How to route multiple public static IPs with Zyxel
How to route multiple public IPs to devices behind a Zyxel router, where the device behind the Zyxel holds a public IP. Typically this method is used when routers are connected behind the Zywall.
Method 1: Use this method to provide "no NAT" to the device behind the Zyxel. This method only works when their is a router in front of the Zyxel so that both the Zyxel and the device behind the Zyxel can use the same gateway.
*Go to Network>Interface>Bridge
*Set Interface type to: external
*Interface name: br1
*Zone: WAN
*Members: WAN1,dmz
*Go to Network>Interface>Trunk and create a new Trunk Group with "br1" as the primary member
*Go to Object>Address and add a host for each usable public static IP
*If the device behind the Zyxel is a router, Go to Security Policy > Session Control and disable the session limits
*Configure the device behind the Zyxel with a usable public static IP and point it to the same gateway that Zyxel is using.
*Plug device behind the Zyxel into a DMZ port.
*Add a route in the Zyxel that states: Incoming > Interface: DMZ > Source Address: Object_Address_PublicIP > Destination: Any > Next hop: Interface br1 > SNAT: Object_Address_PublicIP
Method 2 is the same as method 1 but where a modem is in front of the Zyxel instead of a router. In this case the Zyxel has to act as a gateway for both itself and the devices behind it.
*Go to Network>Interface>Bridge
*Set Interface type to: external
*Interface name: br1
*Zone: WAN
*Members: WAN1,dmz
*Set the IP to automatic if the Public static is obtained via DHCP (note that the mac address used
will not be the MAC of WAN1 even when interface WAN1 is used)
*Go to Network>Interface>Bridge and click on "Create Virtual Interface">Enter the first usable public
IP address and subnet mask and leave gateway blank
*Go to Network>Interface>Trunk and create a new Trunk Group with "br1" as the primary member
Then set the new Trunk Group as the system default trunk
*Go to Network>Interface>port role and set one of the ports as a DMZ
*Plug in a device or switch into the DMZ port and enter the second usable public IP into the device and set the Virtual Interface IP as the gateway
*Make sure the firewall is set say that any to DMZ and DMZ to any is allow.
*Go to network Zones and make sure that interzone blocking for both WAN and DMZ is set to "no"
*The router is now running in dual mode. LAN1 is NAT and DMZ is no NAT
In cases where the devices behind the Zyxel hold private IPs because they required firewall protection. Typically this method is used when servers are connected behind the Zyxel.
Method 1 is 1:1 NAT and is used if firewall functionality is desired. This method only works when their is a router in front of the Zyxel so that both the Zyxel and the device behind the Zyxel can use the same gateway.
*Go to Object>Address and add a host for each public static IP
*Go to NAT and add a rule that says: 1:1 NAT Type>Interface WAN1>Orginal IP=Public address>Mapped IP=private IP of device
Method 2: is the same as method 1 but where a modem is in front of the Zyxel instead of a router. In this case the Zyxel has to act as a gateway for both itself and the devices behind it for the second block of IPs.
* Have the cable provider bind the MAC address of the WAN to the public static IP they provide.
* Have the cable provider route the second block of IPs to the public static held by Zyxel WAN
* Add a virtual interface to the WAN and assign it the first usable IP of the second IP block. Example if the carrier provides a block of 1.2.3.88/29, then the virtual interface would be 1.2.3.89 255.255.255.248 (leave the gateway blank)
* Go to Network > Object Address and add an Address Host Object for each remaining Public IP address of the 2nd block
* Also add Host Objects for each device behind the Zyxel that you will be NATing public IPs to
* Go got Network > Routing and add a route for each device behind the Zyxel and the public IP it supposed to route out on: Incoming = LAN1 > Source=DeviceBehindZyxel > Destination=any > Service=any > NextHop=WAN (don't use the virtual interface) > SNAT=One of the Public IPs
The check box to "use Policy route to override Direct Route can stay "off"
* Go to Security Policy > Policy Control > From=WAN > To=LAN1 > Source=any > Destination=device behind zyxel > Service=define the service > allow
* Go to Network > NAT > classification=1:1NAT > Incoming=WANinterface > Original IP=The public IP being NATed to the device > Mapped IP=device behind zyxel > Service=define the service > Loopback="off"
Comments
-
Hi, is there any way to make this work if you only have one subnet of public static IP? In my case I have the router on x.x.x.9, the zyxel on .10 and have to use .11 on the DMZ device (no-NAT Webb application). The ISP have given me a total of 5 usable static IP.
0 -
Which model are you used in your environment?
Can you explain your network topology?
0 -
A single block of 5 should be fine. If you want to assign a public static to .9, .10, .11 respectively, then follow these steps:In cases where the devices behind the Zyxel hold private IPs because they required firewall protection. Typically this method is used when servers are connected behind the Zyxel.
Method 1 is 1:1 NAT and is used if firewall functionality is desired. This method only works when their is a router in front of the Zyxel so that both the Zyxel and the device behind the Zyxel can use the same gateway.
*Go to Object>Address and add a host for each public static IP
*Go to NAT and add a rule that says: 1:1 NAT Type>Interface WAN1>Orginal IP=Public address>Mapped IP=private IP of device
0 -
Thanks for sharing. I have 5 static IP's routed from ATT Modem / Router to a USG60. It required a setting in the ATT modem and bridging via a private subnet. To be honest I didn't document it, but glad it works.0
-
Hey @iSpeed do you mind explaining a bit more. You seem to have figured out what I need as well.1
-
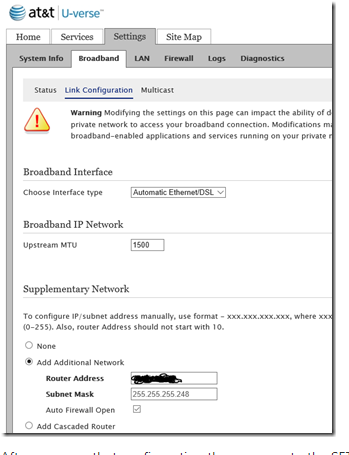
You want to use the Cascaded Router option on the ATT Modem. Then on the Zyxel create objects for your static ip's. Use those objects in your NAT rules.
To use this static IP block behind your router with the Cascaded Router option:
(Assume your router's WAN port is directly connected to the U-Verse Gateway, and currently has the address 192.168.1.10 on the WAN port).
Network Address: 99.99.99.16
Subnet Mask: 255.255.255.248
Router Address: 192.168.1.10
Now addresses 99.99.99.17, .18, .19, .20, .21, .22 are available for use on the LAN side of your router. (Your router must be able to route these addresses, so in all likelihood, one of them must be used on your router's LAN port.)
Below see the very bottom cascaded router. Check that and follow above.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Freshman Member
Freshman Member


 Zyxel Employee
Zyxel Employee



 Ally Member
Ally Member