Site to Site VPN with Dynamic DNS
hi,
I have been able to set up site-to-siten VPN with dynamic DNS to the point it almost works.
My problem is that for the other site I am not able to set the public address as WAN address. The operator makes a NAT that I can't do anything about. Is there any way to tell the VPN to use Dynamic DNS for the local IP address resolution instead of the WAN address given by the operator through DHCP? If there is, what configurations will be needed?
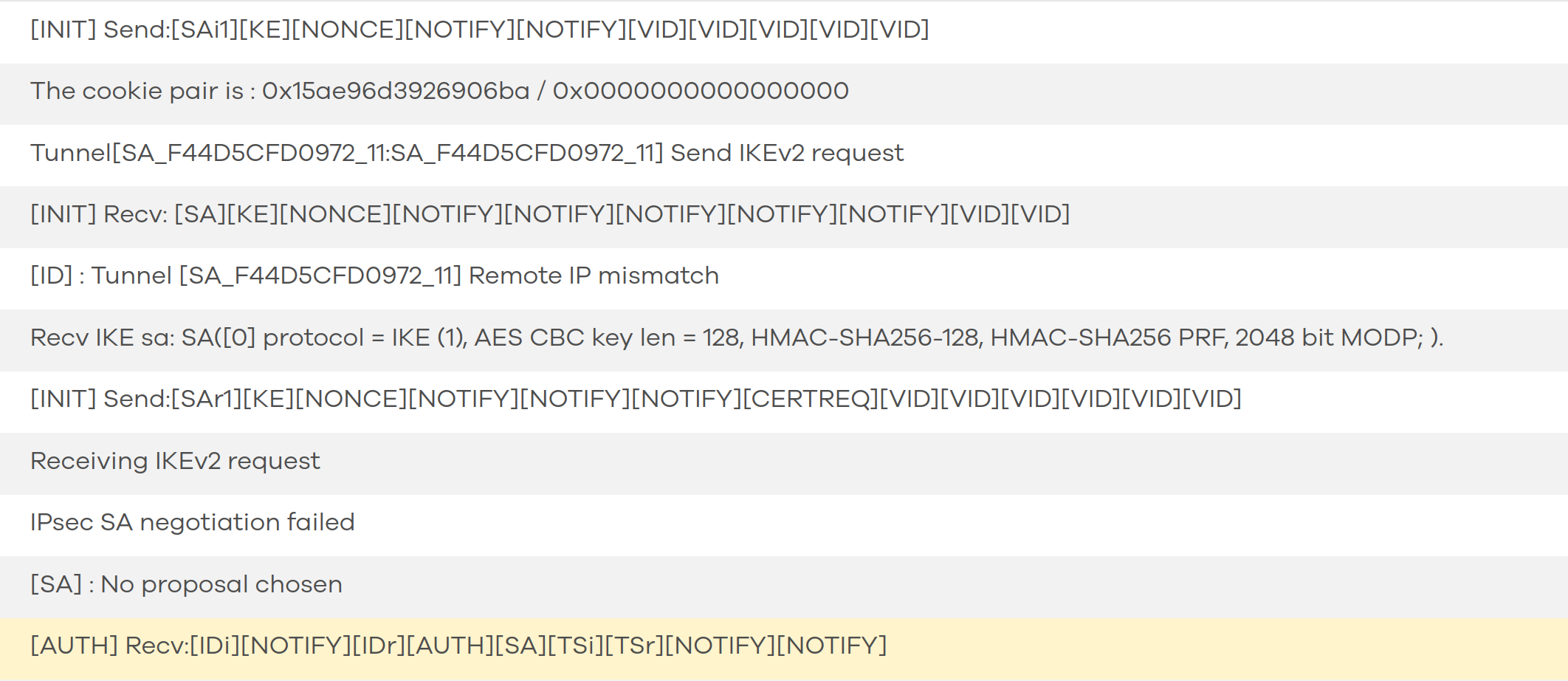
The log on the site that has the dynamic address behind the operator NAT looks like this:
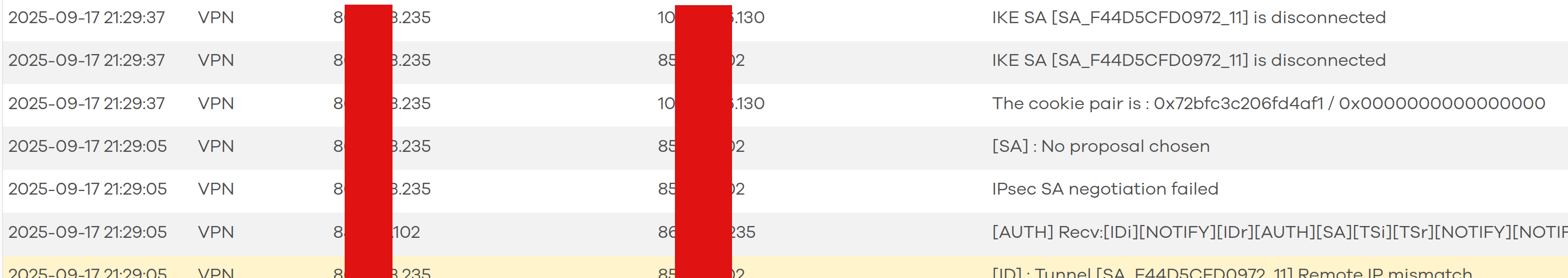
The log on the site that has the proper public ip looks like this:
The log shows that some of the rows show that the other site is able to send a message back (the [auth] line), and some lines show that the target IP is on some of these is the IP behind the NAT (part of IKE SA log lines and The cookie pair line).
Accepted Solution
-
hello @jtk
I had a similar issue years ago. I didn't use Zyxel back then, but my Routers were not able to establish a site-to-site VPN. The solution back then was to run the router with the public IP as server and the other one with the dual-NAT as client. Both stayed connected 24/7 and they acted like they were on a site-to-site VPN. No port forwarding was needed on the client side.
While it is possible to set up one Zyxel router as VPN server, unfortunately Nebula doesn't allow one router to be setup as client. I am not familiar with on premise settings, maybe it is possible there. Maybe it is possible to add a dedicated VPN client to the site behind the CG-NAT to establish the VPN connection?
I got rid of the dual-NAT so this problem doesn't apply to my networks anymore. With the CG-NAT in place, you'll never get the required ports forwarded to your router. Your ISP will simply not do it.
You could ask your ISP to change your connection to a public IPv4. Maybe they offer such an option.
0
All Replies
-
If the operator NAT side can't port forward 500 or 4500 the public ip site can be set to Dynamic Address the side that has NAT can then connect out to the site to site with public ip.
0 -
Hi @jtk,
From the logs you shared, it looks like the issue is caused by an IP mismatch because the firewall is behind the uplink NAT router during the VPN negotiation. This leads to a situation where the IPsec negotiation fails and prevents the tunnel from completing successfully.
Here are two approaches that may help resolve the issue you are facing:
- Enable port forwarding on the NAT router (UDP 500 and 4500)
- IPSec VPN relies on UDP ports 500 (IKE) and 4500 (NAT-T) for tunnel establishment and negotiation.
- Without these ports being forwarded, the firewall behind NAT can only initiate the connection, but it cannot reliably accept or respond to inbound VPN traffic.
- By configuring the NAT router to forward UDP 500 and 4500 to your firewall, the device behind NAT can properly receive VPN traffic and behave as if it had the public IP directly.
- Assign a public IP directly to the firewall
- If your ISP provides a public IP range, you can assign one of those public IPs directly to the firewall instead of relying on the NAT router.
- In this case, the firewall itself will hold the public IP, which eliminates the mismatch between the internal IP and the real public IP.
- This ensures that VPN negotiation can be completed smoothly without IP identity conflicts.
Additionally, as @PeterUK suggested, another practical approach is to configure the public IP site with Dynamic Address and always let the firewall behind NAT initiate the VPN connection. This method avoids the need for port forwarding and may be worth trying as well.
Zyxel Tina
0 - Enable port forwarding on the NAT router (UDP 500 and 4500)
-
Thank you for both the answers. It seems that in my case, it is best to select the site behind NAT to be the one that establishes the connection.
For some reason I can's seem to be able to find the place in Nebula for this setting. Could you please point to a correct instructions or tell in which part of settings it can be found?
0 -
Hi @jtk,
Sorry for the late reply!
Regarding your requirement,
It seems that in my case, it is best to select the site behind NAT to be the one that establishes the connection
please ensure to configure the NAT traversal IP addresses in Nebula for proper connectivity.
You may refer to this FAQ for detailed setup instructions.
Zyxel Tina
0 -
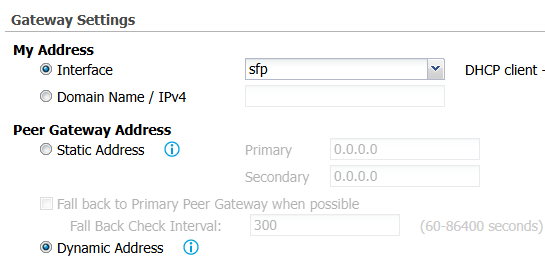
hi, I did configure the NAT traversal IP using dynamic DNS. The problem is that the "public" IP address of my 60AX sees is not actually public, but it is a NATted address behind operator's NAT.
So the earlier replies suggested that the solution is to order the 60AX to be the initiator of the VPN, as the public address is OK on the main site. But I can't find a way to do this.
0 -
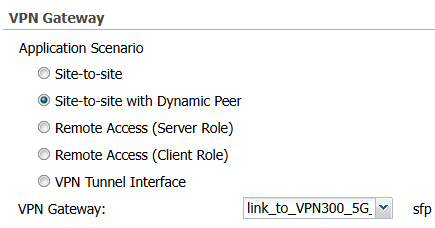
in stadnalone you set to Dynamic Address then set Site-to-site with Dynamic Peer
0 -
hi,
I had the 60AX off for several days. After that, when I powered it on, there was first a partially connected VPN, until it failed again. I attach a piece of log:
Establishing the tunnel starts, but there is a message of "Remote IP mismatch", and after that the firewall (FLEX100) tries to connect directly to the private IP behind NAT. On the 60AX side I can't find the setting to set IKE to use the dynamic dns to use as local IP.
As for the settings, I would very much prefer not to remove the firewall from Nebula to access the local settings, as that would mean a lot of reconfiguration and paying for the Nebula Pro pack really becomes useless.
I also tried configuring Auto-Link VPN, as Zyxel AI recommended trying that. But I would need more advice on how to configure that, with the IP subnet and connectivity check settings, at least.0 -
hello @jtk
I had a similar issue years ago. I didn't use Zyxel back then, but my Routers were not able to establish a site-to-site VPN. The solution back then was to run the router with the public IP as server and the other one with the dual-NAT as client. Both stayed connected 24/7 and they acted like they were on a site-to-site VPN. No port forwarding was needed on the client side.
While it is possible to set up one Zyxel router as VPN server, unfortunately Nebula doesn't allow one router to be setup as client. I am not familiar with on premise settings, maybe it is possible there. Maybe it is possible to add a dedicated VPN client to the site behind the CG-NAT to establish the VPN connection?
I got rid of the dual-NAT so this problem doesn't apply to my networks anymore. With the CG-NAT in place, you'll never get the required ports forwarded to your router. Your ISP will simply not do it.
You could ask your ISP to change your connection to a public IPv4. Maybe they offer such an option.
0 -
Thanks for all your effort for trying to help me.
I was finally able to get a public IP from my ISP/operator for my 60AX, so now the IKE negotiations work and the tunnel got up without changing any settings.
1
Categories
- All Categories
- 441 Beta Program
- 2.9K Nebula
- 210 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 540 USG FLEX H Series
- 340 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 464 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 86 About Community
- 99 Security Highlight
 Freshman Member
Freshman Member



 Guru Member
Guru Member


 Zyxel Employee
Zyxel Employee