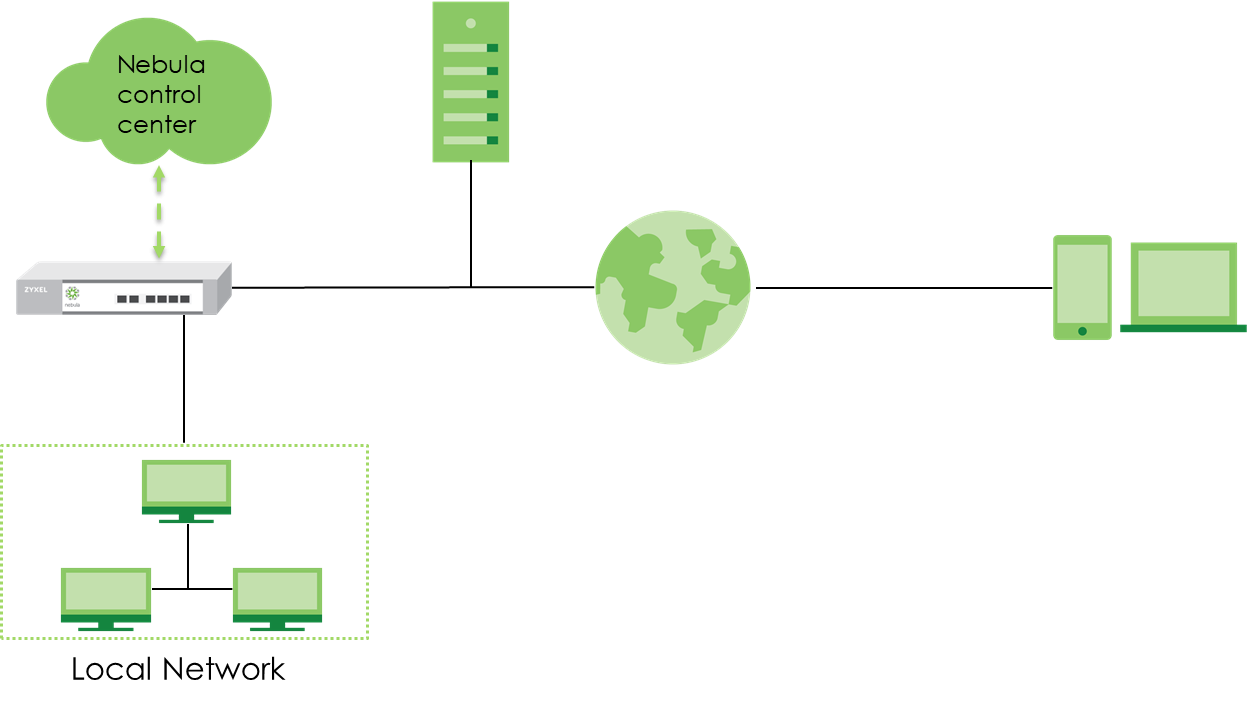
Nebula Cloud Solution provides the option to let users establish L2TP over IPSec VPN/ IPSec VPN and authenticate with My Active Directory (AD) Server.
This topic will configure L2TP over IPSec VPN as the example.
Configuration
We use Windows Server 2019 Data Center as the AD server.
1 Pre-requisites
You need to install Active Directory Domain Service on your server, and then upgrade it to Domain Controller. A Bridged Network Adapter must be connected directly to the physical network.
2 Configure My authentication server
Go to “Gateway > Configure > My authentication server” to type Name and your server IP address. The default port is 389. Type your domain name (such as DomainName.com), and your Domain admin account and password.

3 Configure L2TP over IPSec client
Go to Security Gateway > Configure > Remote access VPN > L2TP over IPSec client and switch ON with Client VPN server. Type Client VPN subnet, such as 192.168.199.0/24. Select Use Google Public DNS as your DNS name servers. And then type your Secret which is same as your secret on your clients. Finally, select your AD server name as Authentication from drop-down list.

4 Configure the L2TP VPN Tunnel on the smart phone
Go to “Setting > Wi-Fi & Network > VPN” to click “︙” add VPN profile.
Type the name of your L2TP VPN profile.
Select type to L2TP/IPSec PSK.
Type your VPN Server IP address (NSG WAN1 IP).
Type your secret which is same as NCC in the IPSec pre-shared key field.
Type account info, including username and password

5 Configure the L2TP VPN Tunnel on the Windows PC
Go to “Setting > Network & Internet > VPN > Add a VPN connection” to add a new VPN connection.
Select VPN provider to Windows.
Type the connection name.
Type your VPN Server IP address (NSG WAN1 IP).
Select VPN type to L2TP/IPsec with pre-shared key.
Type your secret which is same as NCC to Pre-shared key.
Select type of sign-in info to User name and password and type account info.
After setup, please go to Control Panel > Network and Sharing Center, and click Change adapter settings.
Right click your VPN connectio, and select Properties.
Click Security, select Layer 2 Tunneling Protocol with IPSec (L2TP/IPSec) in Type of VPN drop-down list, and check Unencrypted password (PAP) checkbox.


Verification
Smart phone: Android:
Connect the VPN.

PC: Windows 10
Go to “Setting > Network & Internet > VPN” to connect the VPN (you need to type your AD user account, including username and password, if you skipped this in previous you setup).

Note
1. Please make sure the VPN setting are correct before connecting to the VPN.
2. If Windows VPN setting didn’t set Unencrypted password (PAP) in Security section, the VPN connection will fail.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 591 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 478 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight