Q: Branch Office Zywall USG Remote Server Logging (TCP 514) to Head Office remote host over VTI
Hi Zyxel and fellow USG forum lads, I would like to solicit your expertise/advice.
Help Topic: Branch Office Zywall USG Remote Server Logging to Head Office remote host over VTI
Goal: Centralise an instance of all Branch Office Zyxel USG Zyxel appliance logs on main a Head Office Server for audit and archive.
Method Attepted: Specify Logging Remote Server (1-4): logger_host.branch.office
Result: packets are always sent through WAN port of Branch Office Zyxel USG appliances and are sent into the abyss of internet space
Question/ Help: Any clues on how to apply a specific Policy Route or procedure to coerce Branch Office Zyxel USG initiated packets (from the Remote Logger) to send any Head Office over the production VTIx???
THE Remote Server Loggers on the Branch Office USGs simply prepare and send USG log messages over default TCP 514 to the names host - works fine always on the local lans on Branch Office USG appliances.
Existing Production Policy Routes: existing Policy Routes in place for ages for all Branch Office LANx'x , L2TP etc to Head Office LANx's and L2TP and ZYwall via VTI work 100% always !
Diagnostics/ Tools from a Branch Office Zyxel USG:
Zyxel USG router cli to Head Office LAN(s) from USG cli :
nslookup: NS resolves all host names due to Domain Forwarding
ping: times out
traceroute: goes out to WAN and gets lost, times out
packet trace: (parsed by wiresharK):
- source address is always Branch Office Zyxel WAN IP (???)
- destination is Head Office IPV4 of logger_host.branch.office (correct)
Any clues or advice most welcome.
Warwick
Hong Kong
Best Answers
-
Hi @warwickt
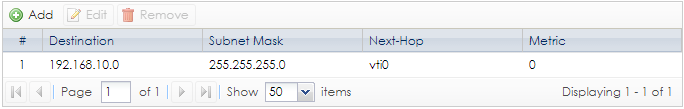
In this scenario, you can add a static route on branch office. It works at my lab.
e.g. the HQ site Lan subnet is 192.168.10.0/24.
Add static route on branch office.
5 -
OSPF:
Hi @Line2 and @Zyxel_Cooldia , this post by @Ian31 , from 2019-April-13 "OSPF Configuration", OSPF with VTI - his article on these forums was most helpful..
https://businessforum.zyxel.com/discussion/comment/7528#Comment_7528
.. and some healthy R.T.F.M.
Method: Using OSPF to coerce a route from Branch Office Zyxel USG Remote logger n to Head Office USG LANx host - works well.
The detail is using the zyxel USG CLI - refer to ZyWALL USG/VPN/ATP Series CLI Reference Guide - Section 14.2.7 - very good
The USG WEBUI seems deficient in configuring the subtle details of OSPF. The informative post from @Ian31 utilises the USG's CLI.
Highlights:
NO static routes nor any additional Policy Routes required - nice.
Just tetsing with simple OSPF Area 0.0.0.0 between these two and works great.
Will move other routers in subsequent OSPF areas and confgure accoringly when stable.
Results:
Head Office ZYXEL USG:
router# show ospf interfaces all areaRouter(config)# show ospf interface all area
Interface Area
===============================================================================
wan1 0.0.0.0
wan2 none
lan1 0.0.0.0
lan2 0.0.0.0
lan3 none
guest none
vlan95 0.0.0.0
vti1 0.0.0.0
vti2 none
vti3 none
Router#
Branch Office ZYXEL USG:
Router# show ospf interface all area
Interface Area
===============================================================================
wan1 0.0.0.0
lan1 0.0.0.0
lan2 none
lan3 none
opt none
vti1 0.0.0.0
vti2 none
Router#
Steps to Do this with OSPF using the USG CLI (ssh (-p <port>) admin-account@your-router.internal.domain ) :
1) map the routers into an OSPF backbone (Area 0.0.0.0) and subsequent satellite OSPF areas
2) add some IPV4 style OSPF identifier to each router...
3) on each router, configure the the particulare OSPF AREA number and associate it with the INTERFACE(s) that are associated wi that OSPF.
e.g.
Router(config-router)# network WAN1 area 0.0.0.0Router(config-router)# network VTI2 area 0.0.0.3 etc etcrefer to the current flavour of ' ZyWALL USG/VPN/ATP Series CLI Reference Guide - Section 14.2.7'
Thanks for the assistance to this point.
Regards
Warwick
Hong Kong
0 -
Good to hear you also moved to OSPF. It seems not to be widespreaded at ZyXEL customers. I waited for a long time for OSPF/VTI.
Line2
5
All Replies
-
Hi
We use central logging for a lot of sites (over VTI/IPSec) with no problems yet. How does your policy routes on the branch USGs look like? We use OSPF for routing not policy routing. Maybe try a static route on the branch USGs to the Head office.
Line2
0 -
Hi @warwickt
In this scenario, you can add a static route on branch office. It works at my lab.
e.g. the HQ site Lan subnet is 192.168.10.0/24.
Add static route on branch office.
5 -
Hi @Line2 and @Zyxel_Cooldia, thankyu both for your most appreciated prompt replies.
Zyxel_Cooldia: Use of a static route from Branch Office to Head Office.
Result: Some progress! I just tried this and indeed it routes this traffic over the intended VTIx (packet capture at Branch Office ISG :514 syslog)
Affect: However the SRC address of the Branch Office ZYxel USG is not the B.O. LANx nor VTI gateway/address but is the WAN address of the Branch Office USG.
Thus (sadly) the Head Office USG Security Policies default will reject it.
( in this configuration, The B.O. offices are ISP DHCP... not static IP)
Is there a method to coerce the SRC (source) address of the Branch Office Zyxel USG to apear from the VTIx end (i.e 10.161.99.15/32) or a B.O LANx address (i.e. 10.233.109.0/24) ?
Line2: The use of OSPF looks like the good. Is there any straight forward (easy to digest) documentation on this for the USG other than the ZYWALL USG Users Guide (V4.33)
Any help or directions appreciated.
Warwick
Hong Kong
0 -
OSPF:
Hi @Line2 and @Zyxel_Cooldia , this post by @Ian31 , from 2019-April-13 "OSPF Configuration", OSPF with VTI - his article on these forums was most helpful..
https://businessforum.zyxel.com/discussion/comment/7528#Comment_7528
.. and some healthy R.T.F.M.
Method: Using OSPF to coerce a route from Branch Office Zyxel USG Remote logger n to Head Office USG LANx host - works well.
The detail is using the zyxel USG CLI - refer to ZyWALL USG/VPN/ATP Series CLI Reference Guide - Section 14.2.7 - very good
The USG WEBUI seems deficient in configuring the subtle details of OSPF. The informative post from @Ian31 utilises the USG's CLI.
Highlights:
NO static routes nor any additional Policy Routes required - nice.
Just tetsing with simple OSPF Area 0.0.0.0 between these two and works great.
Will move other routers in subsequent OSPF areas and confgure accoringly when stable.
Results:
Head Office ZYXEL USG:
router# show ospf interfaces all areaRouter(config)# show ospf interface all area
Interface Area
===============================================================================
wan1 0.0.0.0
wan2 none
lan1 0.0.0.0
lan2 0.0.0.0
lan3 none
guest none
vlan95 0.0.0.0
vti1 0.0.0.0
vti2 none
vti3 none
Router#
Branch Office ZYXEL USG:
Router# show ospf interface all area
Interface Area
===============================================================================
wan1 0.0.0.0
lan1 0.0.0.0
lan2 none
lan3 none
opt none
vti1 0.0.0.0
vti2 none
Router#
Steps to Do this with OSPF using the USG CLI (ssh (-p <port>) admin-account@your-router.internal.domain ) :
1) map the routers into an OSPF backbone (Area 0.0.0.0) and subsequent satellite OSPF areas
2) add some IPV4 style OSPF identifier to each router...
3) on each router, configure the the particulare OSPF AREA number and associate it with the INTERFACE(s) that are associated wi that OSPF.
e.g.
Router(config-router)# network WAN1 area 0.0.0.0Router(config-router)# network VTI2 area 0.0.0.3 etc etcrefer to the current flavour of ' ZyWALL USG/VPN/ATP Series CLI Reference Guide - Section 14.2.7'
Thanks for the assistance to this point.
Regards
Warwick
Hong Kong
0 -
Good to hear you also moved to OSPF. It seems not to be widespreaded at ZyXEL customers. I waited for a long time for OSPF/VTI.
Line2
5
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Ally Member
Ally Member



 Zyxel Employee
Zyxel Employee



 Freshman Member
Freshman Member




