USG20W-VPN UDP Port 500 open
 Freshman Member
Freshman Member
I have a USG20W-VPN that is failing PCI Compliance. The scan shows UDP Port 500 as being open. I checked my NAT and security policy and there are no VPN rules setup. I even added a security policy to deny any traffic from the WAN to Port 500. I am using the expert mode through the web interface. I do not use any of the VPN functions of the router. I am not able to remove the IKE service that uses the UDP 500 port. How do I close this port so I can pass my PCI scan?
Thanks for the help,
Bill
All Replies
-
Hello Fitness_Bill,?
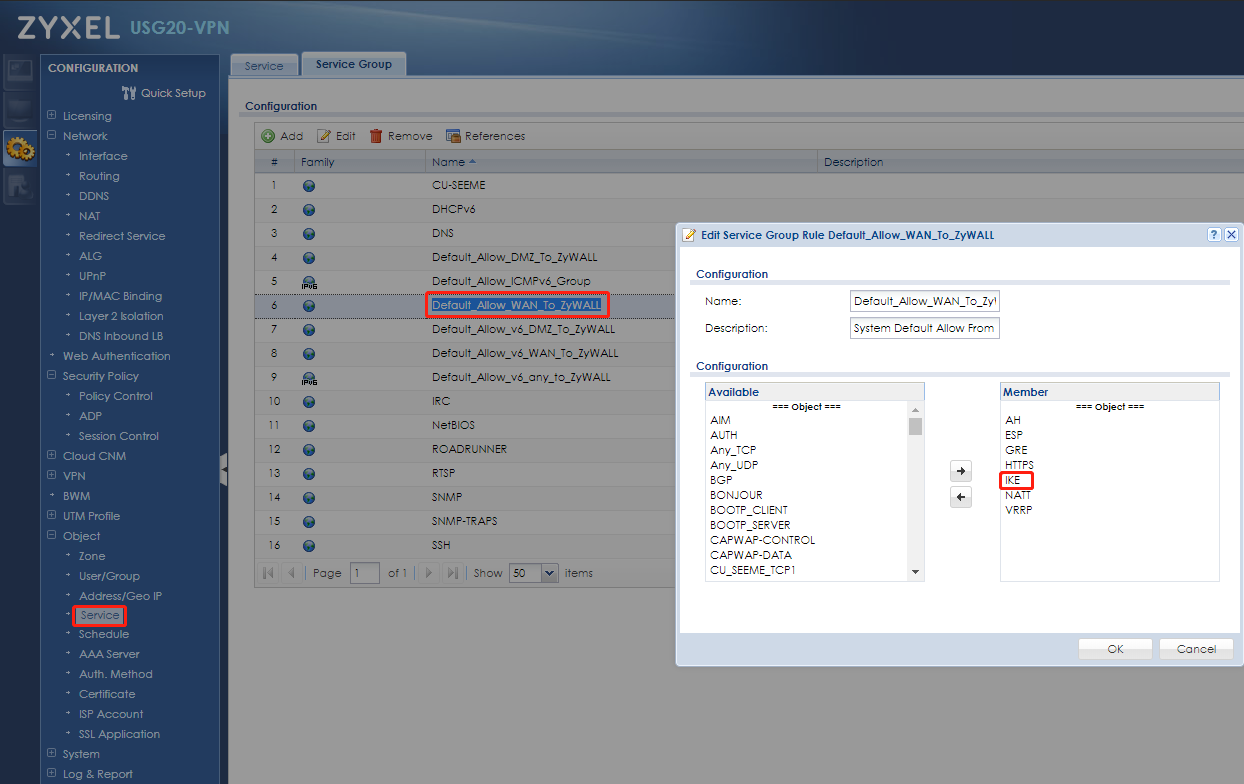
Just go to "service group" and remove IKE(udp 500) from service group "Default_Allow_WAN_To_ZyWALL" , because the service group is for wan to zywall security policy. it's allowed by default.
Service group
Security policy
0 -
I made the changes above and removed the IKE from both the IPv4 and IPv6 wan to Zywall. When I go out to and use websites to check the port it says TCP is filtered and the UDP is open/filtered.
0 -
I went so far to remove all references to IKE and Port 500. Once there were no references to port 500 I removed the service from the list.
Host is up. PORT STATE SERVICE 500/tcp filtered isakmp 500/udp open|filtered isakmp
This is what I got when I ran the scan using https://www.ipfingerprints.com/portscan.php
I was only checking Port 500
0 -
Hi @ Fitness_Bill,
The scan result is right for UDP. Since no response packets received.
You can refer this article of a well known scan program - NMAP.
Table 5.3. How Nmap interprets responses to a UDP probe
"Unfortunately, firewalls and filtering devices are also known to drop packets without responding. So when Nmap receives no response after several attempts, it cannot determine whether the port is
openorfiltered."The Internet is better guarded now, so Nmap changed in 2004 (version 3.70) to report non-responsive UDP ports as
open|filteredinstead.If you want the test result is "filtered".
Change your firewall rule action from "deny" to "reject".
The firewall will reply a "ICMP port unreachable" response.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Ally Member
Ally Member



 Master Member
Master Member



