GS1900 - separate 2 ports from the rest (aka splitting a physical switch into 2 logical ones)
Hi, I have a GS190024HPv2 switch in a simple configuration - not using any VLANs and using it as a plain switch with PoE turned on some ports.
I have an optical-to-metallic media converter from my ISP which I'd like to power via PoE from the GS1900v2. However, I'd like to separate the signal from the ISP (WAN traffic) from local LAN traffic.
In other words, I'd like to connect the ISP converter to port A and set its traffic to route only (and only!) to port B (and vice-versa). I'd then connect my firewall to port B.
Can this be done without doing VLAN tagging (perhaps by using some other feature of the GS1900v2)?
If not, can someone please provide me with the simplest and minimalistic configuration on how to achieve this using VLAN tagging?
Thank you very much.
Regards,
Marko
All Replies
-
VLAN unfortunately is not “simple”. I mean, after understand that, it becomes simpler. But few concepts must be known:
1: For use tagged vLANs, all devices must be vLAN-tagging-aware. And properly configured
2: You can have only one untagged vLAN par-port
3: If you connect any device without configuration on a port with 4 tagged vLANS and an untagged vLAN, it's like connecting it only to the untagged vLAN.
4: tag is a port-based configuration: so any vLAN could be untagged somewere (aka on some ports) and tagged somewhere else (aka on some other ports)
5: on a single port, a single vLAN is either tagged or untagged. You can't have both.Assuming that the current vLAN is numbered 1, and named “default” and the new vLAN should be numbered 12 and named “ISP”
0: save configuration, backup on your computer, upgrade the firmware of your switch and reboot it
1: choose the ports for “the other” vLAN (example, 1 and 2)
2: unplug all devices on that ports
3: create a new vLAN (from now, ISP_vLAN)
4: on VLAN Port section, with vLAN 1 (Default) selected, set port 1 and 2 as “Excluded”. Click Apply
5: on VLAN Port section, switch to vLAN 12 (ISP) set port 1 and 2 as “Untagged”. Click Apply
6: save configuration on your switch!Test connecting a laptop on port 1. Should not be capable to receive any configuration from your LAN, nor if manually configured being able to reach any kind of the device on vLAN 1
IMVHO… a 2-untagged ports vLAN is a bit strange. Am I correct supposing that you're trying to consolidate your PoE devices on the GS1900-8HP?
0 -
Thanks for the instructions.
Currently I have:
- GS1900 switch with only LAN devices connected (not using VLANs)
- Modem from ISP connected to firewall (via a PoE injector)
I want to get rid of the PoE injector:
- GS1900 switch with LAN devices connected (ports 3-24)
- Modem from ISP connected to port 1 (powered via PoE)
- Firewall connected to port 2
Traffic should flow between ports 3-24 and ports 1-2. No traffic should flow between these two groups/VLANs.
All ingress and egress traffic coming to/from the switch should not be VLAN-tagged. In other words, VLAN-tagging should be only done “inside” the switch in order to separate ports.
PS: So you are saying that if I turn on port-based VLANs, then all ports must belong to a VLAN? Should I use VLAN 1 for the LAN segment? Or is VLAN 1 a special VLAN? How do I achieve that traffic leaving the switch gets stripped of the VLAN tag?
0 -
Hi @MarkoD,
Since the GS1900 only supports IEEE 802.1Q VLAN tagging, here's the recommended configuration for your scenario:
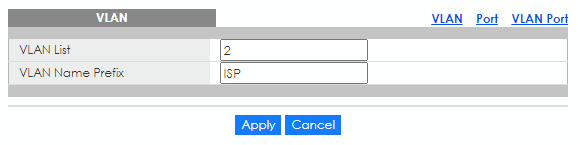
- Add VLAN 2 in Menu > Configuration > VLAN > VLAN.
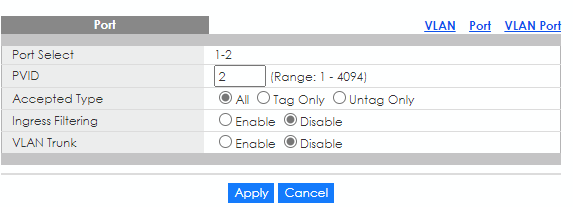
- Go to Menu > Configuration > VLAN > VLAN > Port page to edit port 1&2's settings. Change the PVID from 1 to 2.
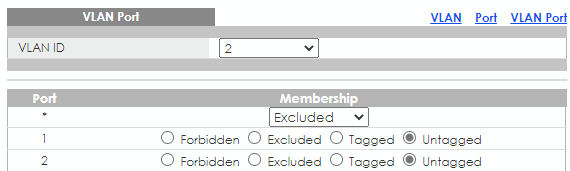
- Go to Menu > Configuration > VLAN > VLAN > VLAN Port page to configure the VLAN port member.
- Port 1&2 set as Forbidden in VLAN 1.
- Port 1&2 set as Untagged in VLAN 2.
Hope this helps.
Zyxel Melen0 -
Dear @Zyxel_Melen,
Thank you for the step-by-step instruction. I have some follow-up questions:
Step 3: Shouldn't I also set ports 3-24 as "Forbidden" for VLAN 2?
Also, what's the difference between"Forbidden"and"Excluded"? I haven't found any info in the manual…(EDIT: I've found that it has to do with protocols such as GVRP; which can dynamically reassign a port's membership if Excluded and not Forbidden)Ingress Filtering: What does this do? I found this in the manual: "Switch discards incoming frames for VLANs that do not include this port in its member set." How is this different than setting the port as "Forbidden"?
Thank you very much,
Marko
0 -
Hi @MarkoD,
You should also set ports 3-24 as
"Forbidden"for VLAN 2. And just like you know, "Forbidden" or "Excluded" is based on whether or not GVRP will be utilized for the port.
The purpose of these settings is to exclude the port from the VLAN, ultimately determining its VLAN membership.Furthermore, the Ingress filtering discards any packet whose VLAN ID does not correspond to the VLAN associated with the port. It should be noted that this filter only affects packet reception and does not impact the port's membership in the VLAN table.
Zyxel Melen0 -
Thanks, @Zyxel_Melen.
One more question regarding Ingress Filtering: So if I turn this on, the port discards any incoming packets that do not belong to the PVID VLAN?
Isn't this the same as if I make the port Forbidden for all VLANs except the one set as PVID?
In other words, what happens if a port receives a packet belonging to a VLAN it is a Forbidden member of?
0 -
Hi @MarkoD,
Let me use this table to explain. "O" means this port is a VLAN member. "X" means it is not a VLAN member.
VLAN 1
VLAN 2
VLAN 3
Port 1(PVID1)
O
X
X
Port 2(PVID1)
O
O
X
In this table, both ports 1 & 2 enable ingress filtering.
When port 1 receives packets from VLAN 2 or 3, they will be discarded by the ingress filtering.
When port 2 receives packets from VLAN 2 or 3, only the packet from VLAN 3 will be discarded by the ingress filtering. In your words, because a port receives a packet belonging to a VLAN it is a
Forbiddenmember of, so the switch discards this packet.Zyxel Melen0 -
Thank you very much @Zyxel_Melen, if I understand it correctly:
In terms of outgoing traffic: whether a port does not send out packets belonding to a VLAN is determined by being a Forbidden member of that VLAN.
In terms of incoming traffic: whether a port discards incoming packets belonding to a VLAN is determined by being a Forbidden member of that VLAN AND having ingress filtering turned on?
So in your example table above, if ingress filtering was disabled, both ports 1 and 2 would accept traffic from VLANs 1, 2 and 3?
0 -
Hi @MarkoD
In terms of incoming traffic: whether a port discards incoming packets belonding to a VLAN is determined by being a Forbidden member of that VLAN AND having ingress filtering turned on?
Yes. When the ingress filtering is on, a port discards incoming packets belonging to a VLAN is determined by being a Forbidden member of that VLAN.
If the ingress filtering is disabled, both ports 1 and 2 would accept traffic from VLANs 1, 2, and 3, and forward the packet to the member ports.
For example, when port 1 receives the broadcast packets belonging to VLAN 3, the switch will forward to port 2 since port 2 is a member of VLAN3.Zyxel Melen0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Ally Member
Ally Member



 Guru Member
Guru Member



 Zyxel Employee
Zyxel Employee