[2022 Issue 16] Zyxel Threat Intelligence (Release Date: 2022-11)
 Zyxel Employee
Zyxel Employee


ZyWALLs latest virus/malware signature update protect you against more malware and threats. See how ZyWALL defends against these threats.
Part 1 – Virus/Malware Spotlight
Part 2 – Intrusion Detection Highlight
Part 3 – Application Patrol Highlight
This article focuses on Trojan.BitCoinMiner. Part 2 and 3 will be included in the November Monthly Threat Report covering Intrusion Detection and Application Patrol update. You can view more about their details, history, and signature information in Zyxel Encyclopedia.
(Number of updated Virus/Malware signatures:18,543)
Zyxel keeps malware detection up-to-date. Currently, Zyxel detects and removes the threats including Trojan.BitCoinMiner.
Highlight (partial)
Name: Trojan.BitCoinMiner
Description:
Trojan.BitCoinMiner identifies a program that the attackers wrote viruses to hijack other people computer's physical resources including memory and processing power. Crypto-mining typically is used with extremely powerful hardware costing a lot of money. To avoid this, Trojan.Bitcoinminer will silently installs through fake software downloads and updates, forcing regular users' computers to mine bitcoins or other digital cryptocurrency for them. Programs identified as Trojan.BitCoinMiners can either function as a miner, or install a separate component that can do so.
What Is Cryptocurrency?
A cryptocurrency is a anonymous and digital currency produced by a public network, rather than any government, that uses cryptography to make sure payments are sent and received safely. Multiple cryptocurrencies exist, such as BitCoin, Ethereum and Monero.
(Cover Total: 5543)
Modified signatures Highlight
CVE-2008-4841
Microsoft WordPad Word 97 text converter XST buffer overflow
The WordPad Text Converter for Word 97 files in Microsoft Windows 2000 SP4, XP SP2, and Server 2003 SP1 and SP2 allows remote attackers to execute arbitrary code via a crafted (1) .doc, (2) .wri, or (3) .rtf Word 97 file that triggers memory corruption, as exploited in the wild in December 2008. NOTE: As of 20081210, it is unclear whether this vulnerability is related to a WordPad issue disclosed on 20080925 with a 2008-crash.doc.rar example, but there are insufficient details to be sure. (Source: NIST)
CVE-2020-26878
ZuoRAT MALWARE-CNC
Ruckus through 1.5.1.0.21 is affected by remote command injection. An authenticated user can submit a query to the API (/service/v1/createUser endpoint), injecting arbitrary commands that will be executed as root user via web.py. (Source: NIST)
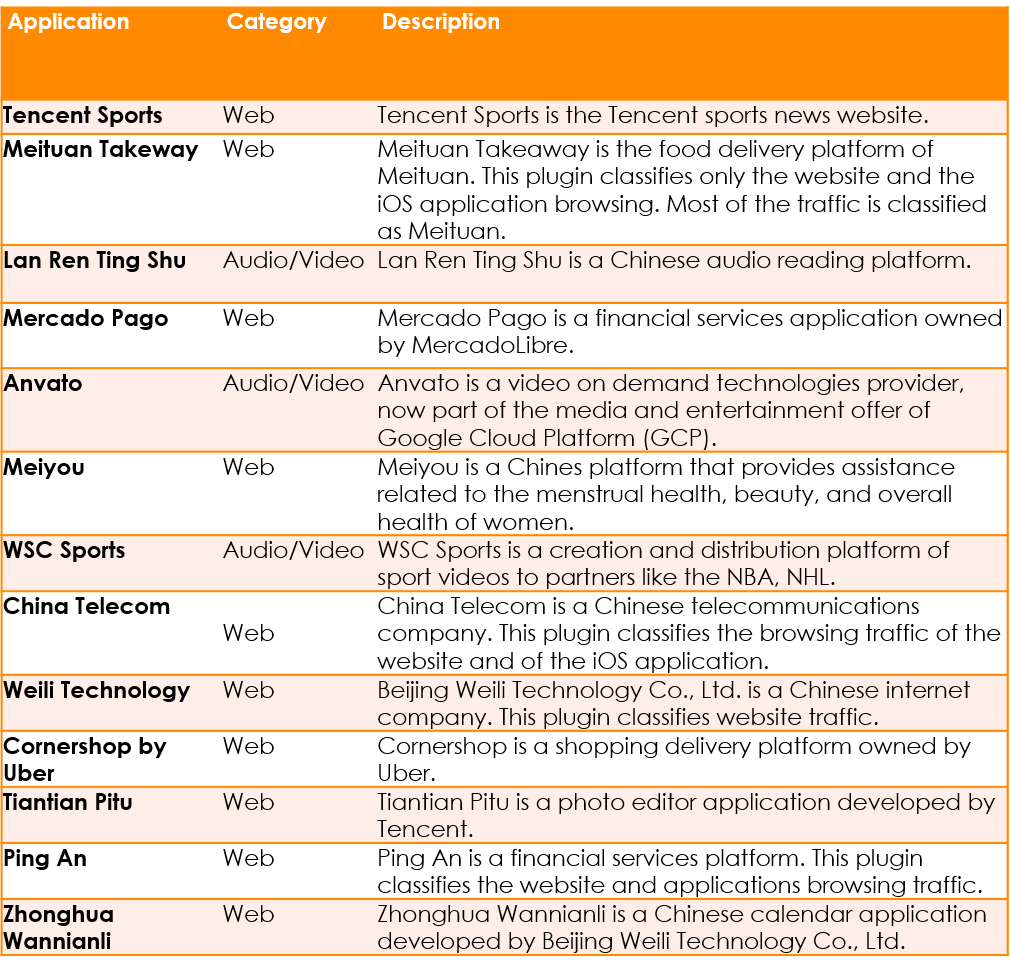
(Cover Total: All Application: 3956; Added Application: 13)
To make your life easier in managing your licenses for your devices, the Marketplace has been opened to buy licenses conveniently and securely.
These
are the three major benefits for you as a customer when using the
Marketplace:
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 585 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 297 Service & License
- 476 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight