How to configure the switch & RADIUS server to implement 802.1x Port-auth w/ Dynamic VLAN Assignment
 Zyxel Employee
Zyxel Employee



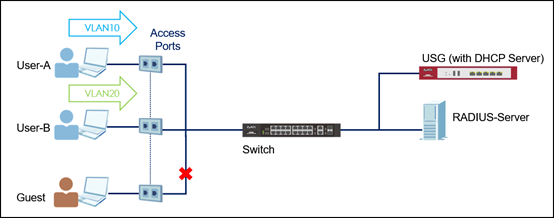
Zyxel switch models support 802.1x Port Authentication that forces hosts to submit valid user credentials to be authenticated by an authentication server (In this case would be RADIUS Server) before their traffic can be forwarded across the switch.
Dynamic VLAN Assignment, a variation of Port Authentication, allows host traffic to be processed in specific VLAN based on the submitted user credentials regardless of the PVID. This can be done by adding certain attributes in the user profile
Below example will instruct the administrator on how to configure the Switch and RADIUS Server to allow host traffic to be processed in a specific VLAN based on the submitted user credentials.
The USG provides dynamic IP address configurations for Hosts in VLAN 10 and VLAN 20:
- If Host enters the “VLAN10” user credentials, Host is going to receive a dynamic IP address for network 192.168.10.0/24.
- If Host enters the “VLAN20” user credentials, Host is going to receive a dynamic IP address for network 192.168.20.0/24.
- If Host enters an invalid credential, Host is not allowed to communicate across the Switch.
In the example, Host A and B will get different network IP via Dynamic VLAN Assignment based on the submitted user credentials. Flexible network segmentation and management can be implemented accordingly.
Note:
All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses and subnet masks. The authentication server in this example is running TekRADIUS Manager in PC, and GS1920-24HP for the Switch.
1. Configuration in the Switch
1-1. Access the web GUI of the Switch.
1-2. Go to Advanced Application > VLAN > VLAN Configuration > Static VLAN Setup.
1-3. Create VLAN 10, 20 for Hosts, and VLAN 100 for RADIUS server.
1-4. Go to Advance Application > VLAN > VLAN Configuration > VLAN Port Setup.
1-5. Configure PVID 100 for the port connected to RADIUS server.
1-6. Go to Basic Setting > IP Setup.
1-7. Configure the IPs for VLAN 10, 20, and 100.
1-8. Go to Advance Application > AAA > RADIUS Server Setup.
1-9. Input the RADIUS Server’s IP address and set the Shared Secret as “12345”.
1-10. Go to Advance Application > AAA > AAA Setup.
1-11. Check Dot1x under the Authorization section.
1-12. Go to Advance Application > Port Authentication > 802.1x.
1-13. Activate Port Authentication on the ports connected to Hosts.
Note:
Guest VLAN (please refer to How to configure the switch to send unauthorized users in a Guest VLAN) can be also added to isolate the unauthorized users.
2. Configuration in the RADIUS Server
2-1. Access the RADIUS Server.
2-2. Edit the Client profile for the Switch.
Note:
The client IP address and secret must match the management IP and shared secret of the switch.
2-3. Edit the User profile for Host credentials and attributes (VLAN ID).
2-4. Restart the TekRADIUS service to refresh the settings.
3. Test the Result
3-1. Regarding the 802.1x configuration on Windows OS, please refer to How to Configure Switch and RADIUS server to Provide Network Access through 802.1x Port Authentication.
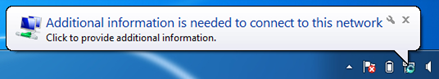
3-2. Connect Host A PC to port 1 of the Switch, it should show “Additional information is needed to connect to this network” on Host A PC.
3-3. Enter the username (vlan10) and password (vlan10user) which must be consistent with the RADIUS server’s user profile settings.
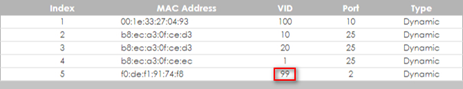
3-4. Access the Switch and go to Maintenance > MAC Table. Check the MAC table on the switch, Host A should be assigned with VLAN ID 10.
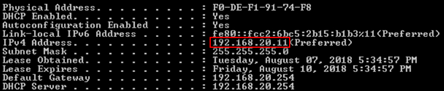
3-5. Host A gets the dynamic IP 192.168.10.X in VLAN 10 from DHCP Server on the USG.
3-6. Connect Host B PC to port 2 of the Switch, it should show “Additional information is needed to connect to this network” on Host B PC.
3-7. Enter the username (vlan20) and password (vlan20user) which must be consistent with the RADIUS server’s user profile settings.
3-8. Access the Switch and go to Maintenance > MAC Table. Check the MAC table on the switch, Host B should be assigned with VLAN ID 20.
3-9. Host B gets the dynamic IP 192.168.20.X in VLAN 20 from DHCP Server on the USG.
Note:
The priority of Dynamic VLAN Assignment is higher than the PVID on Switch. This means if you intend to use the PVID on certain port, you should submit with user credentials including no VLAN ID attribute assignment.
4. What Could Go Wrong
4-1. Make sure you create the specific VLAN in advance regarding the VLAN ID you want to dynamically assign by 802.1x Port Authentication.
4-2. The shared secret, usernames, and passwords are all case-sensitive. Make sure that users input the correct lower-case or upper-case characters. Invalid credentials will be forbidden to access the Switch or isolated to Guest VLAN with limited network resources.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 220 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 602 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight