802.1X authentication from Zyxel GS1900-8HP to Cisco ISE
Hello everyone,
I’m trying to get 802.1X authentication working from a Zyxel GS1900-8HP (firmware V2.90(AAHI.1)) to a Cisco ISE RADIUS server (v3.3.0.430 patch 4).
After several days of testing, I’m still completely unsuccessful.
Every authentication attempt fails with the following error:
Failure Reason: 5440 Endpoint abandoned EAP session and started newResolution: Verify known NAD or supplicant issues and published bugs. Verify NAD and supplicant configuration.Root cause: Endpoint started new authentication while previous is still in progress. Most probable that supplicant on that endpoint stopped conducting the previous authentication and started a new one. Closing the previous authentication.
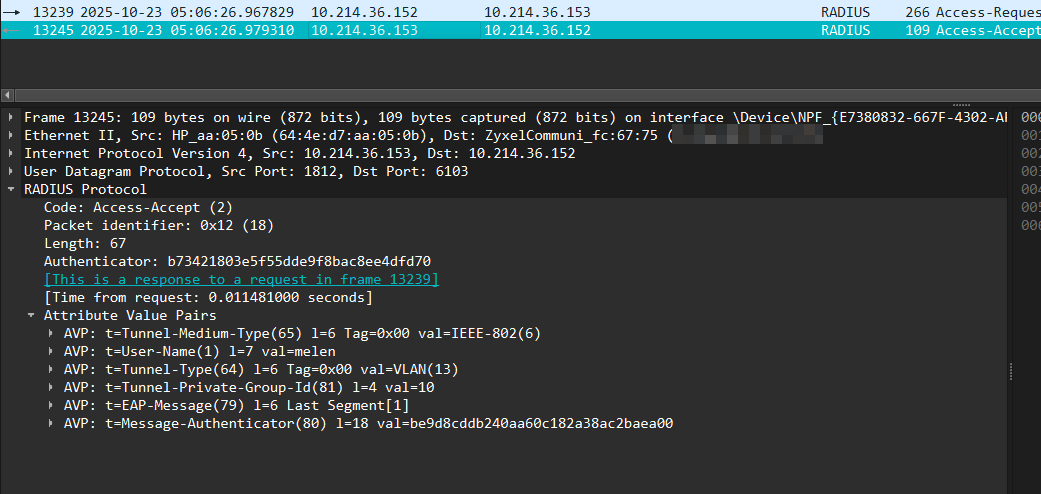
According to Wireshark, the Zyxel switch sends two authentication requests almost simultaneously.
The first one uses correct username and password, but fails with the error above (5440).
The second attempt starts immediately afterward, with incorrect credentials (USERNAME\USERNAME) and fails with:
Failure Reason: 11051 RADIUS packet contains invalid state attributeResolution: Check the network device or AAA client for hardware problems or known RADIUS compatibility issues; check the network connection to ISE for hardware problems.Root cause: The state attribute in the RADIUS packet did not match any active session.
Does this mean that the Zyxel switch does not handle AcsSessionID properly, which is mandatory for Cisco ISE?
Is there any known workaround for this issue?
The exact same computers authenticate successfully through an HPE 5130 switch using the same ISE server.
Here’s part of the current configuration:
interface 1
dot1x auto
no dot1x reauth
dot1x timeout quiet-period 120
dot1x timeout supp-timeout 60
dot1x max-req 5
dot1x guest-vlan
switchport hybrid pvid 7
switchport hybrid allowed vlan add 102 tagged
switchport hybrid allowed vlan add 7,200 untagged
switchport forbidden vlan add 1
spanning-tree link-type point-to-point
port-security address-limit 256 action discard
loop-guard action both
dot1x
radius host 172.16.xx.xx auth-port 1812 acct-port 0 key njNTsRqzU7Giow priority 0 retransmit 6 timeout 3 type all
P.S. I can log in to the web interface of the Zyxel switch using the same ISE users, via both RADIUS and TACACS+, without any issues. 😅
All Replies
-
Hi @Mutko
Please try to set these attributes to the account.
Tunnel-Type: VLAN Tunnel-Medium-Type: 802 Tunnel-Private-Group-ID: «VLAN ID»
Zyxel Melen0 -
Hi @Zyxel_Melen
Sorry, this didn't help :(
The connection drops before it even reaches the authorization policy, this is what I see in the ISE logs.
Zyxel log shows 6 sessions dropped, with new session every 4 sec.1
Oct 23 2025 16:25:43
Dot1X
notice
Port 1 authentication failed for client 178
2
Oct 23 2025 16:25:39
Dot1X
notice
Port 1 authentication failed for client 209
3
Oct 23 2025 16:25:35
Dot1X
notice
Port 1 authentication failed for client 78
4
Oct 23 2025 16:25:31
Dot1X
notice
Port 1 authentication failed for client 112
5
Oct 23 2025 16:25:27
Dot1X
notice
Port 1 authentication failed for client 142
6
Oct 23 2025 16:25:23
Dot1X
notice
Port 1 authentication failed for client 206
Can I send you a pcap?0 -
Hi @Mutko
Yes, please send the pcap, GS1900's tech support file, and the attribute you set on Cisco Radius.
Zyxel Melen0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 476 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Freshman Member
Freshman Member

 Zyxel Employee
Zyxel Employee