ZyWall USG200 L2TP VPN Issues
Hello,
I am trying to configure a L2TP over IPSec VPN to give access to the office network for remote workers. I have been following all the tutorials to configure this manually, and I have also used the Wizard in attempting to do this.
Each time the Phase 2 authentication fails.
Is it any known issue or is the firmware too old for modern encryption and authentication algorithms?
Current Version of the firmware is : 3.30(AQU.7)
All Replies
-
Hi @DeePee
The purpose of Phase 2 negotiations is to establish the Phase 2 SA (sometimes called the IPSec SA). The IPSec SA is a set of traffic specifications that tell the device what traffic to send over the VPN, and how to encrypt and authenticate that traffic. In Phase 2 negotiations, the two peers agree on a set of communication parameters.
The Phase 2 proposal includes the IP addresses that can send traffic over the tunnel, and a group of encryption and authentication parameters. Device sends these parameters in a Phase 2 proposal. The proposal includes the algorithm to use to authenticate data, the algorithm to use to encrypt data, and how often to make new Phase 2 encryption keys.
The items you can set in a Phase 2 proposal include:
Type
You can select the type of protocol to use: Authentication Header (AH) or Encapsulating Security Payload (ESP). ESP provides authentication and encryption of the data. AH provides authentication without encryption. I recommend you select ESP.
Authentication
Authentication makes sure that the information received is exactly the same as the information sent. You can use SHA1 or MD5 as the algorithm the peers use to authenticate IKE messages from each other. SHA1 is more secure.
Encryption
Encryption keeps the data confidential. You can select DES, 3DES, or AES. AES is the most secure.
Force Key Expiration
To make sure Phase 2 encryption keys change periodically, always enable key expiration.
So, as you say Phase 2 authentication fails, please verify the algorithm the peers use to authenticate (SHA1 or MD5) and verify it is configured on the Zyxel device.
I hope it helps.
Regards
0 -
Hi @DeePee,
After I check your configuration file, some settings for IPSec VPN and L2TP VPN are not correctly configured.
If you’d like to use Birou_VPN for L2TP VPN, you should modify the follow settings.
In Birou_VPN gateway:
In Birou_VPN connection:
The local policy must be the IP address of WAN 83.103.xxx.xxx.
In L2TP VPN, select Birou_VPN as the connection.
0 -
Thanks a lot. Unfortunately none of them work with default clients of Mac OS and iOS...
0 -
Hi @DeePee,
There should be default firewall rules for IPSec VPN.
It seems you delete the default rules.
Add the following rules:
From IPSec_VPN to any, allow
From IPSec_VPN to ZyWALL, allow
Enable the rule:
From WAN to ZyWALL
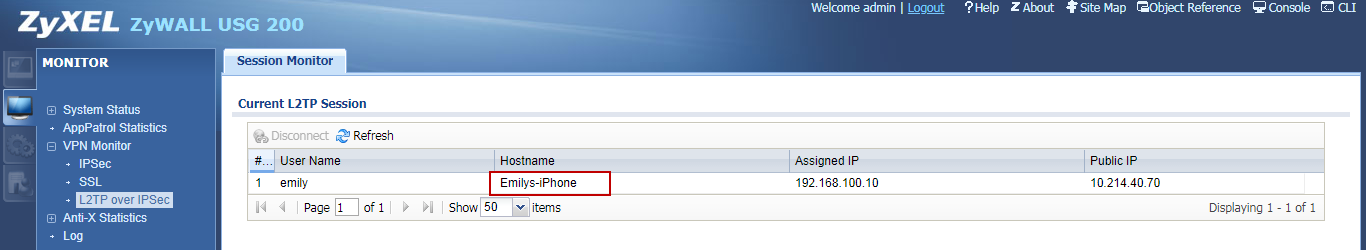
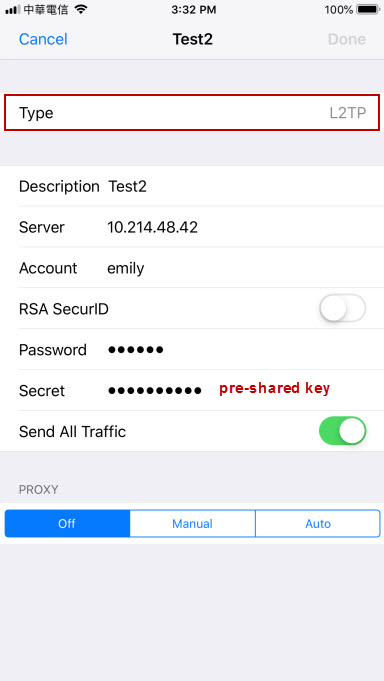
L2TP VPN is able to be connected on iPhone.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 602 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Freshman Member
Freshman Member
 Master Member
Master Member


 Zyxel Employee
Zyxel Employee