How to configure the switch to send unauthorized users in a Guest VLAN
 Zyxel Employee
Zyxel Employee



The example shows administrators how to use Guest VLAN for users that fails or used an invalid user credential during 802.1x port authentication. In a real application, we may need to allow guests to access the USG so that they can access the Internet, but still isolated from Private-Server. On the contrary, we have to allow the users with valid credentials to only access the Private-Server.
Note:
All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses and subnet masks.
1. Configuration
1-1. Configure 802.1x Port Authentication in the switch
Configure 802.1x on all towards users. Do not enable Port Authentication on ports to the USG, RADIUS-Server, and Private-Server.
1-2. Configure VLAN for Guest VLAN in the switch
Configure the VLAN for Guest VLAN (VLAN 100) on Switch. VLAN 100: Set fixed port: 1, 2, 3, 30; untagged port: 1, 2, 3, 30; forbidden port: 31, 32; port 30: pvid=100. VLAN 1: Set forbidden port: 30. For isolating VLAN 1 and 100.
1-3. Configure Guest VLAN for Failed Authentication in the switch
Go to Menu > Advanced Application > Port Authentication > 802.1x > Guest Vlan. Activate the Guest Vlan on port 1-3 and type the guest Vlan as 100. Press “Apply”.
1-4. Configure the RADIUS Server
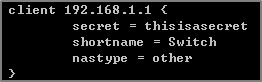
1-4-1. Edit the client profile in /etc/freeradius/clients.conf. Save the file and exit.
Note:
The client IP address and secret must match the management IP and shared secret of the Switch.
1-4-2. Add the following user profiles in /etc/freeradius/users. Save the file and exit.
1-4-3. Restart FreeRADIUS service.
1-5. Configure the setting on User-A, User-B and Guest in Windows
1-5-1. In the Services window, locate the service named Wired AutoConfig. Make sure the service status is “Started”.
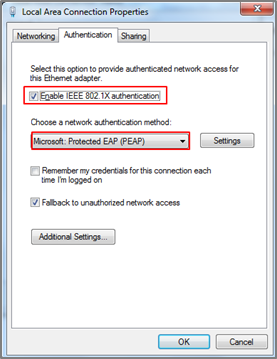
1-5-2. Right-click on your network adapter and select Properties. Click on the Authentication tab and check “Enable IEEE 802.1X authentication”. Make sure that the network authentication method is “Microsoft: Protected EAP (PEAP)”.
1-5-3. Click on Additional Settings, select Specify authentication mode and specify User authentication.
2. Test the Result
2-1. Disconnect and connect the PC with Switch. PC should show an “Additional information is needed to connect to this network.” pop-up message.
2-2. Enter the username (User-A) and password (zyxeluserA) which must be consistent with the RADIUS-Server’s user profile settings.
2-3. Devices using User-A and User-B credentials can communicate with Private-Server.
2-4. Connect User-A device to the Switch. User-A should show an “Additional information is needed to connect to this network.” pop-up message.
2-5. Enter the username (Guest) and a random password.
2-6. Device using Guest credentials cannot communicate with Private-Server, but it can communicate with USG.
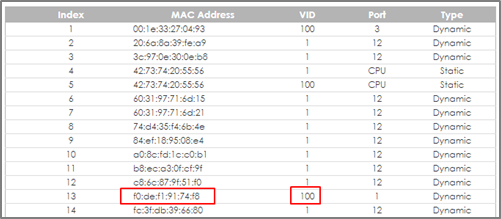
2-7. Check the MAC table of the Switch. The device of users with wrong credentials are assigned to VLAN 100. (Menu > Management > MAC Table > Search)
3. What Could Go Wrong
3-1. If the PC doesn’t pop up the authentication message after connecting the PC to the switch:
3-1-1. Try to use the Switch to ping Radius-Server. The Switch should be able to ping Radius-Server.
3-1-2. Right-click on your network adapter and select Properties > Authentication > Additional settings. Uncheck the “Validate server certificate”.
3-2. If the shared secret setting of Switch and PC does NOT match, the authentication will fail.
3-3. If the authentication is fine, but the PC cannot ping Server, please check 801.1X Port Authentication configurations. Do NOT activate the authentication on the uplink port (port 2, 3, and 12).
3-4. If devices sent to the Guest VLAN cannot reach the USG, make sure that the switch has created and configured the Guest VLAN in Advance Application > VLAN > VLAN Configuration > Static VLAN Setup.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 220 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 602 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight