How to Configure 802.1x EAP-TLS to Secure the Wireless Environment with Third-party CA Certificate?
 Zyxel Employee
Zyxel Employee


This example shows how to use Android/iOS phone import the third-party certificate to get the wireless connection with 802.1x EAP-TLS protected. We need a certificate which is purchasing by the third-party CA.
Configure Certificate
1 Generate certificate request on the NXC. Go to CONFIGURATION > Object > Certificate > My certificates, and add a request certificate. In Subject Information, Set the NXC’s IP in the Host IP Address.
In Enrollment Options, select Create a certification request and save it locally for later manual enrollment.
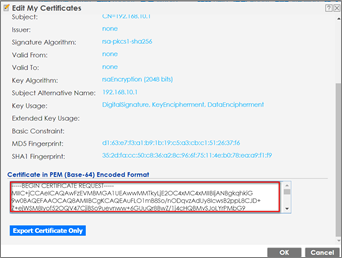
2 Double click the certificate and scroll down the page to copy the Base-64 code, then provide it to the third-party certificate company.
3 After receiving the certificate, import the NXC identity certificate into “My Certificates”, and the REQ certificate will be changed to CERT automatically. Go to CONFIGURATION > Object > Certificate > My Certificates > Import.
4 Import the root CA and Intermediate CA’s certificate (if exits) into “Trusted Certificate”. Go to CONFIGURATION > Object > Certificate > Trusted Certificates > Import.
5 Import the station identity certificate, root CA and Intermediate CA’s certificate (if exits) into the Android/iOS phone. (The station could download the certificates from email, dropbox or a cloud storage space).
Andriod: In step “e”, the Credential use must select Wi-Fi.
a
b
c
d
e
f
g
iOS: The way is same as import self-signed certificate.
a
b
c
d
e
f
g
h
i
Configure AP profile
1 Go to CONFIGURATION > Object > AP Profile > SSID> Security List, and add a Security profile.
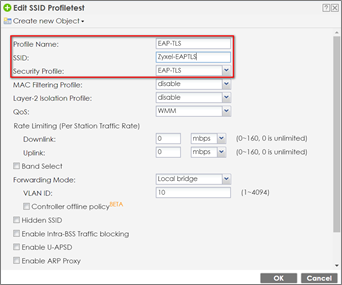
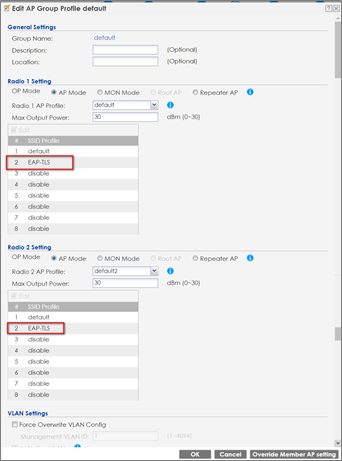
2 Go to CONFIGURATION > Object > AP Profile > SSID> SSID List, and add an SSID profile.
3 Go to CONFIGURATION > Wireless > AP Management > AP Group, and add this SSID into the default group.
Configure Auth. Server
1 Change the certificate to NXC identity certificate from third-party CA. Go to CONFIGURATION > System > Auth. Server > Auth. Server, and the Authentication Server Certificate select NXC.cer.
Comments
-
Test the Result
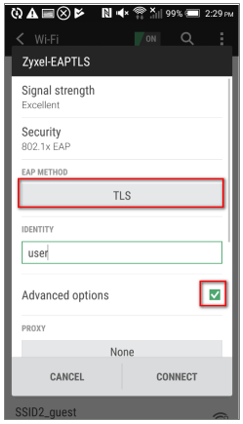
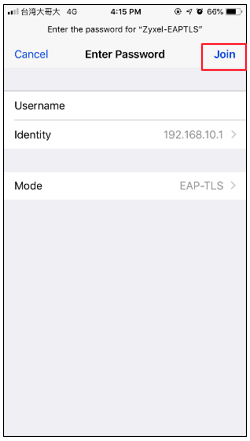
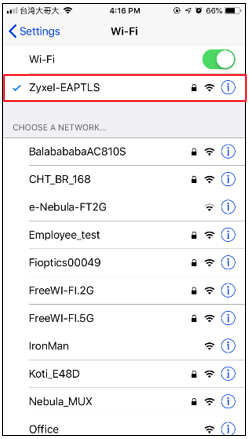
1 Use Android/iOS phone and connect to the SSID Zyxel-EAPTLS.
Android: In step “c”, please select root CA’s certificate in “CA CERTIFICATE” Column and select station identity certificate in “USER CERTIFICATE”
a
b
c
d
e
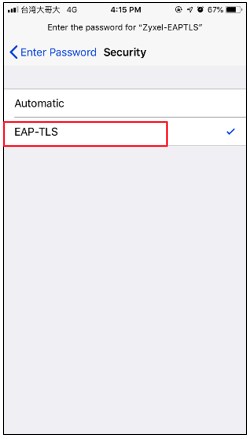
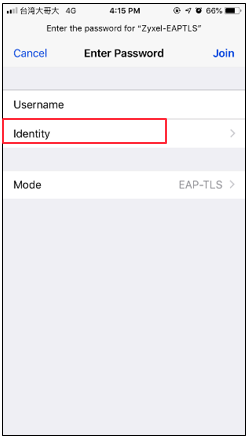
iOS: In step “e”, please select the station personal certificate from CA.
a
b
c
d
e
f
g
i
2 Check the station information On NXC station info. Go to Configuration > Wireless > Station info.
What Could Go Wrong?
1 User must import the certificate correctly on each device.
NXC: Root/Intermediate CA’s certificate > Trust Certificate; NXC’s certificate > My Certificate;
Station: Root/Intermediate CA’s Certificate > Trusted CA list; Stations’ personal certificate > Personal Certificate.
2 When pressing disconnecting on the Android phone, we might need to import the certificates again.
3 Different Android firmware versions may have different certificate importing behavior. Please ensure the certificates are imported successfully.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 476 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight