Buffer overflow issue FAQ
 Zyxel Employee
Zyxel Employee



Q1. What are the impact model and version for this buffer overflow issue?
Affected series | Affected version | Patch availability |
|---|---|---|
ATP | ZLD V4.32 to V5.36 Patch1 | ZLD V5.36 Patch 2 |
USG FLEX | ZLD V4.50 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
USG FLEX50(W) USG20(W)-VPN | ZLD V4.25 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
VPN | ZLD V4.30 to V5.36 Patch 1 | ZLD V5.36 Patch 2 |
ZyWALL/USG | ZLD V4.25 to ZLD V4.73 Patch 1 | ZLD V4.73 Patch 2 |
Q2. What are the vulnerability details?
The buffer overflow vulnerability could allow an unauthenticated attacker to cause denial-of-service (DoS) conditions even a remote code execution on an affected device and cause IPSec daemon corrupted.
Q3. What are the symptoms?
(1) VPN tunnel disconnection.
(2) No internet service.
(3) The device may hang, resulting in the inability to access the device's local web-GUI and receive CLI responses.
Q4. What should I do to mitigate the risk?
We strongly suggest you upgrade the device to the latest release. You can find out the download link here
If you’re unable to do firmware upgrading immediately, please follow the steps below to edit security policy.
Based on our investigation so far, VPN service is the targeting. We strongly advice disabling VPN services if you’re not utilizing any VPN features such as L2TP, Site-to Site VPN, or Remote Access VPN.
Here is the procedure to disable VPN service.
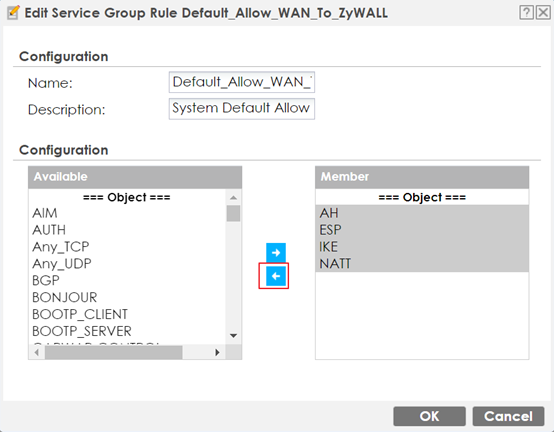
Navigate to Object > Service > Service Group.
From the group "Default_Allow_WAN_To_ZyWALL", remove the services AH, ESP, IKE, and NATT.
If your usage is limited to a site-to-site VPN, we suggest permitting VPN services exclusively for specific source IP addresses.
Q5. What fix is included in the latest release 4.73P2and 5.36P2?
Here it is the CVE information about this release.
CVE-2023-33009
CVE-2023-33010
Q6. Is the device safe after upgraded to the latest release (4.73P2/5.36P2)? Do I need to do extra steps to protect my device?
After the device is upgraded to the latest release, the device will be safe. No further operation is needed.
Q7. Is the device managed by nebula mode also affected?
Yes. The latest release 5.36P2 will be available on cloud by May 24th.
Q8. What should I do if the on-Premise mode Firewall fails to upgrade to the latest firmware?
You can follow the steps to backup configuration & switch to standby partition for upgrading the latest firmware.
Q9. What should I do if Nebula management Firewall is offline from Nebula server after upgrading the firmware?(Sys light flashing)
You can re-plugin the power cord from your device, it should able boots up success.
If the device continues to exhibit the sys light flashing without successfully booting up, it is advisable to report this symptom to Support through the Nebula portal.
All Replies
-
I would like to thank Zyxel to keep supporting ZLD 4.x firewalls with vulnerabilities and problems patches.
Really appreciated.
0 -
Well on one had I am also thankful for the quick fix, however, on the other hand, this is the least ZyXEL can (and must) do, since these vulnerabilities were present in the FW for years (all the way from old version v4.25) and given a CVE score of 9.8 out of 10, this must be a major and serious vulnerability…
I would appreciate ZyXEL being more open on giving details about the vulnerability.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 601 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 480 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight

 Guru Member
Guru Member

 Ally Member
Ally Member






