IKEv2 Client-To-Site and certificates
Hello,
I have a (probably general) question regarding IKEv2 authentication using certificates.
We set up a VPN100 appliance and got some client computers (Win10) able to connect through IKEv2 (internal Windows client). For this, I have created a self-signed certificate on the VPN100 and installed it in the clients' local machine account's certificate store Trusted Root Certification Authorities. (Procedure can be found at http://onesecurity.zyxel.com/img/uploads/Next-Gen_IKEv2_VPN_Server_Role_CR.pdf ).
Generally speaking, though: Assuming one of the laptops get lost or stolen, how could I prevent this specific device from connecting? As far as I can see, there is no way to have a per-device or even per-user certificate, is that correct? That would mean that when a computer is missing, I would have to create a new certificate and deploy it to every remaining laptop, is that correct? Obviously I could change the password for the user account in question, but that seems like a workaround, rather than a secure method to prevent intrusion into the VPN.
Is there any way to authenticate a per-device client certificate?
Thanks for any help,
Roland
All Replies
-
Hi @brischt,
You can configure Two Factor for VPN connection using Email or SMS.
Go to CONFIGURATION > Object > User/Group > username, add Email and Mobile Number.
Go to CONFIGURATION > Object > Auth. Method > Two-factor Authentication, select the check box Enable and IPSec VPN Access.
Move the IKEv2 users to selected user/group object.
Select the delivery settings: SMS, Email, or both.
Enter the WAN IP address or domain of VPN100.
Delivered by Email
Go to CONFIGURATION > System > Notification > Mail Server, enter SMTP server settings.
Delivered by SMS
Go to CONFIGURATION > System > Notification > SMS, enable SMS ,enter country code and your ViaNett account.
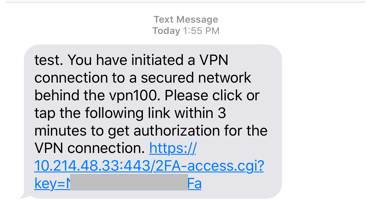
When IKEv2 VPN client connects, the user receives authorization by SMS or Email. The user is authorized only after clicking on the authorization link.
Email
SMS
0 -
hi,
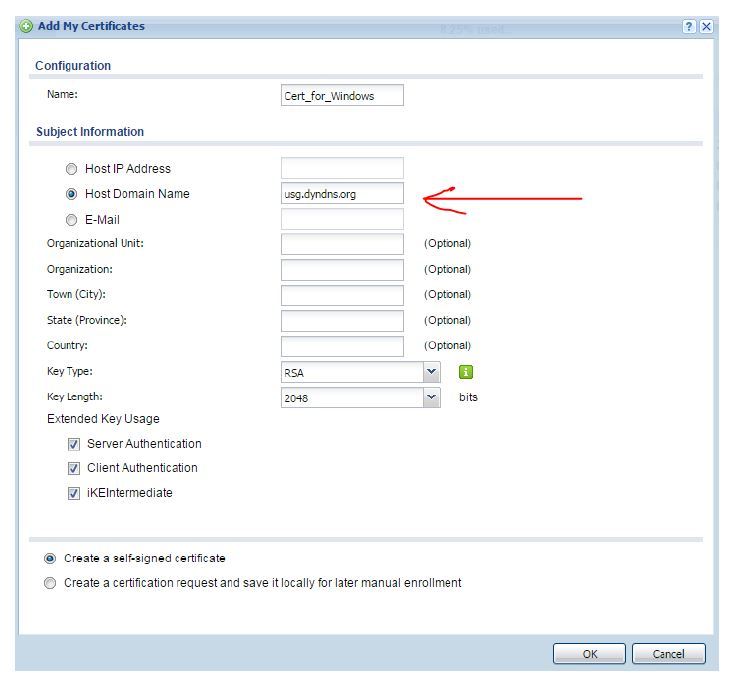
when I add a certificate what have to write in HOST DOMAIN NAME?
thanks
Damiano
0 -
Hi Damiano,
in case the question was directed at me: That should be the FQDN that points to your Zyxel box from external (it can be a dynamic DNS name). This is the name that clients will resolve into an IP address and then connect to, to establish a VPN. The Zyxel box then assures the client that it really is the endpoint the client wants to talk to through this certificate.
For example: vpn-mycompany.dyndns.org
or if you have your own domain mycompany.com and a static IP set up in DNS for the subdomain vpn: vpn.mycompany.com
Hope that helps,
Roland
0 -
hi Roland, thank you.
I have to connect from my notebook-house to the lan of my company. in my company behind usg 40 there is lan with a windows server 2019, the internal AD of my company is mycompany.local and internet domain is www.mycompany.com. my notebook-house have not static IP.
what do I do?
thanks
Damiano
0 -
Hi Damiano,
I believe you should use whatever FQDN resolves to your company's internet connection. It's hard to tell without more information on your network/DNS/domain setup.
- Is your Zyxel box directly connected to the internet, or is there a DSL/cable/something else router in between? If the latter, remember to forward the required ports from the router to the Zyxel box - UDP 4500 and UDP 500
- Do you have a static IP address on the internet connection in your company, or a dynamic one? If the latter, you need to set up a dynamic DNS resolver on the router that actually connects to the internet. Use that dynamic DNS host name then for the certificate's host domain name!
- If www.mycompany.com resolves to your company's internet connection (i.e., if your company runs their web servers on premise, not with a 3rd party provider/webspace/cloud), you probably have a static IP, and you could probably use that FQDN. However, I believe a cleaner solution could be to set up a subdomain vpn.mycompany.com and create according DNS entries to point to your company's IP address.
Hope this helps, otherwise maybe Zyxel support might be more qualified to answer your questions.
Kind Regards,
Roland
0
Categories
- All Categories
- 438 Beta Program
- 2.7K Nebula
- 188 Nebula Ideas
- 121 Nebula Status and Incidents
- 6.2K Security
- 454 USG FLEX H Series
- 303 Security Ideas
- 1.6K Switch
- 81 Switch Ideas
- 1.3K Wireless
- 44 Wireless Ideas
- 6.8K Consumer Product
- 278 Service & License
- 435 News and Release
- 88 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.2K FAQ
- 34 Documents
- 34 Nebula Monthly Express
- 85 About Community
- 91 Security Highlight
 Freshman Member
Freshman Member


 Zyxel Employee
Zyxel Employee