Possible or not? 1USG20W-VPN together with a Zyxel AP,so that end devices seamlessly roam same WiFi
 Ally Member
Ally Member



Hello, I have an USG20W-VPN, and its WiFi6 is not enough to cover all the intended areas. Now, I evaluate an additional Access Point with WiFi7 and WPA3 to extend the wireless access where is needed, namely an NWA50BE Pro.
Now, I haven't received yet the new AP, but I assume that it will cover the existing area better, so that I might even be able to switch off the wireless on the firewall and use only the new AP with a better overall signal and performance coverage.
If not, I might end up having to use the current firewall WiFi to coexist with the new AP.
Scenario1, for me the ideal one: both existing firewall WLAN and new AP can use the same wireless name SID etc, so that the moving devices roam accordingly to the stronger signal around the perimeter.
Can the two devices extend one single WiFi between them, making the devices capable of WiFi7 and WPA3 to seamlessly switch between the new AP and the WiFi6 / WPA2 of the older firewall + WiFi device?
If yes, how?
Scenario2: existing firewall WLAN remains unmodified, new AP has a new WLAN, and the devices switch accordingly between them for stronger signal.
Scenario3: I might be able to use only the new AP and turn off the WLAN from the firewall, given that I have then overall WiFi7 and WPA3.
Which tools do you recommend for the signal coverage and tuning of the WLAN(s)?
For all possible scenarios above: what do you recommend me to use so that I can measure and then fine-tune the WiFi signal strength for the firewall WLAN and for the new AP WLAN, so that they do not constantly beacon up each other to maximum signal strength against each other?
Anything else that you suggest?
All Replies
-
Hi @Zyxel_USG_User,
For your current setup, we recommend configuring both your existing USG-20WVPN firewall and the new NWA50BE Pro WiFi 7 access point to broadcast the same SSID, which can enable seamless client roaming between devices.
In order to enable proper roaming functionality, please ensure both the USG-20WVPN and NWA50BE Pro are configured with:
Identical SSID
Identical password
Matching security settings (WPA2/WPA3)
Moreover, for optimal roaming performance, please verify that your USG-20WVPN and NWA50BE Pro have overlapping wireless coverage areas. The signal strength from each neighboring access point should measure between -80 dBm and -85 dBm at the coverage overlap zones. This ensures clients can seamlessly transition between access points without experiencing connection drops or interruptions.
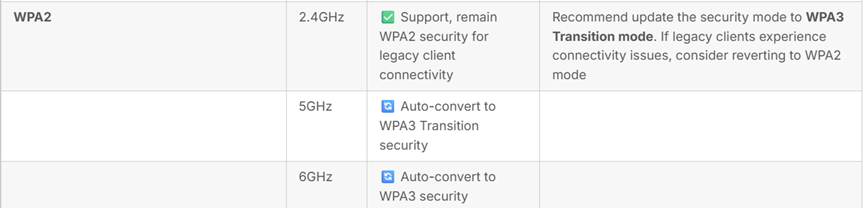
However, one important consideration for WiFi 7 BE mode access points is that with firmware version 7.20 and later, there is an automatic security protocol upgrade behavior. When the security option is configured as WPA2 on the 5 GHz band, the system will automatically convert it to WPA3. Users should be aware of this automatic conversion when planning their network configurations, as it may affect compatibility with older client devices that only support WPA2.
Here is the link regarding the new behavior with the release of the new AP firmware 7.20:
If you have any questions, please do not hesitate to contact us. Thanks!
Best Regard,
Lynn
0 -
Hello, thanks a lot for the prompt and detailed answer!
This was very helpful. I have a better idea now how to plan and test the WiFi for seamless roaming.
I will revert with questions as soon as I have the device and start configuring and testing.
Thank you & Kind regards
0 -
Hello again
I set up the NWA50BE Pro working standalone, no Nebula. It works as standalone AP or together with the same WiFi SSID from the firewall. The roaming works without interruptions and I will fine-tune the powers of the antennas along time. We have a mixed environment with many OSs for workstations, notebooks, smartphones.
Firewall has WLAN 'standard1' with SSID1, AP has WLAN 'standard1' with SSID1, same password. Can I / should I assign different passwords to the same WLAN name but specific to each device? Would that cause an interruption- even if minimal in roaming, versus having the same password for the same WLAN on two devices?
I changed to NAT on both antenna configurations.
Now, I have some questions:
- when looking at the AP in the monitoring section, the leased IPs are all over the place from one huge subnet with too many clients for my taste, theoretically possible. Is this correct? clients connected to 2.4 Ghz always get IPs from different subnets, same on 5 Ghz, same on 6 Ghz. Is this for safety reasons, arbitrarily leasing IPs across many subnets in a huge IP network?
- Can I edit and limit the DHCP server when using NAT, per antenna, or per frequency? for example, I want to see antenna1 leases 172.1.1.1 to .30, and antenna 2 leases 172.3.3.1 to .100, or 2.4 Ghz leases 172.1.1.1 to .30 and 5 Ghz and 6 Ghz share same pool 172.3.3.1 to .100. Can I configure that, on this specific AP model? If yes, how?
- IPP is propagated with NAT on the WLAN for printing from Apple devices on another network, so can I assume that the Apple stuff like discovery etc will also be automatically NATed ?
0 -
I wanted to open a new question, but the system does not allow this. I need to select a theme but there is none to choose from! Without a category selected, I cannot post! Please fix.
Now, to my 'other' question I wanted to ask, I will put it in this thread because 1. I cannot post it separately as a new question, 2. it involves the same setup between two Zyxel devices, a firewall and a standalone AP. If you decide to split the below question into a new one, please notify me as well with the new link / question / thread, thank you.
Can I use a Zyxel firewall to aggregate in its logs also the log of an external Zyxel AP?
Can I send out email alerts from this standalone AP? If yes, how?
I have an USG20W-VPN and an NWA50BE Pro. I need to go to both devices individually to see their logs. Can I somehow aggregate the NWA AP to push its logs as configured to the firewall log, if I do not have a syslog server? If the AP logs would be accordingly marked in the firewall log, I would save me the logging on another device and have all the logs centralised on the firewall. I am aware also of the downsides of such, as filling the firewall log faster with entries from 2 devices. Just asking whether is possible or not, and if yes- how.
On the firewall I can configure it that if failed user logins are detected, sends out an email. I do not see any options to configure such on the AP, how can I achieve this and other sorts of notifications on the AP?0
Categories
- All Categories
- 441 Beta Program
- 2.9K Nebula
- 210 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 540 USG FLEX H Series
- 340 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 464 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 86 About Community
- 99 Security Highlight
 Zyxel Employee
Zyxel Employee