Using a ZyXEL USG as a RADIUS server to authenticate users on a GS-Series Switch with 802.1X
 Freshman Member
Freshman Member

Hi all,
There is a FAQ entry on using an external Radius server to allow users to be authenticated on a ZyXEL GS Series switch where 802.1X authentication has been enabled:
However, what if I were to want to use a ZyXEL USG to be the server for this purpose? 802.1X for wireless devices works just fine, but when I put the IP address of the USG into the Switch for RADIUS authentication, is doesn't work!
Can this be done? and if so, maybe there are some additional steps needed in the USG to authenticate the switch?
All Replies
-
So do you want to use USG as RADIUS server to authenticate hosts on the switch via 802.1x (port-auth) but it didn't work?
Have you checked the associated service setting (such as windows service "WiredAutoConfig") on your host? I mean the one that FAQ article has mentioned.
0 -
Hi Sakura_T
Thanks for the reply.
You are right; the client PC (Windows 10) has the 802.1X (Wired) authentication enabled and I get the popup on my laptop screen.
The USG has users populated and the Wireless authentication works as expected. When I check the USG logs I don't see any entries regarding authentication failures.
I have put into the switch that all ports need to use 802.1X (apart from the port to the USG and a test port so I can get in!) and the key is set up to authenticate between the two.
So... the Switch and the laptop know to use 802.1X, the USG has the users, the issue seems to be that the switch and USG are not presenting user credentials / authentication.
Is there something in the USG settings that needs to say that the switch itself is authorised to make such requests? I ask because I assume the USG needs to be satisfied that the switch is a trusted device, otherwise a hacker could just fire usernames and passwords at ports 1812 and 1813 until they get lucky.
0 -
For RADIUS server configuration on USG, Configuration > System > Auth.Server, and add profile (including IP, shared secret) of the switch.
And create user-profile in Configuration > Object > User/Group.
On Zyxel switch, Advanced Application > Port Authentication > 802.1x, activate and check the desired ports.
AAA > RADIUS Server Setup, set RADIUS server's IP and shared secret.
AAA > AAA Setup > Authorization, activate Dot1x.
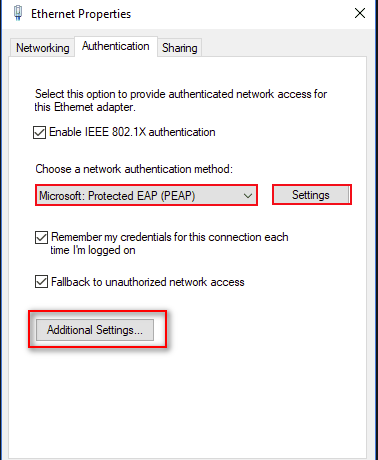
On Windows 10, the detail settings in Ethernet Properties > Authentication should also be taken into account.
Zyxel_Lucious
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 128 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Ally Member
Ally Member


 Zyxel Employee
Zyxel Employee