[USG Flex 100H] - Policy Control not working
 Ally Member
Ally Member

Hello everyone,
I have an USG Flex 100H with some custom Policy Control.
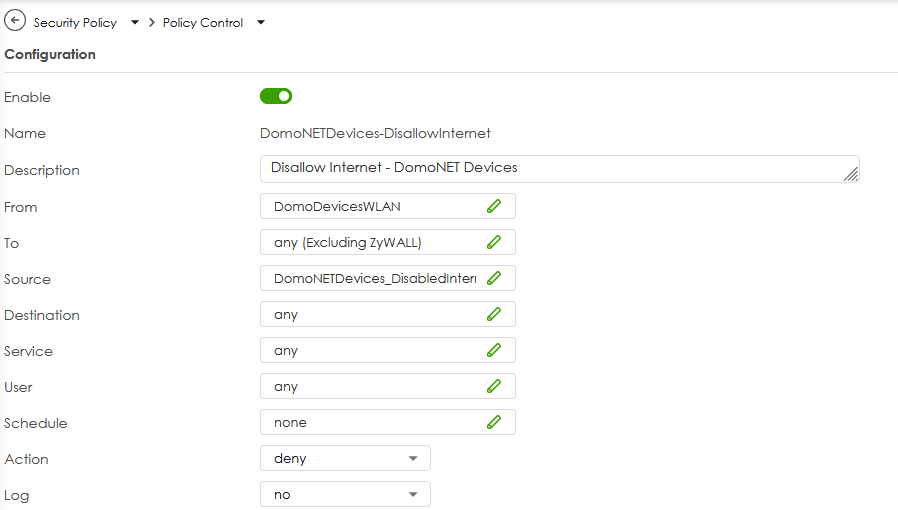
I have a dedicated Wifi VLAN used for all my IoT devices, and one of the custom rule, deny all the traffic from this VLAN to "Any" (excluding ZyWall) for any service, in which the Source IP is an object (IP Address list) and the destination is Any.
Obviously every IoT device have the own static IP Address defined into the DHCP Static list of the firewall.
Every night I shutdown my network devices (external access point — Zyxel NWA130BE — used also for the IoT devices, switch and firewall), and every morning I power on all of this AT THE SAME TIME (I have a power strip that supplies electricity for all devices at the same time)
The problem is that everytime I power up the network devices, in some cases (surely the last 3 days from today) one of the IoT device (unfortunately I can't prove if this is the case for everyone.), defined into the "DisabledInternet" source group, can reach internet for a limited period (seems for few seconds).
Report here one case:
I have an IoT device that read the electric power consumption in real-time and report this real-time value on its cloud platform and I would like to deny this connection (simply I don't like that these "personal" readings use the external cloud, since I can also read these readings locally).
So, all I did was create the Policy Control rule, and put the device's (static) IP address into the source address list
but…
I don't know why, for this device, every morning I receive a push notification on my phone, that indicate that this device is online, and when I open the app, I can read the real-time power consumption value assigned to some seconds before.
After that, it seems the device no longer has internet access, as I no longer have instant readings, and the last "good" one seems to be the only one. After some time, I also receive a notification that the device has been disconnected (probably after a timeout period during which the cloud service no longer receives data).
So… my question is: it's possible that the Policy Control rules start only after the interfaces are created? Because if we can assume:
- The firewall interface is created with DHCP Server and the associated port bring up.
- The access point connected to this port (which started up together with the firewall and has already started to connect the devices via Wi-Fi) starts the dialogue;
- The firewall interface boot up and the DHCP Server instanly serve IPs for this interface;
- My IoT device who is already connected to wifi (The access point startup takes much less time than the firewall startup) can instantly obtain the IP;
- My IoT device, that have received the IP can connect to internet;
- After that all of the interfaces are up&running, the Policy Control rules can be delivered stopping in this way the communication between the IoT device and WAN.
Can be this the problem?
Thank you
All Replies
-
So in short on boot up traffic is allowed for a bit then the Policy Control rules kick in?
Yes have seem this problem where when a reboot the FLEX inbound traffic over a bridge is allowed then after some time its blocked as per rules.
I guess the way to solve this is to get the USG ready then enable the interfaces.
0 -
Yes, exactly the same behaviour.
As per suggestion, I think that can could change the service startup sequence:
- Start the interface, without starting the DHCP Server;
- Start the Policy Control service;
- Start the DHCP Server for every interface that require the DHCP.
Or (maybe better):
- Start the interface, without activate ports;
- Start the Policy Control service;
- Activate all ports.
What do you think?
1 -
Yes having the Activate all ports (if enabled by config) after Policy Control would be a good idea.
0
Categories
- All Categories
- 441 Beta Program
- 2.9K Nebula
- 210 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 540 USG FLEX H Series
- 340 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 464 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 86 About Community
- 99 Security Highlight
 Guru Member
Guru Member





