SWT – VLAN Ingress Check
 Zyxel Employee
Zyxel Employee


Overview
The VLAN Ingress Check is a network security and traffic control mechanism on Nebula-managed switches. It ensures that only traffic belonging to VLANs (Virtual LANs)assigned to a specific port is accepted.
If a packet enters a port that is not a member of the VLAN it claims to belong to, the switch drops that packet. This prevents unwanted or misrouted traffic from propagating through the network.
Starting from Nebula 19.20, the VLAN Ingress Check is enabled by default on all switch ports for newly created Nebula sites.
1. What Is VLAN Ingress Check?
When VLAN Ingress Check is enabled, the switch performs an incoming VLAN membership validation on every port:
- If the VLAN ID (VID) of the incoming packet matches one of the VLANs assigned to that port → Packet is accepted and forwarded.
- If the VLAN ID does not match any VLAN membership of that port → Packet is dropped.
This ensures that each port only handles VLAN traffic it is explicitly configured to belong to.
2. VLAN Membership Rules
A port is considered a VLAN member if it meets one of the following conditions:
Condition
|
Description
|
|---|---|
Fixed/Access port
| The port is manually assigned to a specific VLAN (e.g., Access VLAN 100). |
Trunk port
| The port allows multiple VLANs and accepts all VLAN-tagged traffic. By default, all VLANs are treated as members of the trunk port unless restricted. |
3. VLAN Ingress Behavior Explained
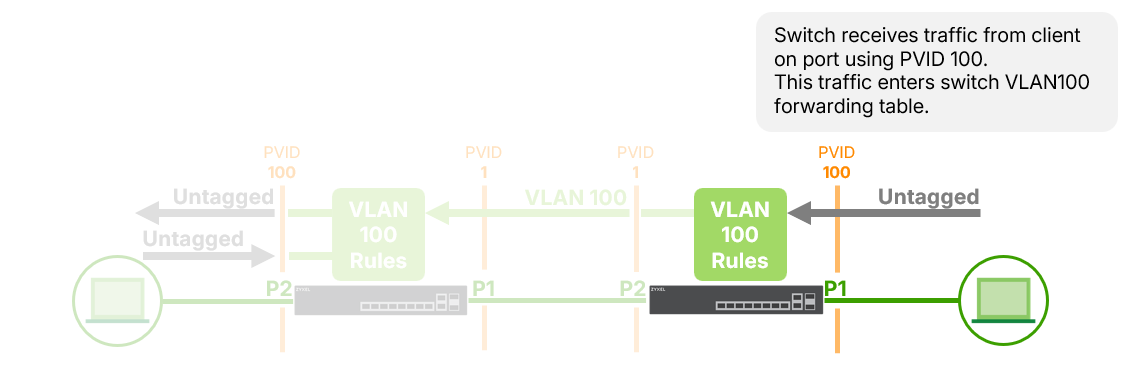
Example1: Access Port Receiving Untagged Traffic
- A laptop sends untagged frames to the switch via Port 1.
2. Port 1 is configured as Access VLAN 100.
3. The switch tags the incoming traffic with VLAN 100 internally and forwards it
according to VLAN 100’s forwarding rules.
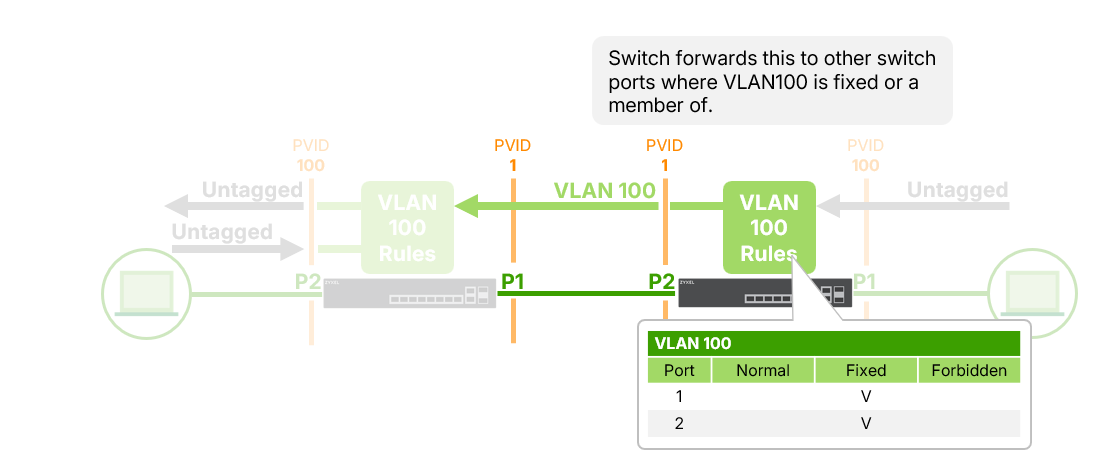
4. Traffic can exit from other ports that are also members of VLAN 100.
✅ Allowed traffic flow: Port 1 → Port 2(both are VLAN 100 members)
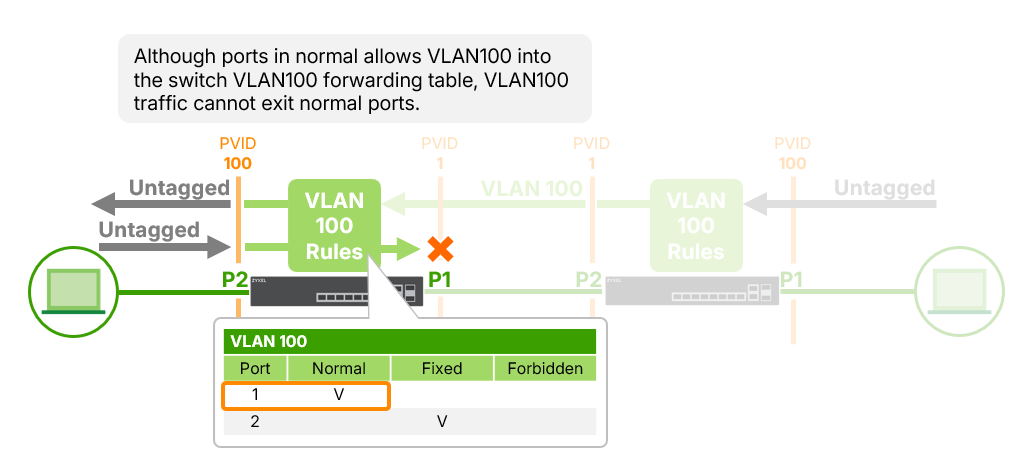
Example2: Port Not in VLAN Member List
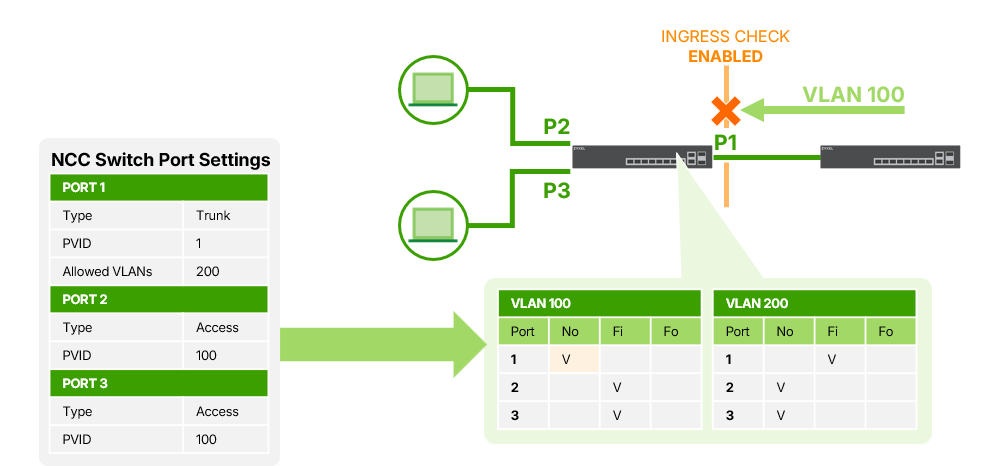
If Port 1 is not a member of VLAN 100 (set to “None”), and it receives VLAN 100 traffic:
- Ingress Check Disabled:
The switch still forwards the traffic if other ports (e.g., Port 2 or 3) are
members of VLAN 100.
- Ingress Check Enabled:
The switch drops the incoming VLAN 100 traffic immediately because Port 1 is
not a valid member of VLAN 100.
❌ Dropped traffic: Port 1 (non-member) →VLAN 100 packet rejected
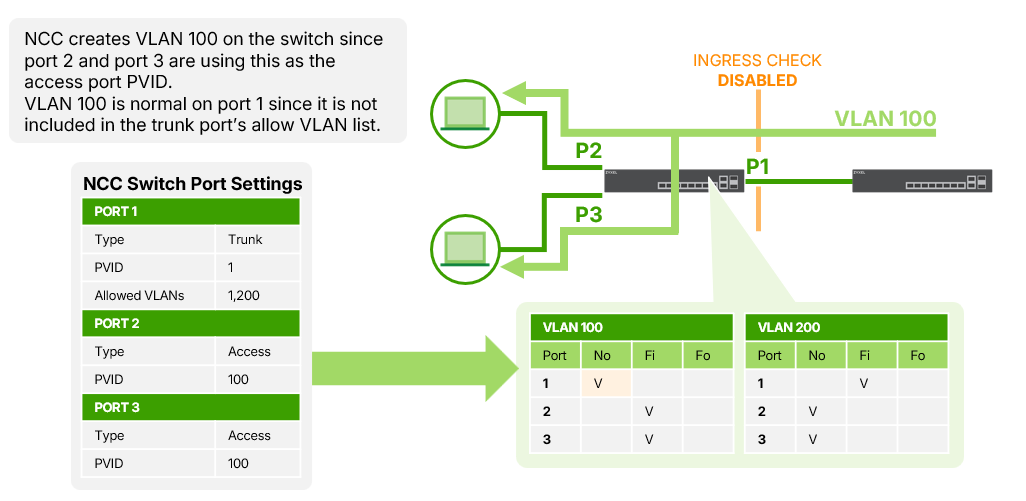
Example3: Trunk Port Behavior
If Port 1 is configured as Trunk (allow all VLANs):
- All VLANs are considered members of Port 1.
- VLAN Ingress Check allows all VLAN-tagged traffic to pass.
- For example, traffic tagged with VLAN 100 entering Port 1 is accepted and forwarded to any port that is a member of VLAN 100.
✅ Allowed traffic flow: Port 1 (Trunk) →Port 3 (Trunk, VLAN 100 allowed)
4.Default Behavior in Nebula
Site Creation Time
|
VLAN Ingress Check Default
|
Notes
|
|---|---|---|
After Nebula 19.20 release | Enabled on all ports
| Automatically provisioned to all managed switches |
Before Nebula 19.20 release | Enabled automatically after upgrade | Applies to all supported switch models. |
Exception
| Older models (e.g., NSW100/NSW200) | These two models do not support the VLAN Ingress Check feature. |
5. How to Verify VLAN Ingress Check Status
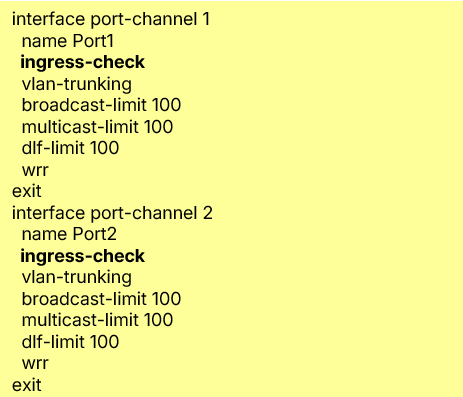
You can confirm VLAN Ingress Check status directly on the switch via CLI:
show configuration
Example Output (Before 19.20):
Port 1 & Port 2 do not display and ingress-check information
ExampleOutput (After 19.20):
Port 1 & Port 2 display ingress-check enabled
This confirms that VLAN Ingress Check is now active on the switch ports.
6.Impact on Network Behavior
- Traffic filtering: Prevents mis-tagged or unauthorized VLAN traffic from being accepted.
- Improved network security: Ensures ports only handle VLANs they belong to.
- No user impact: Since non-member ports should not receive traffic for unrelated VLANs, enabling this feature does not disrupt normal operations.
- Automatic provisioning: No manual action is required after Nebula 19.20 — the configuration is applied automatically to all eligible switches.
7.Summary
Aspect
|
Description
|
|---|---|
Feature Name | VLAN Ingress Check |
Function
| Ensures incoming VLAN traffic matches port membership |
Default Status | Enabled for all ports (from Nebula 19.20) |
Supported Models | All Nebula Cloud Switches except NSW100/NSW200 |
Configuration Access | Automatically managed by NCC |
Verification | CLI: show configuration |
Network Impact
| Enhances VLAN integrity and prevents misrouted traffic |
To sum up, VLAN Ingress Check enforces VLAN membership validation for each port, ensuring traffic integrity and preventing untagged or misassigned VLAN packets from passing through the switch.
From Nebula19.20, this security mechanism is automatically enabled by default on all Nebula-managed switches, improving reliability and network segmentation with zero additional setup required.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 601 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 480 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight