Remote Access VPN Support NCAS
 Zyxel Employee
Zyxel Employee



USG FLEX H Series Firewall has expanded its cloud-managed capabilities by integrating Nebula Cloud Authentication Service (NCAS) into its Remote Access VPN solutions. This enhancement enables administrators to manage VPN user credentials directly from Nebula Control Center (NCC) without relying on local databases or external authentication servers.
This article explains how NCAS works for VPN and setup procedures.
1. What Is Nebula Cloud Authentication (NCAS)?
NCAS allows administrators to create and manage user accounts entirely in the cloud, bypassing the need for on-premises servers or the firewall’s local database. With this integration, NCAS can now be used as the authentication server for:
- SSL VPN
- IPSec Remote Access VPN
This is especially useful for businesses that do not have an existing Active Directory (AD), RADIUS, or LDAP infrastructure.
2. Where to Configure NCAS for VPN
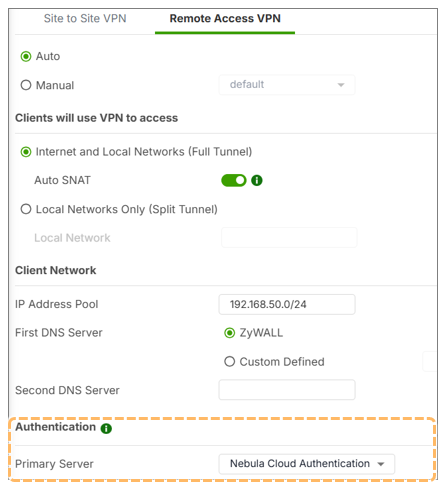
You can set NCAS as the authentication method in Nebula, under the Authentication Server section, simply select:Nebula Cloud Authentication
Note: Only one primary authentication server is allowed when using NCAS. Secondary servers cannot be added in this setup.
3. Creating VPN Users with NCAS
You can create cloud authentication users in two places:
Option A: Directly from the Remote Access VPN Settings
- Go to Remote Access VPN in Nebula
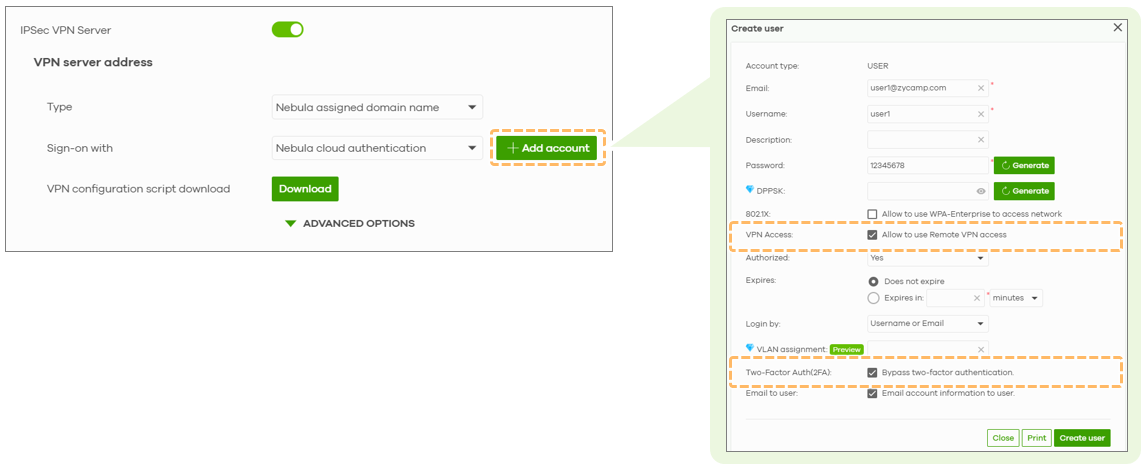
- Enable IPSec VPN Server
- Under authentication, select Nebula Cloud Authentication
- Click “Add Account”
- Enter email address and username
- By default, VPN access is enabled
This is the easiest method and automatically prepares users for VPN connection.
Option B: From the Cloud Authentication User Page
- Navigate to Site-wide > Configure > Cloud Authentication
- Click “Add User”
- Fill in user details
By default, VPN access is disabled here - make sure to enable the option “Allow user to use Remote Access VPN.”
4. VPN Connection: Using the Configuration Script
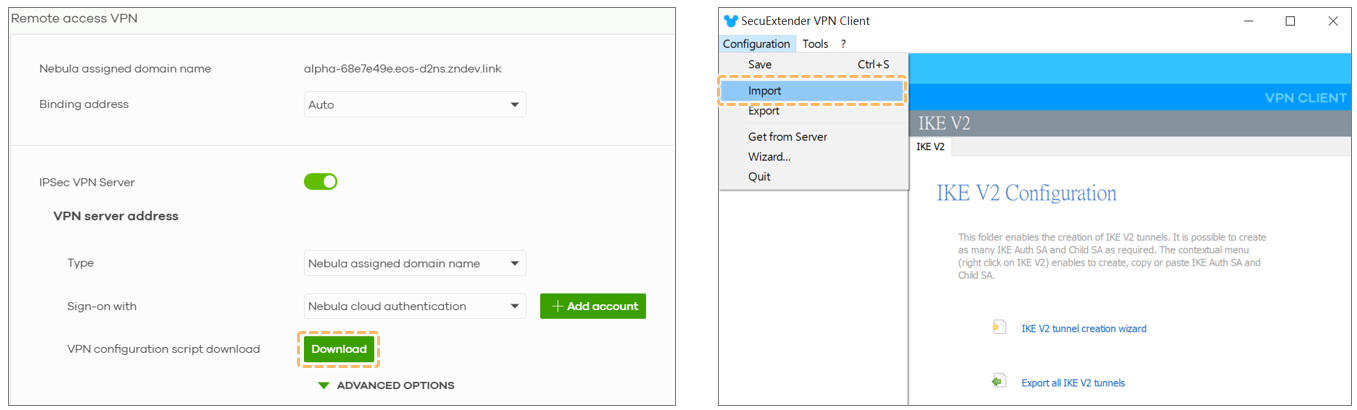
Once users are created, they can download the VPN configuration script:
- Click “Download” in the Remote Access VPN section
- Import the file into either:
- SecureExtender (Zyxel’s official VPN client)
- Native OS VPN clients (requires manual import)
This configuration script includes all necessary parameters for establishing a secure VPN tunnel.
5. Login Verification and Monitoring
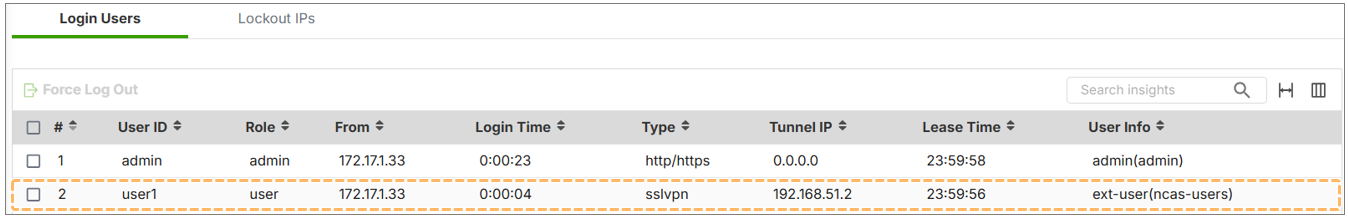
You can verify user login in Login User, Once the VPN is connected, the user information will include the NCAS user type
Login Users Monitor
- Shows active VPN sessions
- Lists the username, IP, and login type (ncas-users)
6. Current Limitations
While NCAS simplifies VPN management, there are a limitation, Two-factor authentication is not currently supported. It will be implemented in the future firmware.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight