How to configure the switch and RADIUS server to provide network access through device's MAC address
 Zyxel Employee
Zyxel Employee



Switch firmware version: 4.70 and before
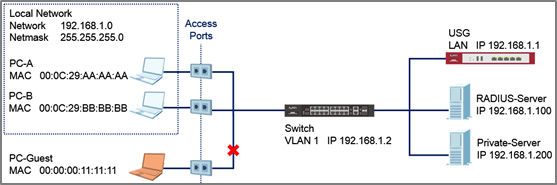
This example will instruct the administrator on how to configure the switch to provide access to machines with specific MAC addresses. With MAC Authentication, the organization can ensure that only devices provided by the organization can access internal resources.
Note:
All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses and subnet masks. The authentication server used in this example is FreeRADIUS running in Ubuntu server. All UI displayed in this article are taken from the XGS4600 series switch.
1. Configuration in the Switch
1-1. Access the Switch’s Web GUI.
1-2. Go to Advance Application > AAA > RADIUS Server Setup. Configure the RADIUS server’s IP address and set the shared secret. Click Apply.
Note:
The shared secret must match the secret of your RADIUS server’s client profile.
1-3. Go to Advance Application > Port Authentication > MAC Authentication. Check the MAC Authentication Active box as well as for access ports. Do not check the active box of ports connected to either the USG, RADIUS-Server, or Private-Server.
2. Configuration in the RADIUS Server
2-1. Edit the client profile in /etc/freeradius/clients.conf. Save the file and exit.
Note:
The client IP address and secret must match the management IP and shared secret of the Switch.
2-2. Add the following user profiles in /etc/freeradius/users. Username format should be <Name Prefix><MAC Address of your device>. Save the file and exit.
2-3. Restart FreeRADIUS service.
3. Test the Result
3-1. Connect PC-A, PC-B, and PC-Guest to the Switch.
3-2. PC-A and PC-B should be able to reach the USG and Private-Server.
3-3. PC-Guest should not be able to reach the USG and Private-Server.
4. What Could Go Wrong
4-1. If the Switch does not allow access to authorized devices:
4-1-1. The RADIUS-Server’s user profile must use all upper-case characters of the device’s MAC Address separated by dashes (-) instead of colons (:).
4-1-2. Machines, like laptops or notebooks have more than one MAC addresses (LAN, Wireless, etc). Make sure that the correct MAC address is used in the RADIUS-Server’s user profile.
4-2. If the Switch still does not allow access to authorized devices after correcting the Switch or RADIUS-Server configurations, wait for a few minutes before trying again. This is determined by the MAC Authentication’s timeout value, where the default time a devices is re-validated is 300 seconds.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight