How to configure a whitelist for remote management to prevent unauthorized access
Options
Zyxel_Arisa
Posts: 25  Zyxel Employee
Zyxel Employee



 Zyxel Employee
Zyxel Employee


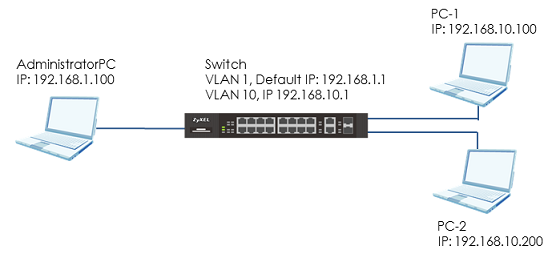
The example shows administrators how to configure a whitelist for host
devices that prevents attempted access from unauthorized devices or subnets.
The whitelist inspects the source IP addresses of hosts and the types of services
accessing the switch (Ex: Telnet, FTP, HTTP…..).
Note:
All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses and subnet masks. This example was tested using XGS4600-32 (Firmware Version: V4.50).
1. Configure the whitelist of the remote management
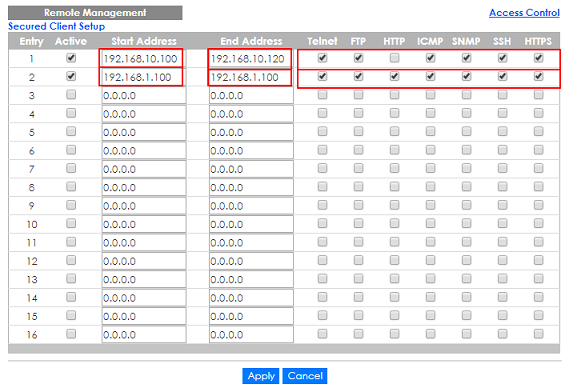
1-1. Enter the web GUI and go to Menu > Management > Access Control > Remote Management > Click Here using AdministratorPC. Enter the range of IP addresses and the corresponding types of services that are allowed to access the Switch. Then click “Apply”.
2. Test the Result
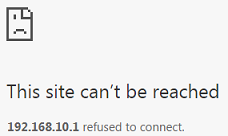
2-1. In the setting, we set the IP range: 192.168.10.100-192.168.10.120, which is allowed to access the Switch by all protocol types, EXCEPT HTTP. Therefore, if we use PC-1 (192.168.10.100) to access the Switch by HTTP, the Switch will refuse the connection. If we try to access the web GUI by HTTPS (Enter the https://192.168.10.1), PC-1 can connect to the Switch successfully.
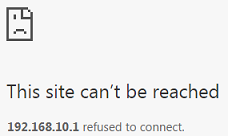
2-2. The PC-2 (192.168.10.200) is not in the range which is allowed to access the Switch. PC-2 cannot access or ping the switch’s management IP address.
2-3. AdministratorPC can access the Switch by all service types successfully.
3. What could go wrong?
3-1. The IP address is setting up repeatedly, but the setting is different. The logic rule of whitelist is OR.
For example, if we set the range of the IP addresses shown below. 192.168.10.120 is repeatedly set up accidently. The result is that all types of services are ALLOWED for 192.168.10.120.
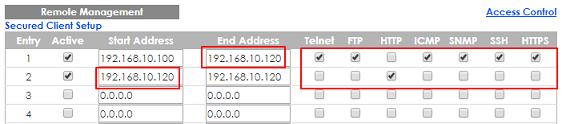
3-2. If the administrator has forgotten or lost track of the whitelisted IP addresses, the administrator will not be able to access the Switch. To solve this problem, use Console to verify the settings. Administrators can find out which IP addresses are allowed to access the Switch by reviewing the running configurations.
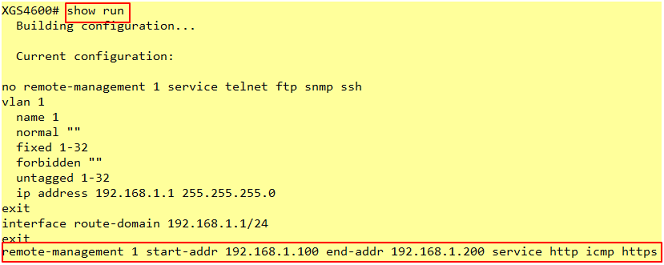
Note:
If the Switch does not support Console, please check the manual of your Switch model to find out how to restore device to factory default settings.

Note:
All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses and subnet masks. This example was tested using XGS4600-32 (Firmware Version: V4.50).
1. Configure the whitelist of the remote management
1-1. Enter the web GUI and go to Menu > Management > Access Control > Remote Management > Click Here using AdministratorPC. Enter the range of IP addresses and the corresponding types of services that are allowed to access the Switch. Then click “Apply”.

2. Test the Result
2-1. In the setting, we set the IP range: 192.168.10.100-192.168.10.120, which is allowed to access the Switch by all protocol types, EXCEPT HTTP. Therefore, if we use PC-1 (192.168.10.100) to access the Switch by HTTP, the Switch will refuse the connection. If we try to access the web GUI by HTTPS (Enter the https://192.168.10.1), PC-1 can connect to the Switch successfully.

2-2. The PC-2 (192.168.10.200) is not in the range which is allowed to access the Switch. PC-2 cannot access or ping the switch’s management IP address.

2-3. AdministratorPC can access the Switch by all service types successfully.
3. What could go wrong?
3-1. The IP address is setting up repeatedly, but the setting is different. The logic rule of whitelist is OR.
For example, if we set the range of the IP addresses shown below. 192.168.10.120 is repeatedly set up accidently. The result is that all types of services are ALLOWED for 192.168.10.120.

3-2. If the administrator has forgotten or lost track of the whitelisted IP addresses, the administrator will not be able to access the Switch. To solve this problem, use Console to verify the settings. Administrators can find out which IP addresses are allowed to access the Switch by reviewing the running configurations.

Note:
If the Switch does not support Console, please check the manual of your Switch model to find out how to restore device to factory default settings.
Tagged:
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 220 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 602 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight