Site to Site VPN Communication Issue - USG60 to Azure VNet
Options
LukeRodgers
Posts: 3  Freshman Member
Freshman Member


 Freshman Member
Freshman Member

in Security
 Good afternoon,
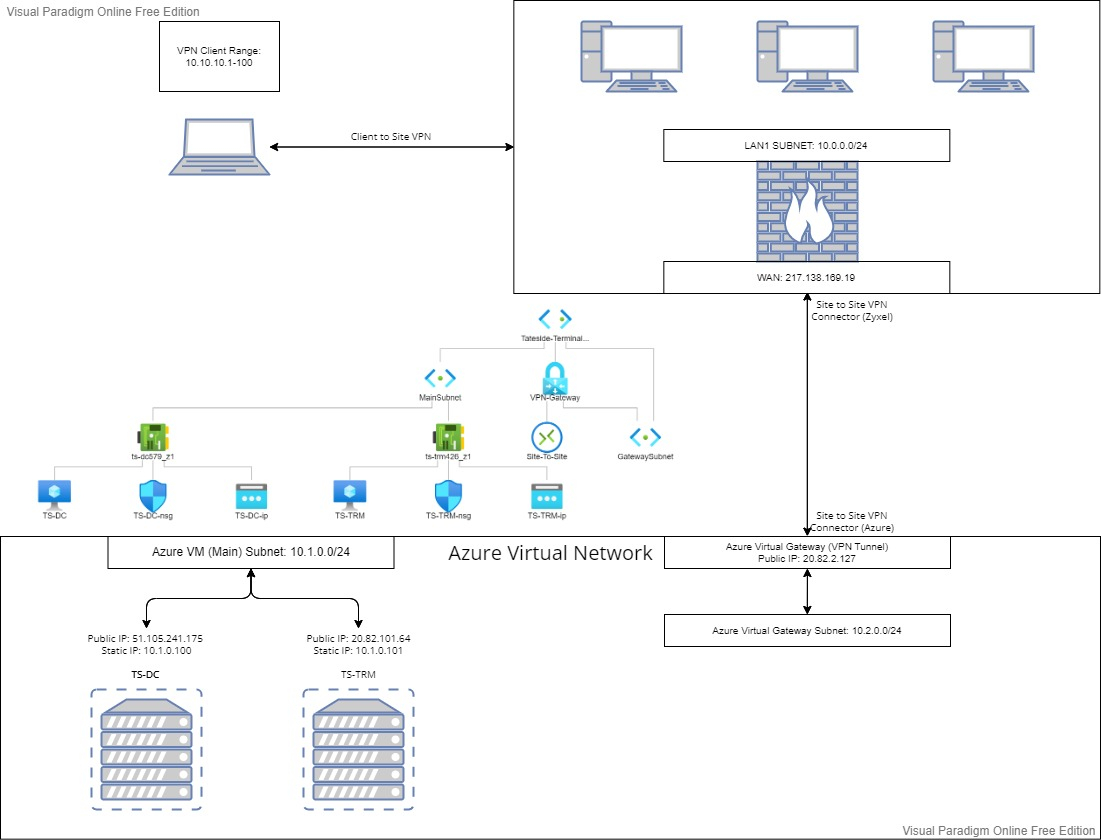
Good afternoon,We have a new Azure virtual environment set up, using two subnets, 10.2.0.0/24 and 10.1.0.0/24. The former is used by the Virtual Gateway, and the latter is the main subnet used by our two Virtual Machines.
We have set up a site-to-site VPN between the Azure virtual environment and our Zyxel USG60 firewall. The VPN connectors on both side say they are successfully connected, and when using PSTools and PSPinging the Azure VM (10.1.0.101), we get a response, as it uses TCP port. However upon using the ping command and trying to RDP onto it, we get no response at all when doing so from our office LAN 10.0.0.0/24.
This may be a routing issue, so I have followed multiple guides on setting up our routes on the firewall, but to no avail.
Any advise would be great.
To summarise: Need to be able to RDP from our office LAN, 10.0.0.0/24, onto the Azure VM 10.1.0.101. However the Public IP address is reachable.
0
All Replies
-
PS: Please ignore VPN client range, it is now 10.5.0.0/240
-
Hi @LukeRodgers,
Welcome to Zyxel community.
You can verify Network Security Group (NSG) configuration on the Azure side, to make sure that RDP traffic and ICMP are allowed from your office LAN IP range or ensure that the appropriate ports are open and forwarded to Azure network.0 -
Hi,Zyxel_Cooldia said:Hi @LukeRodgers,
Welcome to Zyxel community.
You can verify Network Security Group (NSG) configuration on the Azure side, to make sure that RDP traffic and ICMP are allowed from your office LAN IP range or ensure that the appropriate ports are open and forwarded to Azure network.
We have opened RDP ports and ICMP protocol on our Azure VM's NSG, meaning they should be accessible from our Firewall. However, upon attempting a connection from our Office site (Where our Firewall is, site 1 of the site to site VPN), via the Azure VM's static IP, 10.1.0.101, we are still unable to get a response.
0 -
To trouble shoot the packets between VPN tunnel.
1. On USG, using CLI to monitor packet in/out the IPSec VTI tunnel.
# packet-trace interface <VTI tunnel interface> ip-proto icmp
2. ping 10.1.0.101 from host in your office.
3. Check the packet monitor.
If you get ping request to 10.1.0.101 -> USG do sent the ping to Azure VM via the VPN tunnel.
If you didn't get the ping reply. Then go for Azure Virtual Network Gateway packet capture.
Prerequisites:
The captured packets can only store to Azure blob. So you need to prepare it before doing the capture.
(1) Create a storage account
https://learn.microsoft.com/en-us/azure/storage/common/storage-account-create?tabs=azure-portal#create-a-storage-account-1
(2) Create a blob container
https://learn.microsoft.com/en-us/azure/storage/blobs/quickstart-storage-explorer
(3) Generate and get the SAS URL of the container. (permission select: read/write/list) https://www.youtube.com/watch?v=4yn9wS6Q9zw, at 5m04s ~
https://www.youtube.com/watch?v=4yn9wS6Q9zw, at 5m04s ~
1. Packet Capture on the VPN connection
(1) On Azure Portal, open the VPN connection under the Virtual Network Gateway.
(2) In the left hand side menu, under Support + Troubleshooting section. Go to VPN Connection Packet Capture.
(3) Click Start Packet Capture. In the right hand side filter setting, change protocol to 1 (icmp).
Then scroll down to click Start Packet Capture button.
2. Doing ping test from your office to 10.1.0.101
3. After ping test finish. Click Stop Packet Capture. On the right hand side fill-in the SAS URL of your blob container. Then click on the Stop Packet Capture Button.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Zyxel Employee
Zyxel Employee



 Master Member
Master Member




