USG Flex - VPN Logins into different subnets possible?
Hi guys,
Before I dig deeper into the manual … Is it generally possible to have different VPN configurations to different subnets/VLANs simultaneously active on an USG Flex?
Presently we've got two configurations active, one SSLVPN profile and another IPSec profile. The corresponding profile is automatically chosen depending on the VPN Client used. But both configurations will forward the VPN traffic always into the same destination subnet. Works fine so far.
Now we've expanded our office to new remotely located rooms (without an own internet connection), which are connected by one fiber line to our USG Flex. And the different new subnets of the remote offices are connected to USG via different VLANs.
This caused that some employees still need a VPN connection to the usual subnet as already configured, while other guys need a VPN connection into the new VLAN subnet.
Accepted Solution
-
Hi Peter,
The commissioning of the VPN routing into two subnets (VLAN) succeeded. But finally it was not only a matter of an updated or additional security policy rule as you stated above.
For SSL VPN we have to additionally add the new VLAN63 subnet into "Selected Address Objects" under CONFIGURATION > VPN > SSL VPN. Now two address objects, "LAN1_Subnet" and "VLAN63_Subnet" are listed in the Network List. Every SSL VPN User is able to ping the hosts of both subnets and have access to.
Much more difficult was the commissioning of the second subnet for IPSec IKEv2 access, since the VPN configuration section at the USG contains an additional "Policy" area, where only ONE target subnet could be chosen from dropdown. Creating an address group, containing both subnets, could not be selected in that dropdown field. Finally we've solved this limitation by changing the subnet mask of the target subnet from 255.255.255.0 to 255.255.0.0 where the entire subnet 192.168.0.0 could be used as target subnet, which includes both 192.168.21.0 (LAN1) and the 192.168.63.0 (VLAN63) subnet. This is working but could cause a security concern since all VPN Users would be able to access all subnets, which means more than both mentioned subnets. On the other hand we are able to steer and restrict the access via security policies, what we've done.
0
All Replies
-
So you want to some users by VPN to have access to one subnet but not the other?
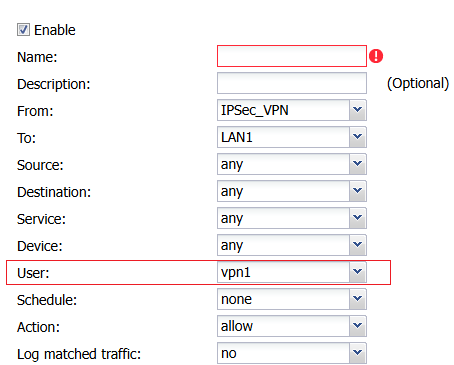
You can do control policy for a given user to access a given subnet
note by default you may be allowing access to all subnets on the FLEX
0 -
Thanks Peter
The restriction is peresently not our problem. I have only a lack of understanding, how a remote user should say to its VPN client to login into one or the other subnet, since he is entering IP address and login credentials only.
Do I have to arrange it in user profile at USG?
0 -
When I user logs in by VPN there login name is mapped to what IP they get so you can do rules like this
0 -
Ok Peter, then you've given me the right direction where I have to search for. Long time ago where I've set up the VPN config in our USG. Thanks again.
0 -
Hi Peter,
The commissioning of the VPN routing into two subnets (VLAN) succeeded. But finally it was not only a matter of an updated or additional security policy rule as you stated above.
For SSL VPN we have to additionally add the new VLAN63 subnet into "Selected Address Objects" under CONFIGURATION > VPN > SSL VPN. Now two address objects, "LAN1_Subnet" and "VLAN63_Subnet" are listed in the Network List. Every SSL VPN User is able to ping the hosts of both subnets and have access to.
Much more difficult was the commissioning of the second subnet for IPSec IKEv2 access, since the VPN configuration section at the USG contains an additional "Policy" area, where only ONE target subnet could be chosen from dropdown. Creating an address group, containing both subnets, could not be selected in that dropdown field. Finally we've solved this limitation by changing the subnet mask of the target subnet from 255.255.255.0 to 255.255.0.0 where the entire subnet 192.168.0.0 could be used as target subnet, which includes both 192.168.21.0 (LAN1) and the 192.168.63.0 (VLAN63) subnet. This is working but could cause a security concern since all VPN Users would be able to access all subnets, which means more than both mentioned subnets. On the other hand we are able to steer and restrict the access via security policies, what we've done.
0 -
Or use 0.0.0.0
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 213 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 551 USG FLEX H Series
- 341 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 471 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Master Member
Master Member



 Guru Member
Guru Member