Zywall 110 IPSec site to site VPN Not working
Options
trying to do a SSL Site to Site VPN to pass a temporary syslog.
i have tried the built in guides and guides on youtube and internet from Zyxel to set it up.
- Each site have the oposit sites IP adress.
- The LAN subnets are different.
- Encryption is set same on both sites.
- same password. (ruled out incompatable passwords bu useing just 123456789 for test)
- firewall rules are in place on both sites, (firewalls are factory default exept VPN and WAN interface settings)
Site 1 have static IP
Site 2 have dynamic ip but a public facing one.
i did try to do a packet capture while i do try to connect from the other site and i do not get any trafic at all from that IP.
Any good ideas or questions so i can try to se what i have missed?
*Pictures from one of the sites, the other one is the same but with the other IP adresses of cource. 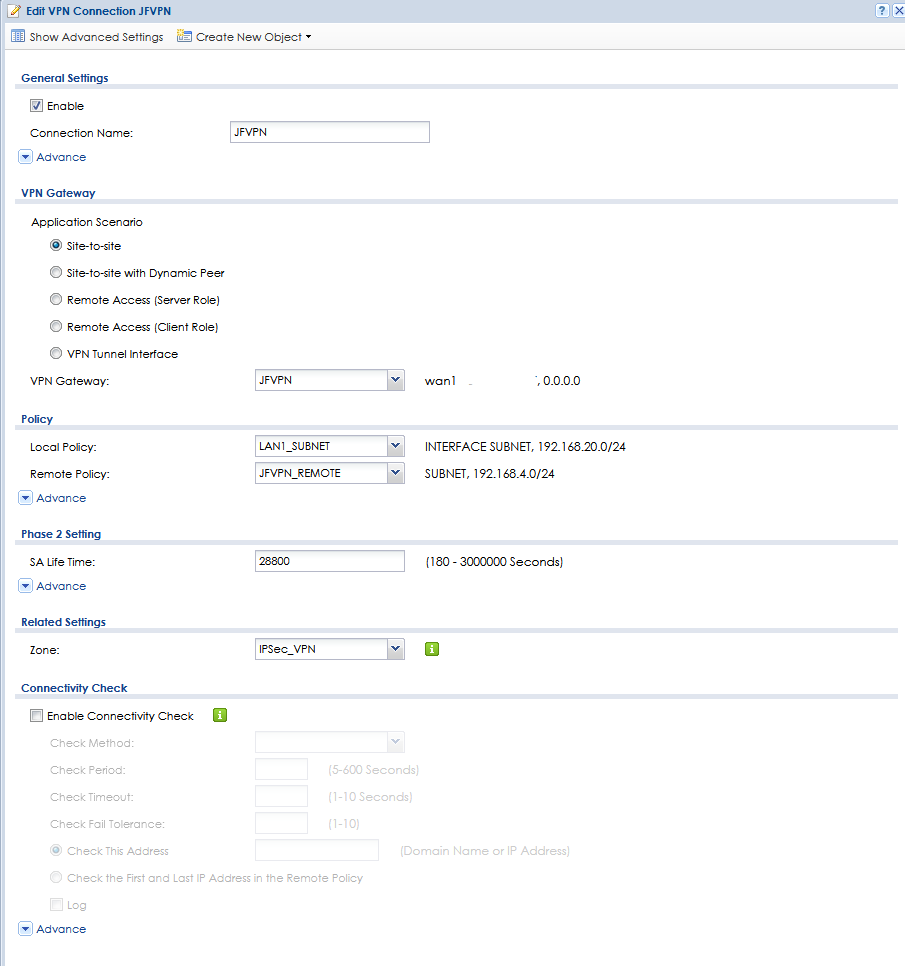
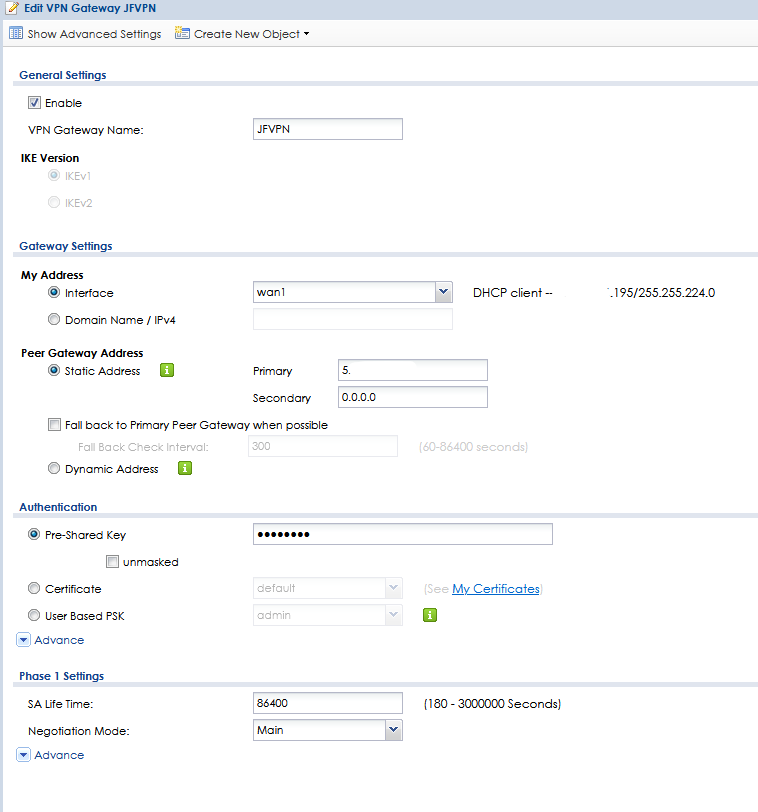
0
All Replies
-
This is my small experience...
For both sites: any firewall with private IP configured on WAN interface must have enabled NAT-Traversal; strongly suggested to enable DPD (Ipsec V1).
Site1: if the WAN on the zywall is configured with private address (as the previous suggestion), ports 500 UDP and 4500 UDP must be forwarded to the Zywall from your ISP router.
The gateway must be set as "Dynamic Address" under Peer Gateway address. This change can lead to the negotiation to aggressive. Also, lower the SA time than 28800, in case of address change the rebuild of the tunnel could take up to 28800 seconds, or less (depending on the last time tunnel was built).
In the VPN connection, it's advisable to set the connection not Nailed up; the scenario must be Site to site with a dynamic peer, and the gateway should be populated again with the new VPN gateway setting.
Site2: as site1, ports 500 and 4500 forwarded are a thing that I'd do (assuming that the address on Site2 connection is pubblic and not ISP-level natted.
For gateway, match the SA time and the negotiation (cipher included) match the gateway on site 1.
Set the VPN connection as Nailed-Up. Site2 will initiate the connection any time it's on.
Connection is fine as "site to site"
1 -
(●) Site-to-site with Dynamic Peer was my initial thought as well. mMontana's post above is very good, I do not have anything to add.
0 -
will try this, though there is no ISP routers or modems at all so that is not a problem.
0 -
Hmm does not work. i´l try to sum up:
No ISP routers or modems on any site.
Site one:
IP = Static
VPN type = "Site to site with dynamic peer
Auth = preshared key
SA Life = 28800
Negotiation = Agressive
Encryption = AES128 and SHA1
Nat traversal = onDPD = onon connection:
Naild-Up = off
Site two:
IP = Dynamic but public facing
VPN Type = site to site (static adress of site one as primary adress)
Auth = preshared key
SA Life = 28800
Negotiation = Agressive
Encryption = AES128 and SHA1
Nat traversal = onDPD = onon connection:Nailed-Up = onDid try to get all the settings in two pictures below,

0 -
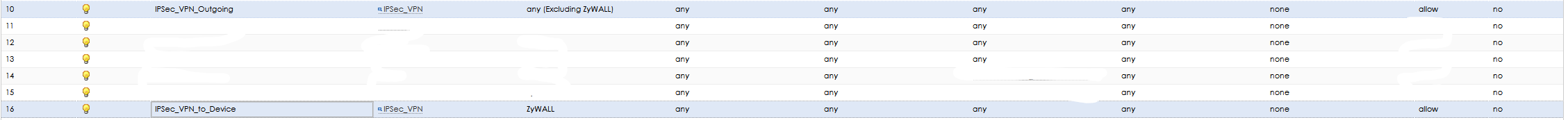
On both sites, please activate "enable replay detection" into VPN Connection.Please, answer this question: WAN interfaces on site1 and site2 have public ip address configured or a private ip address configured (like 192.168.x.y or 172.16-31.x.y or 10.x.y.z)?Into security policies, the policy WAN to Zywall allow traffic for port 500 and 4500 UDP?After checking these boxes, time to go on log for understand what's goin' on.0
-
done, but still not working.
Yes there are public IP adresses on the WAN interface on both sites.
0 -
Rules can be simplified using Service groups, reducing the load for the firewall with one rule instead of two.Now it's time to dig into the logs.0
-
Hi @NilsG
In default setting, there is a rule from WAN to ZyWALL to allow VPN service.
You can move the rule as 1st priority, prevent VPN connection effect by other rules.
Also, you can click "Connect" button in VPN connection page to trigger VPN tunenl.
If VPN tunnel connect fail, you can take screenshot of all "IKE" log entries to us for further check the reason. (Monitor > Log) 0
0
Categories
- All Categories
- 441 Beta Program
- 2.9K Nebula
- 208 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 533 USG FLEX H Series
- 334 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 461 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 86 About Community
- 99 Security Highlight
 Freshman Member
Freshman Member Guru Member
Guru Member



 Master Member
Master Member



 Zyxel Employee
Zyxel Employee




