VPN Configuration
I started a new thread as just now getting back to this and different questions
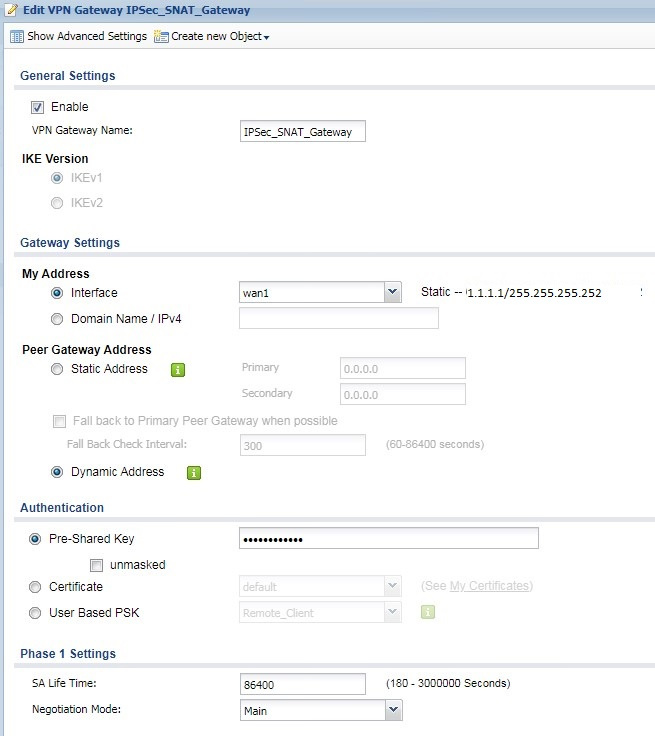
Here is the configuration of our ZyXELL 110
Above is a site to site, router to router VPN tunnel between offices which works just fine. Now I'm wanting to add a VPN client connection for remote access to people in the field. I've set it up as the following.
So, office "A" internal network is 192.168.0.0/21 and office "B" is 192.168.8.0/21 and the intention is to have the client give an address of 192.168.88.x and SNAT to 192.168.80.x because likely their connection would overlap our internal addresses.
After a bunch of trials, changing the Phase1 & Phase2 to match, only using 3DES & SHA-1 & DH2, I've gotten rid of the auth errors but now the ZyWALL VPN CLient is giving me Phase2 doesn't match again and the weird part is in the log it stated the site to site policy and not the client policy. I started out with the Win10 VPN client but installed the ZyWALL one for further tests.
Clearly something that I'm missing. Not that familiar with VPNs. I set the site to site a number of years ago. Any help appreciated.
All Replies
-
Hi @Costas
You may refer to this KB article which mention about how to implement SNAT in Site-to-Site IPSec VPN scenario to avoid local subnet overlapping problem.
https://kb.zyxel.com/KB/searchArticle!viewDetail.action?articleOid=014715&lang=EN
0 -
Sorry, had a number of other projects and now getting back to this. Due to the time delay and issues I thought it would be best to just start over so have deleted the prior gateway, client, and policy. I still have the office site-to-site VPN in place but all of the client stuff from above has been removed.
Created a new gw & client based on http://onesecurity.zyxel.com/img/uploads/Next-Gen_VPN%20with%20User%20Based%20PSK%20CR.pdf I can include shots of them if you wish.
What I did not do is on the bottom of page 11 to uncheck the box to “Use Policy Route to control dynamic IPSec rules” because we have rules for the office traffic.
Created a policy route for the source address of the group of authorized public IP's with the destination address of a new subnet (192.168.1.0/24) because I only need to communicate with that part of the super subnet (192.168.0.0/21).
Tried connecting with the built-in Windows VPN client but failed so went back to the ZyWALL client. I can establish the tunnel and it provides the client with a 10.10.10.10 address. If I look at the VPN IPSec monitor it shows connected with inbound traffic. If I attempt to ping 192.168.1.20 (a device I want to RDP to) I appear to get a response from the ping but the monitor shows no outbound traffic and when I try to RDP to it it fails to connect.
My guess is the policy route?
I figured best to start with a basic connection and then try to figure out the SNAT issue since my local subnet is 192.168.40.0/24 and I don't overlap the office subnets.
Thanks again,
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 211 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 545 USG FLEX H Series
- 341 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 52 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 465 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 87 About Community
- 99 Security Highlight
 Freshman Member
Freshman Member









 Zyxel Employee
Zyxel Employee




