ZyXEL USG Logs to remote server (especially AWS CloudWatch)
Options
Hi guys!
I am wondering (or even browsing the web and ZyXEL KB), if there is a possibility to send logs from ZyXEL device to remote server?
Hopefully, this is not all I can do(?):
https://kb.zyxel.com/KB/searchArticle!gwsViewDetail.action?articleOid=011800&lang=EN
More important question is, is there possibility to send it to AWS CloudWatch? Does anybody did something like this?
Thanks!
I am wondering (or even browsing the web and ZyXEL KB), if there is a possibility to send logs from ZyXEL device to remote server?
Hopefully, this is not all I can do(?):
https://kb.zyxel.com/KB/searchArticle!gwsViewDetail.action?articleOid=011800&lang=EN
More important question is, is there possibility to send it to AWS CloudWatch? Does anybody did something like this?
Thanks!
0
Accepted Solution
-
Thanks for reply @Blabababa and @Ian31 !
AWS CloudWatch uses their own CloudWatch agent, that's true.
Yesterday I connected it to Logentries - there is possible to use 'Plain TCP/UDP Forwarding (Legacy)', for more info, read here.
But it is crazy bad that ZyXEL doesn't have nothing better (secured), with security token or something!0
All Replies
-
I had tried to use syslog-ng on Raspberry Pi as my external log server and it works(using udp port 514).
Not sure what protocol and port AWS CloudWatch will use. Is it using the standard syslog port to receive the log from outside, too?1 -
I don't think USG can direct connect to CloudWatch now. Since need built-in the CloudWatch agent
into it.
The alternative solution is to install a syslog server on-premise or on AWS EC2, then install the CloudWatch agent on it, as a middleware to CloudWatch.
There also a lot of cloud hosting service for log management, which can save the effort to build your own.
0 -
Thanks for reply @Blabababa and @Ian31 !
AWS CloudWatch uses their own CloudWatch agent, that's true.
Yesterday I connected it to Logentries - there is possible to use 'Plain TCP/UDP Forwarding (Legacy)', for more info, read here.
But it is crazy bad that ZyXEL doesn't have nothing better (secured), with security token or something!0 -
-
Hi Pista, yes you can send the logging to one or more servers or desktops if you have them to capture the verbose logging from most ZYXEL appliances.
No need to waste time with overrated cloud stuff.. simply provision it locally at your home or business....
We do this with our clients with all zyxel USGxx's and also Zyxel L2 GS2210 managed switches to macOS servers.What you need:
- network host addressability and access to the logging servers
- a logging agent / task / daemon on the logging server the processes the logging from the USG i.e. ( use syslog-ng on macOS )
- optionally use another logging port other than the default port (UDP 514)
- a mechanism on the logger server(s) to "turnover' and remove older logs (/etc/newsyslog.conf)
Steps:
- set u[p a remote logger on the remote servers (FreeBSD, Centos, macOS etc etc ). We use syslog-nd from the mac ports website. There are few versions else use the native syslogd in the remote server.
- ensure the remote server permits access to port 514 (or the port you want to use) else set up another port to use in public end.
- allocate/configure remote directories to contain the syslog for each server. (i.e. path/to/usg60_002.log) and set the r/w access (ACL or chmod)
- verify that the remote host accepts access on the port. Here, port 64514 is used from macOS, freebsd11.2 and unbuntu18
macmini-02-server:~ warwick$ <b>sudo lsof -i :64514</b> COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME <b>syslog-ng</b> 237 root 10u IPv4 0x598b69fe9335fd05 0t0 UDP *:64514
macpro:~ warwick$ <b>nc -vnzu 10.0.99.12 64514</b> found 0 associations found 1 connections: 1: flags=82<CONNECTED,PREFERRED> outif (null) src 10.0.99.9 port 65154 dst 10.0.99.12 port 64514 rank info not available Connection to 10.0.99.12 port 64514 [udp/*] succeeded!<br>warwick@ubuntu18-01:/$ <b>nc -vnzu 10.0.99.9 64514;nc -vnzu 10.0.99.12 64514</b> Connection to 10.0.99.9 64514 port [udp/*] succeeded! Connection to 10.0.99.12 64514 port [udp/*] succeeded!<br>
root@freebsd11-03:~ # <b>nmap -sU -p 64514 macpro-lacp;nmap -sU -p 64514 macmini-02-server</b> Starting Nmap 7.70 ( https://nmap.org ) at 2018-08-15 17:51 HKT Nmap scan report for macpro-lacp (10.201.95.9) Host is up (-0.21s latency). rDNS record for 10.201.95.9: macpro-l95.nnnnnnn.studio PORT STATE SERVICE 64514/udp open|filtered unknown MAC Address: xx:xx:xx:xx:xx:xx (Apple) Nmap done: 1 IP address (1 host up) scanned in 0.47 seconds Starting Nmap 7.70 ( https://nmap.org ) at 2018-08-15 17:51 HKT Nmap scan report for macmini-02-server (10.0.99.12) Host is up (-0.21s latency). rDNS record for 10.0.99.12: macmini-02-server.nnnnnnnn.studio PORT STATE SERVICE 64514/udp open|filtered unknown MAC Address: <span>xx:xx:xx:xx:xx:xx</span> (Apple)<br> Nmap done: 1 IP address (1 host up) scanned in 0.46 seconds root@freebsd11-03:~ #<br>
- configure /etc/newsyslog.conf to roll over the logs and delete the older log versions ... (do what you need for ms windows ,... what ever that is.. )
- Now on your ZYXEL USG appliance(s): Configure USG appliance Configure / Log & Report / Log Settings: (in the following example there are two (2x) servers the the router sends the logs to. These are archived for auditing.)

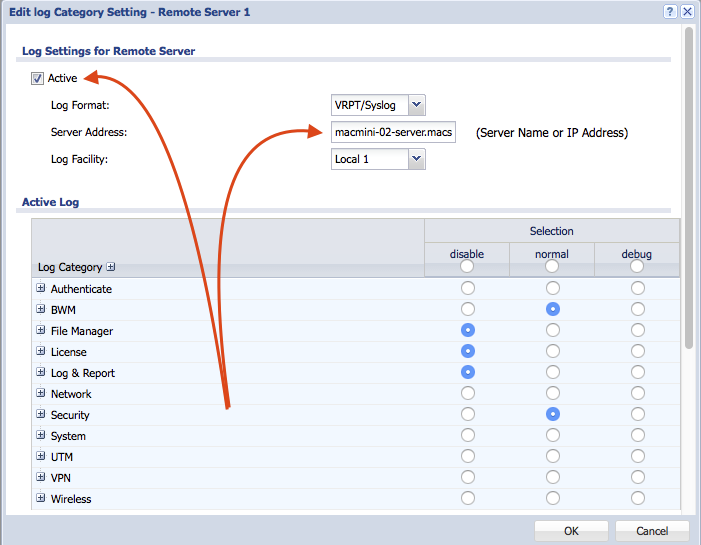
- Optional to use a specific UDP port instead of the default Port 514. You need to access the USG appliance with ssh to use the shell to set the port you want. Zyxel dont provide this in the USG UI.
 . Refer to the latest ZYXEl USG "CLI Reference Guide" .. get from
. Refer to the latest ZYXEl USG "CLI Reference Guide" .. get from - log into the USG appliance (via ssh ...) and issue the show logging status syslog command. In this example only the port 64514 is already set to the one we use.
Router> <b>show logging status syslog remote server: 1 </b> enable: yes log format: vrpt, server address: macmini-02-server.nnnnnnn.studio, <b>server port: 64514</b>, log facility: Local_1 category settings: content-filter : no , forward-web-sites : no , blocked-web-sites : no , warning-web-sites : no , user : normal , myZyXEL.com : no , zysh : no , idp : normal , app-patrol : no , bwm : normal , ike : no , ipsec : normal , secure-policy : normal , sessions-limit : normal , policy-route : normal , built-in-service : normal , system : normal , system-monitoring : no , connectivity-check: all , routing-protocol : all , nat : all , pki : normal , interface : all , interface-statistics: no , account : normal , port-grouping : normal , l2tp-over-ipsec : normal , anti-virus : no , ssl-vpn : no , cnm : normal , traffic-log : no , file-manage : no , adp : normal , anti-spam : no , forward-clear-mails: no , cellular : no , daily-report : no , ipmac-binding : normal , dhcp : all , auth-policy : all , capwap : no , wlan-monitor : no , wlan-rogueap : no , wlan-frame-capture: no , wlan-dcs : no , wlan-band-select : no , wlan-load-balancing: no , rtls : normal , inbound-lb : normal , usb-storage : normal , web-authentication: no , redirect-service : normal , capwap-dataforward: no , authentication-server: normal , wlan-station-info : no , zymesh : no , wlan-auto-healing : no , default : normal , upnp : normal , layer2-isolation : no , sso : normal , zon : no , ap-firmware : no , geoip : no , dfs : no , fqdn-object : no , session-monitor : no , <b>remote server: 2</b> enable: yes log format: vrpt, server address: macpro-l99.nnnnnnnnn.studio, <b>server port: 64514</b>, log facility: Local_1 category settings: content-filter : no , forward-web-sites : no , blocked-web-sites : no , warning-web-sites : no , user : normal , myZyXEL.com : no , zysh : normal , idp : normal , app-patrol : no , bwm : normal , ike : normal , ipsec : normal , secure-policy : all , sessions-limit : all , policy-route : normal , built-in-service : normal , - now set the port you want use use instead of the default port 514 uses by syslog...... In this example 'syslog 2' is configured to use port 64514. The router will start logging to that server on that port:
Router(config)# <b>logging syslog 2 port 64514</b> server '2' port:64514 Router(config)#
- Here's an example with specifics looking for the usual scumbags
 trying to get in on the WAN ports at the active log at
trying to get in on the WAN ports at the active log at<b>tail -f /Volumes/zfs_dataset_usg_routers/usg_60_router_logs/node09-usg60-01.log | grep -i "abnormal TCP flag attack detected"</b> Aug 15 15:09:42 myrouter src="172.97.181.203: 50599" dst="xxx.xxx.xxx.xxx:65446" msg="abnormal TCP flag attack detected, DROP" note="ACCESS BLOCK" user="unknown" devID="aabbccddeeff" cat="Security Policy Control" class="Access Control" ob="0" ob_mac="000000000000" dir="ANY:ANY" protoID=6 proto="others" Aug 15 16:55:27 myrouter src="172.97.181.203: 50658" dst="xxx.xxx.xxx.xxx:56512" msg="abnormal TCP flag attack detected, DROP" note="ACCESS BLOCK" user="unknown" devID="aabbccddeeff" cat="Security Policy Control" class="Access Control" ob="0" ob_mac="000000000000" dir="ANY:ANY" protoID=6 proto="others" Aug 15 18:15:00 myrouter src="172.97.181.203: 50704" dst="xxx.xxx.xxx.xxx:62166" msg="abnormal TCP flag attack detected, DROP" note="ACCESS BLOCK" user="unknown" devID="aabbccddeeff" cat="Security Policy Control" class="Access Control" ob="0" ob_mac="000000000000" dir="ANY:ANY" protoID=6 proto="others"
Epilogue:
you will need to research the specific settings to configure both the syslog rollover/cleanup (typically /etc/newsyslog) and the syslogd or replacement and on the OS platform for the desktop(s) or server(s) you want to use.
This is very easy on FreeBSD and Linux. Use syslog-ng for macOS.Note to Zyxel_Stanley and the team at Zyxel in lovely 台灣
..... would you blokes add a PORT specification in the next firmware update of the USG range in syslog remote server settings?
You did this in the firmware for the GS2210 firmware ...
HTH
Warwick
Hong Kong0 -
-
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 211 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 544 USG FLEX H Series
- 341 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 465 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 87 About Community
- 99 Security Highlight
 Freshman Member
Freshman Member


 Master Member
Master Member

 Zyxel Employee
Zyxel Employee


 Ally Member
Ally Member





