Issue with WLAN 802.1x AD authentication
Having USG 700H and trying to setup 802.1x authentication of wifi clients on managed APs, but something doesn't work.
- AD server is setup under User Authentication and working (user lookup is ok)
- New user of type ext-group-user is created using AD definition and it also works fine using required group membership identifier.
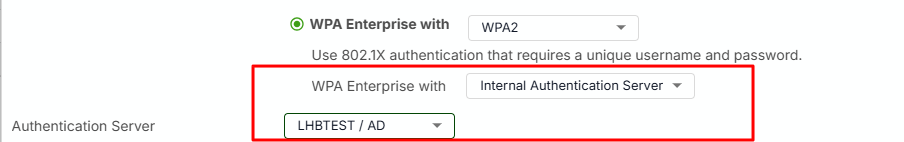
- SSID is setup for WPA2(3)-Enterprise set as "WPA Enterprise with = Internal Authentication server" and "Authentication server = AD configured above".
When I try to login on SSID and put known credentials it doesn't work. I checked FW and there are no rules trigger/no traffic is observed on AD interface. Logs says almost nothing:
AP log: User test (MAC: <OUI>) 802.1X auth failed on interface wlan-2-2.(Server: 10.50.200.1:1812)
Debug level: kernel [193934.502729] Can't find user (mac-users) profile in KUser_head
Not sure if debug log is related, but it is generated at the time I try to authenticate and reading message and observing no traffic to AD server it looks like the entire config doesn't work.
I'm aware that purely AD server is not enough to use .1x authentication, but my understanding is AP controller acts as internal RADIUS component interacting with external AD.
I've checked FAQ here and an example how to setup the config in subject is very similar to what I've done with some differences related to old GUI.
Not sure though if any specific configuration of AD is required.
Any ideas?
Best Answers
-
Hi @Rösti
Please help to check if you have done the join af domain process. Please navigate to the user & authentication > user authentication page to select you AD server and click the join domain button.
Zyxel Melen0 -
Hi @Rösti
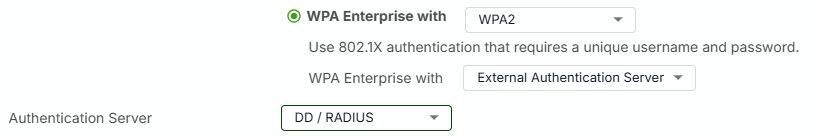
Yes, you can setup the external RADIUS server with the AD NPS and apply WPA enterprise with external RADIUS server.
The authentication server option in the SSID setting will be like this:
Zyxel Melen0
All Replies
-
Hi @Rösti
I did a local lab with the latest firmware version and get the same result as yours. I'm checking on this and will update you once I get further information.
Zyxel Melen0 -
Hi @Rösti
Please help to check if you have done the join af domain process. Please navigate to the user & authentication > user authentication page to select you AD server and click the join domain button.
Zyxel Melen0 -
Hello @Zyxel_Melen,
The AD host is within an external trusted network, I have no rights to onboard the firewall there. Is it required?
0 -
Hi @Rösti
If you use WPA Enterprise with internal Authentication server with AD server, you have to finish the join domain process, or the firewall can't help your AP to check the user with AD server.
Zyxel Melen0 -
Hello @Zyxel_Melen,
Ok, thanks. Would be great to have your manuals updated though.
What would be an alternative option then to utilize existing AD accounts? An external RADIUS server connected to bespoken AD, like Windows NPS, for example?
0 -
Hi @Rösti
Yes, you can setup the external RADIUS server with the AD NPS and apply WPA enterprise with external RADIUS server.
The authentication server option in the SSID setting will be like this:
Zyxel Melen0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 589 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 478 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Freshman Member
Freshman Member

 Zyxel Employee
Zyxel Employee