How to capture IPS packets for false positive analyzing?
 Zyxel Employee
Zyxel Employee



Scenario
IPS false positive occurs when the IPS detects an activity as malicious, which is identified mistakenly as an attack. Sometimes it would have negative impact for business. If we would like to report false positive event/ID to Zyxel support, we need to provide related information/log for analyzing. This demonstration illustrates how to capture IPS packets for false positive analyzing.
Demonstration
Before we perform packet capture on firewall, please update to the latest IPS signature version.
Click “IPS update” at CONFIGURATION > Signature Update > Signature.

Make sure it is the latest version, and click “ok”.

In this demonstration, we download eicar file from a LAN host (ID:112012).
Step 1. SSH to firewall, and type following CLI to enable IPS packet capture for signature ID 112012.
Router# idp packet-capture enable
Router# idp packet-capture select enable
Router# idp packet-capture select add-id 112012
Step 2. Reproduce the issue by running the same application/software in LAN host.
In this lab test, we download eicar file in a Linux host by CLI
wget http://www.csm-testcenter.org/cgi-bin/eicar.com
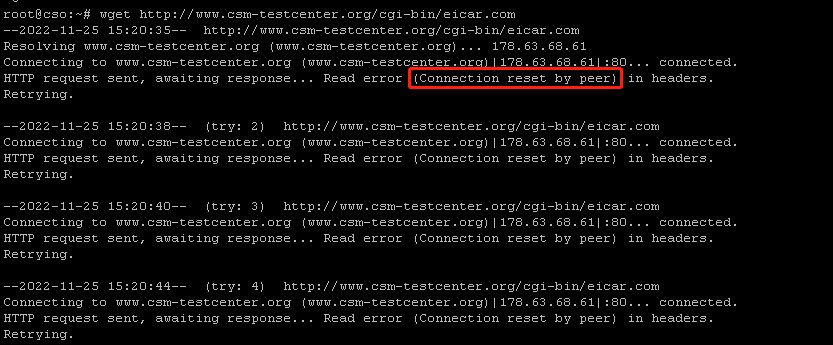
As we can see, it is failure to download eicar file. Session was reset by IPS module.
Step 3. Make sure if application/software is blocked by IPS signature ID 112012.
Go to MONITOR > Log > View Log to see if it has IPS blocked log.

Step 4. Download packet files and match rule list file.
Go to Diagnostics > Packet Capture > Files and download those "zyidp" files

Step 5. Remove signature ID 112012, and disable IPS packet capture.
Router> idp packet-capture disable
Router> idp packet-capture select del-id 112012
Router> idp packet-capture select disable
We can check status by CLI below to see if it is disable.
Router> idp packet-capture show status

After actions above are completed, please provide following information to Zyxel for false positive analyzing.
1. Firmware version
2. IPS signature version
3. Packet trace files and match rule list
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 128 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight