xgs2210-52 inter-vlan routing troubleshooting
Dear all,
We've configured a stack of xgs2210-52 switches but are running into issues routing traffic between vlans. The environment consists of 2 xgs2210-52 and 2 fortigate 70f connected in full mesh HA fashion, so the switches are stacked and both have a aggregated connection to both firewalls. But we're already running into issues before doing anything fancy, we cant seem to switch traffic between VLANs. Configuration is as described below:
client are connected to both switches on different vlans, echt vlan has a gateway adress configured on the switches which the clients in the matching subnet use as their default gateway. Clients can ping the switch gateway, firewall gateway and dhcp server in their subnet and corresponding vlan, but nothing outside of it.
Switch ports are configured with a single fixed untagged vlan with a matching pvid. The firewall upstream ports are configured with multiple tagged vlans. There are no policies configured. Port security and loop guard are turned off. Strangely the switches themselves, using the diagnostics ping test, cant ping the clients but they can ping the firewall gateways.
All Replies
-
Hi @aminam,
There are some questions I want to clarify with you:
- Does your PC's firewall allow ping?
- What's the default gateway setting of your switch?
If possible, please help to collect the switch tech support and send it to me via private message so I can better clarify your problem. Many thanks.
Zyxel Melen0 -
1: yes the clients allow ping and can be pinged from within the same vlan.
2: I've not configured default routes or next hop on the switch yet. Although the default routes created with the swich interfaces are still present and should suffice from what im trying to achieve at this point.
0 -
Hi @aminam,
Thanks for the feedback and tech support.
May I know if you use laptops and if these laptops also connect to a Wi-Fi SSID? Since you did not set the default gateway on XGS2210, it means your client cannot access the internet. And it will use Wi-Fi as the default path to access. If the clients are laptops and connect to Wi-Fi SSID, the ICMP request/ping will be sent by the Wi-Fi but not the ethernet adapter. Try to disable the Wi-Fi function first and ping other subnets.
Besides, I didn't find any ports set with PVID 9 like the topology you provided from the configuration. The ports were only set with PVID 201, 202, and 203. If the client connects to XGS2210, please make sure the PVID of connecting port is 9.
Zyxel Melen0 -
Hi, You're right I changed pvid 9 on 1/41 (my own client device) because of troubleshooting reasons. The clients are indeed connected to wifi but have static routes configured to the gateway's they're connected to. Routes are for example configured: route -p add 172.31.202.0 MASK 255.255.255.0 172.31.9.253
0 -
Hi @aminam,
I use your configuration to reproduce (with Wi-Fi enable and add route config to my laptop) and I can ping the PC in a different subnet.
Please help to check both of your laptops have set the default gateway to the switch and the route config.
Zyxel Melen0 -
Hi @aminam,
Could you help to use [tracert 'destination IP'] to check where routing failure occurred and use [route print] to check the PC's routing table?
Zyxel Melen0 -
Hi @Melen, of course. below are the prints from the windows client operating from 172.31.9.106 on port 2/41 now, pvid 9 untagged. The 172.31.202.105 is the other client I have access to, the clients 172.31.201.2 and .3 are server remote access cards that are hard to troubleshoot.
0 -
Hi @aminam,
Since the tracert result shows that the client 172.31.9.106 can reach 172.31.201.2, 172.31.201.253, and 172.31.202.253, this looks like the switch routing works with some conditions. I would like to clarify the below information:
- Which port is "172.31.202.105" connecting with? Is the PVID 202? Is its default gateway setting "172.31.202.253"?
- Is the server "172.31.201.3"'s default gateway setting "172.31.201.253"?
Could you help to take more tests to narrow down the problem? Apologize for the duplicate test.
- Use the switch to ping "172.31.202.105" and "172.31.201.3." ⇒ To make sure the switch can reach the client.
- Use "172.31.9.106" to tracert "172.31.202.105" and "172.31.201.3."
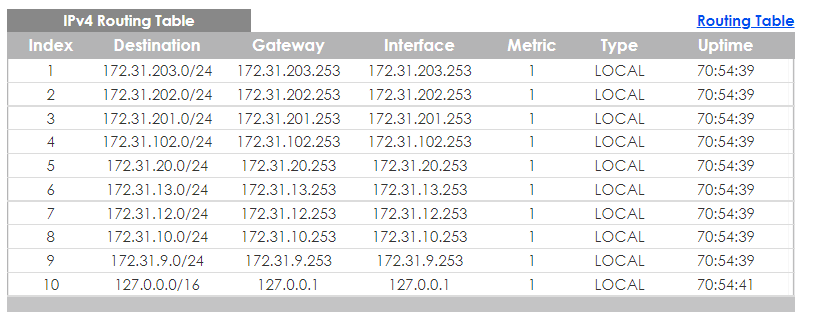
- Collect the switch tech support. ⇒ To check the switch routing table.
Thank you for your assistance!
Zyxel Melen0 -
Hi @Zyxel_Melen
While we were depoying further configuration to our servers it seemed that they were all perfectly routable thrue other vlans. Digging into this further it appears that we used a different gateway on some of the remote access cards, correcting these also made them routable from different networks. And the network devices of course don't use a default gateway but were simply missing static routes to the other networks via the gateway in their own management subnet, duhh…..
So all seems well now, it all makes perfect sense with hindsight. Thanks four help in troubleshooting this.
1
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 476 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Freshman Member
Freshman Member



 Zyxel Employee
Zyxel Employee