LACP-Portchannel with VLANs between GS1920-24HPv2 and Fortigate-Firewall
Hello everyone,
first of all - happy new.
I'm trying since a couple of days to achieve the following.
A portchannel (2 ports) on my Fortigate containing 4 VLANs (VLAN2, 10, 199, 222) should be connected to a portchannel on my Zyxel-Switch and on the switch i would need to have some ports in each of the vlans. Subnet/VLAN-definition and DHCP is done on my fortigate.
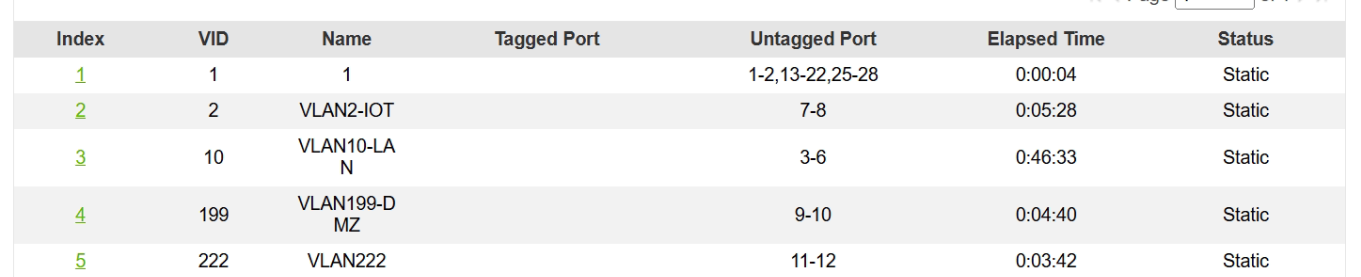
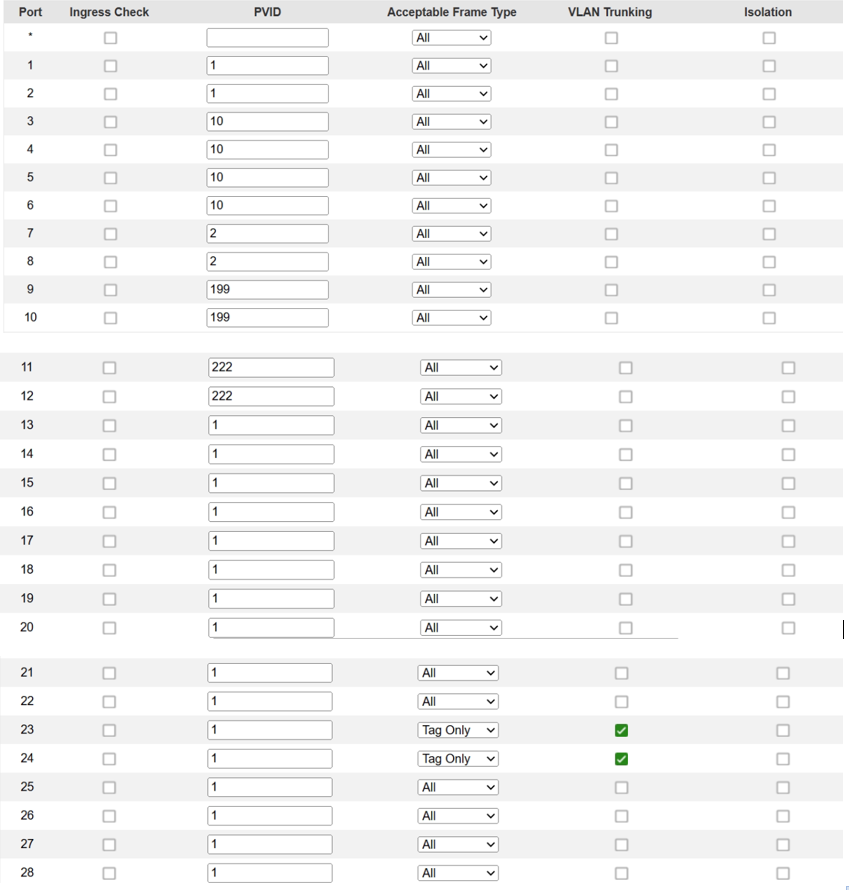
I have created the LACP on firewall and on switch. On the switch the ports for the LACP are set to trunking, VLAN1 is forbidden on trunk-ports as well as on the ports which should belong to the VLANs. PVID is set on the ports corresponding to VLAN-ID.
Firewall policies and DHCP-Scopes are there.
According to CLI on Fortigate LACP-Portchannel is working and on switch it is showing active.
the vlans
VLAN-Port-Setup
DHCP-Snooping is not enabled.
Hardware
Fortigate FGG80E running on 7.2.12
Zyxel GS1920-24HPv2 running on V5.00(ABMI.2) | 09/24/2025
I'm sure i'm doing something but i can't figure out what 😐️
Any help is very much appreciated.
Many thanks to all
All Replies
-
Hi @Ribwutz,
VLAN trunking is enabled on switch ports 23 and 24. However, enabling this feature only allows the switch to forward unknown VLAN traffic. You have created VLANs 2, 10, 199, and 222, so these are known VLANs, not unknown VLANs.
The easiest solution is to tag ports 23 and 24 for all of your VLANs except VLAN 1.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 589 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Freshman Member
Freshman Member