How to run two IKEv2 tunnels (full + split) on the same router?
 Freshman Member
Freshman Member


We have external staff accessing company resources via smartphones and laptops.
Previously we used IPSec IKEv1 tunnels, but now we’re moving to IKEv2.
Smartphones are already set up with an IKEv2 “all traffic” tunnel (EAP auth with username/password, config payload works fine).
Now we want laptops/PCs to connect via IKEv2 as well, but they must use split tunneling due to limited bandwidth at HQ.
When we add a second IKEv2 connection as a split tunnel, clients hit the wrong tunnel and fail to connect.
Question: How can we configure two IKEv2 tunnels on the router so that smartphones always get the full tunnel and laptops/PCs always get the split tunnel?
We’d like to keep EAP with username/password for auth and push IP settings via payload.
Thank's
Dirk
(This was kindly supported by ChatGPT)
All Replies
-
I take it this is for the non H models USG?
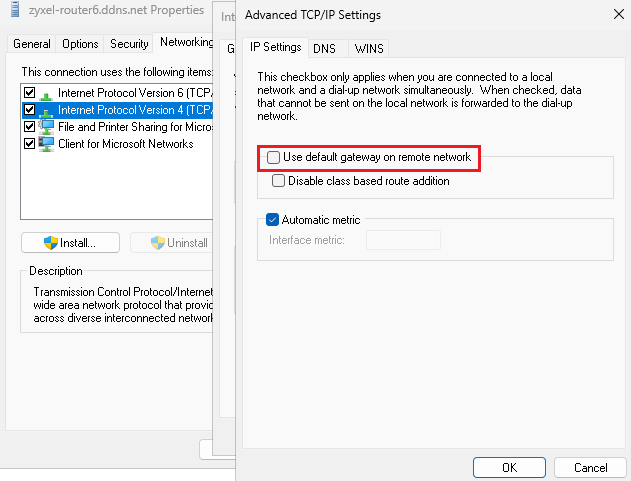
In windows you can disable full tunnel by VPN setting IPv4
Then for split tunnel use PowerShell
Add-VpnConnectionRoute(VpnClient) | Microsoft Learn
Add-VpnConnectionRoute -ConnectionName "zyxel-router6.ddns.net" -DestinationPrefix 192.168.138.0/24
Using StrongSwan client on phone and windows built in client both clients where able to connect but you need to change Windows EncryptionMethod to match StrongSwan default
Phase 1
AES256 SHA256
DH14
Phase 2
AES256 SHA256
DH2use PowerShell
Set-VpnConnectionIPsecConfiguration(VpnClient) | Microsoft Learn
Set-VpnConnectionIPsecConfiguration -ConnectionName "zyxel-router6.ddns.net" -AuthenticationTransformConstants SHA256128 -CipherTransformConstants AES256 -EncryptionMethod AES256 -IntegrityCheckMethod SHA256 -PfsGroup PFS2 -DHGroup Group14 -PassThru -Force
0 -
I forgot to mention that we’re using the Zyxel VPN Client because we need the GINA feature, meaning the tunnel has to be established before Windows login.
With the Windows built-in client this only works on a device level, but we need a user-based VPN tunnel.0 -
The Zyxel VPN Client should fine with that setup
0 -
-
So from the replies I take it that on the router side only one IKEv2 tunnel is configured, running as an “all traffic” tunnel (i.e. also allowing WAN traffic)?
And to use split tunneling, the adjustment is instead done on the client side by defining the target networks?If that’s correct, then this wouldn’t work together with configuration payload, meaning we’d have to assign client IPs manually after all – is that right?
0 -
Hi @MyForumUser
Let me provide you another way for your purpose:
- Use Wizard to create the full tunnel IKEv2 VPN, and download the script for your Android users.
- Navigate to configuration > object > User/Group to create a full tunnel user group.
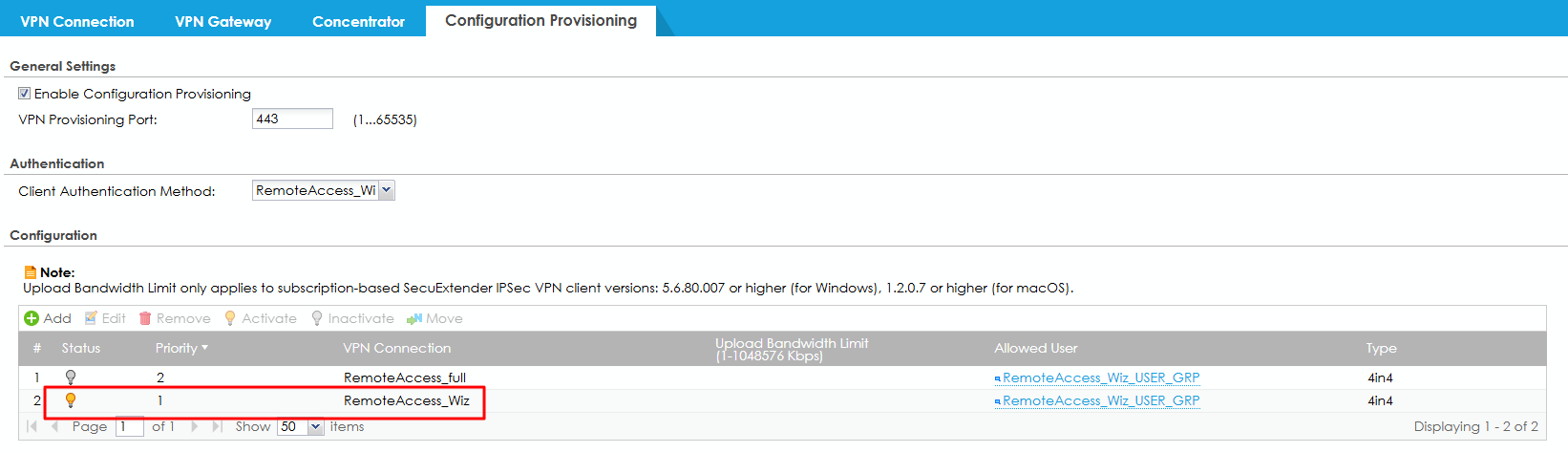
- Navigate to configuration > VPN > IPsec VPN and change full tunnel's name on VPN connection and VPN gateway page, phase 1's allowed user from Remoteacess_Wiz_USER_group to the full tunnel user group.
- Use Wizard to create the split tunnel IKEv2 VPN, and set the allowed user for split tunnel. (Remember to remove full tunnel users if they are listed in the allowed user list.)
- Navigate to configuration > VPN > IPsec VPN and change split tunnel's phase 1 and phase 2 proposal, like AES256/SHA256. This step is to make split tunnel's proposal be different from the full tunnel.
- Navigate to configuration > VPN > IPsec VPN > Configuration Provisioning and disable the provision of full tunnel profile.
- Use the get from server option on the SecuExtender to get the split tunnel's configuration.
Additionally, use the same proposal may cause the VPN connection been disconnected since it might match to the VPN profile that is not you want to connect. Use differenet proposal can aviod this issue.
Zyxel Melen0 -
Thanks for the reply @Zyxel_Melen
We’re not using the Wizard since we prefer to create and name the objects on the router manually. Let me summarize what we did:
Created two IKEv2 tunnels (each with its own Phase 1/Phase 2), with different proposals for full vs. split.
Set up two VPN user groups and assigned them to the respective tunnels.
Added a separate certificate for the split tunnel.
Configured different IP ranges for full and split to avoid overlap in the configuration payload (not sure if the Zyxel checks across tunnels to prevent duplicate IPs).
On mobile devices we use the full-tunnel cert and a full-tunnel user, with proposals left on auto.
On PCs/laptops (SecuExtender client) we explicitly set the split proposals, the split cert, and a split user.
With this setup, devices do select the correct tunnel (mobiles → full, PCs/laptops → split). Split DNS doesn’t seem to work — all DNS goes through the tunnel — but that’s fine. The main point is that PC traffic now goes out locally, not through the tunnel, so it looks like it’s working.
Final question: On the PC/laptop side, what exactly do we need to configure to ensure the correct tunnel is always chosen? How does the Zyxel decide which tunnel to use?
0 -
With
IPSec_SSL_VPN_7.7.50.008
and StrongSwan
and two IKEv2 Remote Access (Server Role) Certificates with different Phase 1 Proposals I've seen some mixed problems.With StrongSwan you can't have a site to site IKEv2 even with different Certificates with a IKEv2 Remote Access (Server Role) for StrongSwan even if Phase 1 Proposals are different.
With IPSec_SSL_VPN_7.7.50.008 on different Certificates with StrongSwan Remote Access (Server Role) even if Phase 1 Proposals is different as StrongSwan connects but SecuExtender client can not even if SecuExtender client cryptography is set!
How to solve this use in SecuExtender client to set local ID like Email any@any .com and set for on USG for that gateway VPN peer ID Email any@any .com but you need to do the same for the other gateway VPN for StrongSwan so set peer ID Email any2@any .com and on StrongSwan client set client identity any2@any .com now both Remote Access (Server Role) work.
Also with SecuExtender VPN Client if you set traffic selectors with VPN client address to 0.0.0.0 it uses the that devices IP to send to the remote LAN down the VPN tunnel which may cause problem if the other end uses the same LAN subnet as the client or two clients have the same LAN IP to go down the tunnel so might be best to set that.
0 -
Hi @MyForumUser
Please ensure:
- Different phase 1 and phase 2 proposal for different VPN tunnels.
The Zyxel firewall will check the proposal first when the remote access VPN connects. If you use the same proposal, you might connect to the wrong VPN tunnel (match by the order of the VPN tunnel).
Zyxel Melen0
Categories
- All Categories
- 441 Beta Program
- 2.9K Nebula
- 210 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 540 USG FLEX H Series
- 340 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 464 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 86 About Community
- 99 Security Highlight
 Guru Member
Guru Member


 Zyxel Employee
Zyxel Employee