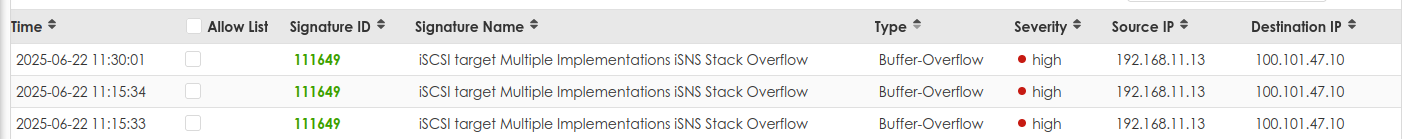
IPS iSCSI warnings.
 Ally Member
Ally Member

What is this warning telling me?
I am familiar with both the source and the destination machines.
Is this reporting that the source "192.168.11.13" is doing something to the destination that is harmful or unwanted?
I am very familiar with the source, and I would like to assume it is clean an safe.
What is IPS detecting exactly?
the above has over 900 warnings stacked. So, I don't want to dismiss it, I'd like to understand it. When i google the iSCSI / iSNS it doesn't help me understand my scenario.
Best Answers
-
Update:
This is confirmed as a false positive, and it has been fixed on IPS signature V4.0.0.20250812.0.
Zyxel Melen0 -
Thank you.
0
All Replies
-
Hi @jef ,
To look up information about any IPS Signature ID, please refer to this link, enter the Signature ID, and click Search.
Zyxel_Judy
0 -
I had already done that, if you click in application, on the signature it opens the signature explaination.
But, it doesn't tell you what you need to know as an Admin, it explains why it is a signature IPS issue.
I scanned the source IP box and it returned clean, multiple times.
So I am confused at what the IPS alarm is all about and what triggered it.What triggered it. If the source is known, and the source doesn't have any malware.
Why is the error being thrown.0 -
This tells me to? Yes the source IP server is Linux and the Destination is AWS linux.
Why does IPS think the source is attacking the destination??0 -
Hi @jef ,
I scanned the source IP box and it returned clean, multiple times.
Could you please share the details about the tool and steps you used to scan the source IP (192.168.11.13) and confirm that it returned clean results?
Zyxel_Judy
0 -
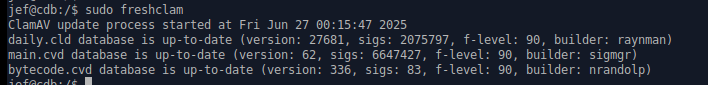
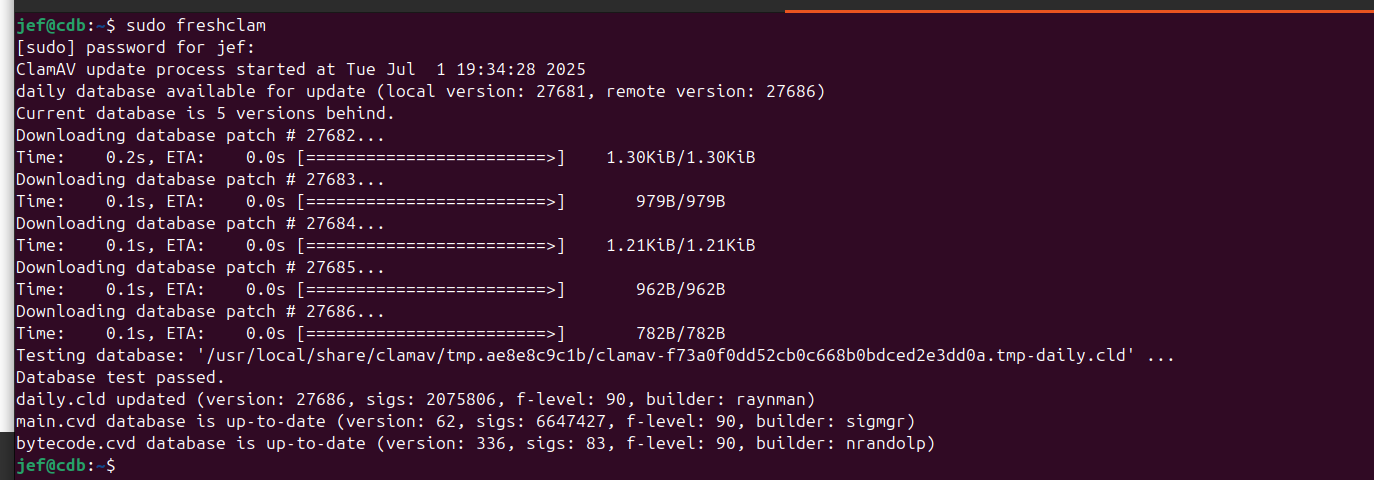
I did a "freshclam" to update the Signatures, then I ran the scan.
I didn't take a "before" picture of the freshclam, because I didn't think to until after the scan finished.
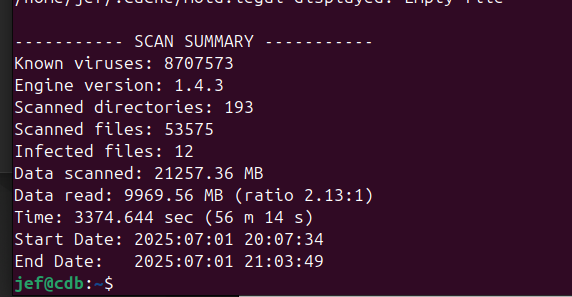
But you get the Idea.Step 1. Fresh Signature files.
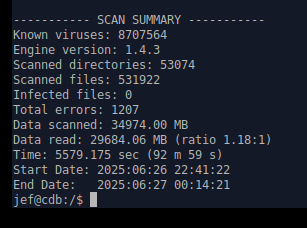
Step 2. Let it run from root for an hour and a half. Done… No Infected files.
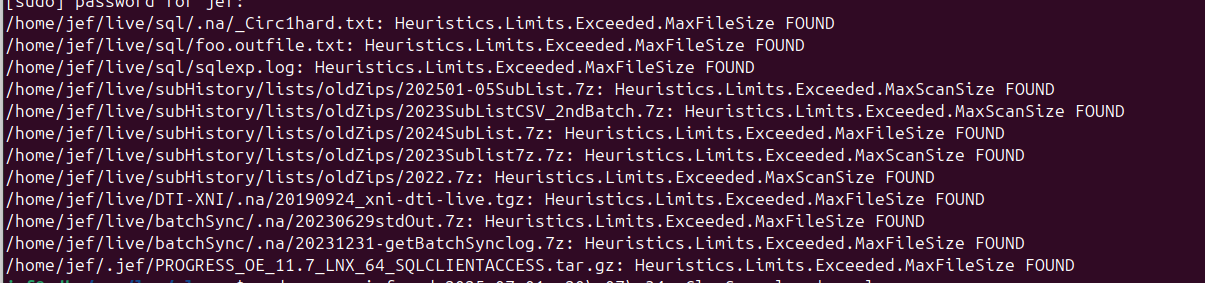
Errors 1207, logs show are empty files and symbolic links or active system files under permission lock.0 -
Hi @jef
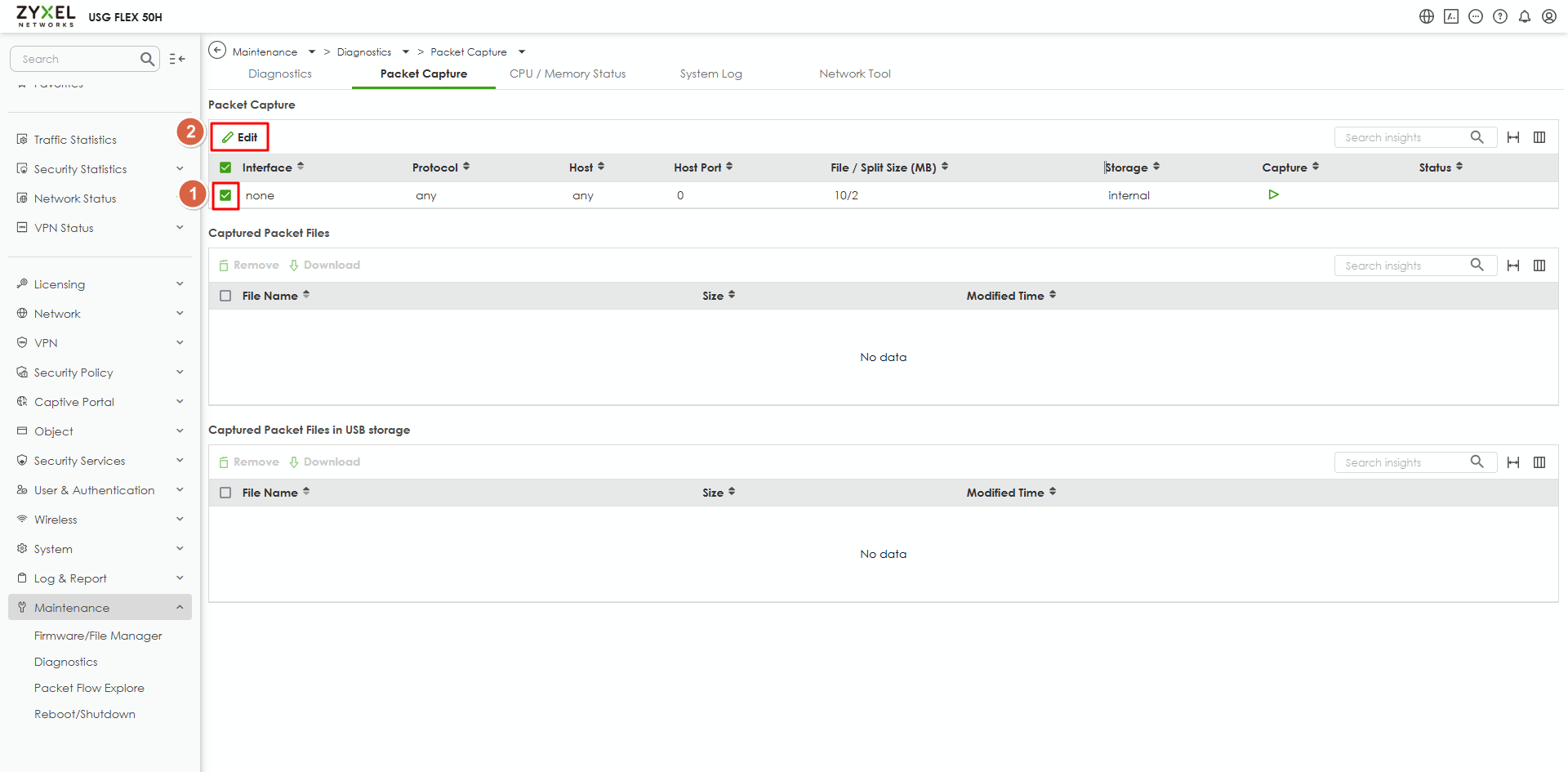
Thanks for the information. We did a lab to use "freshclam" but our USG FLEX H didn't detect the abnormal activity. To investigate this further, could you help to collect below info?
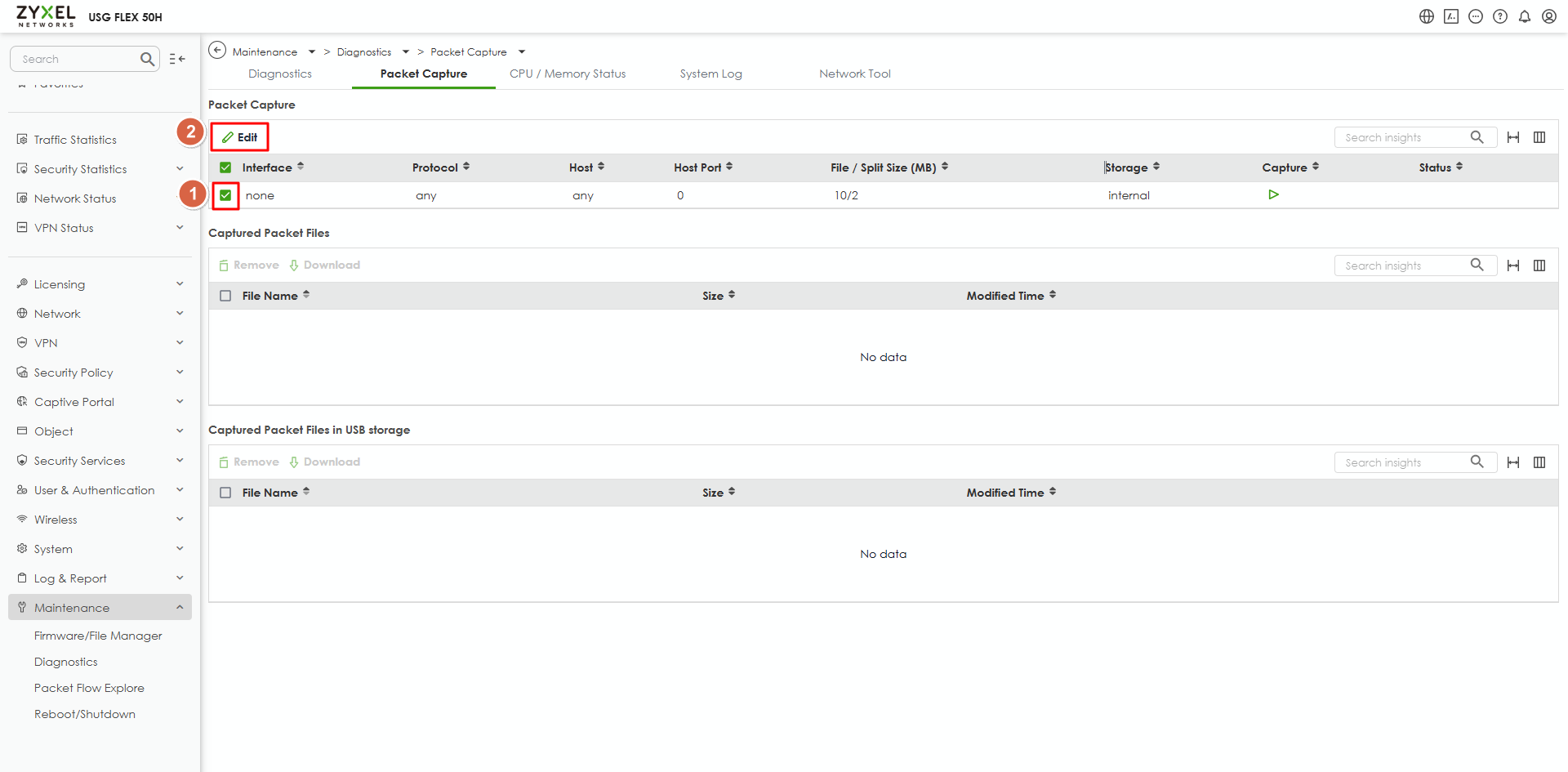
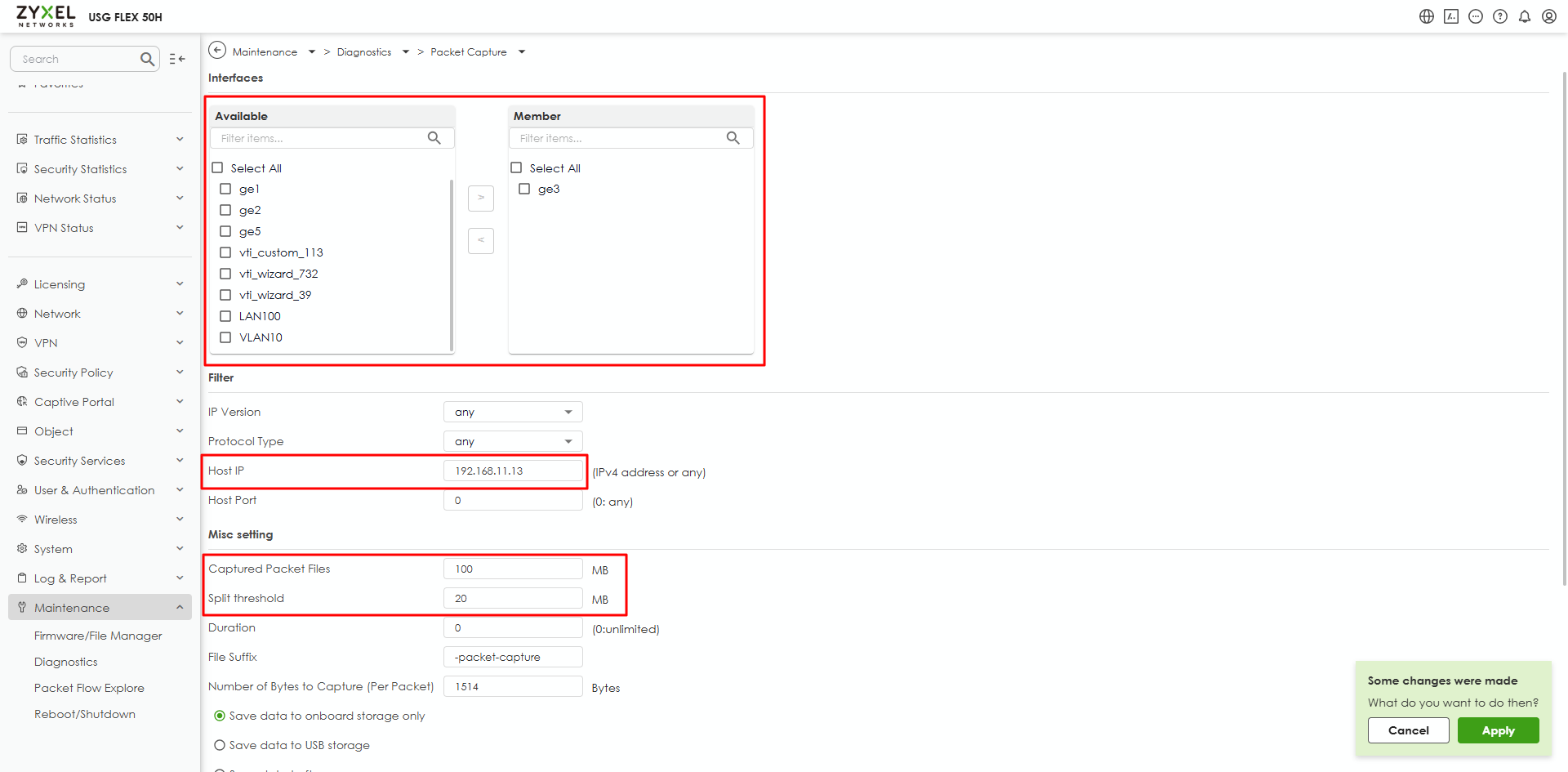
- Please help to capture this server's packet from the LAN interface. Please
- Select the packet capture item to edit it.
- Change the capture condition and apply.
- Click the capture button to start capturing.
- Update the linux server's clamav database.
- Capture/screenshot the event log again once the device display the block log. In the mean time, stop capture packet.
- Provide the screenshot and the packet to us. You may send it to me via private message.
Thanks!
Zyxel Melen0 - Please help to capture this server's packet from the LAN interface. Please
-
I will, but the "Security Services" "IPS Trial" has ended.
I assume without a valid license it is not scanning signatures anymore.
I will send you the pkt capture and screenshot when the scan completes.the 12 "found" are not "infected" per se, they flag because they exceed the files size.
0 -
-
How do I know which machine, "Source" or "destination, to focus on from this information?
From thisIf this is Packet Inspection, could we get more information than the above.
What exactly raised this error. which direction, anything more would be useful.
The "Source" isn't running iSCSI. Nor is it public facing.
The "Destination" is ipsec VPN, also not public facing.
Not sure if it is running iSCSI it is privately hosted by a vendor.
The question I would most like answered is: Is this an Attack, or a Vulnerability warning?0 -
Hi @jef,
The question I would most like answered is: Is this an Attack, or a Vulnerability warning?
After checking, we assume this could be a false detection and are checking with our partner. In the meantime, we want to check the version of your ClamAV. Could you help to use this command to collect the version?
#clamscan -V
Here is our lab's version:
└──╼ #clamscan -V
ClamAV 1.0.7/27694/Wed Jul 9 16:42:34 2025Thanks!
Zyxel Melen0
Categories
- All Categories
- 441 Beta Program
- 2.9K Nebula
- 208 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 530 USG FLEX H Series
- 332 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 51 Wireless Ideas
- 6.9K Consumer Product
- 294 Service & License
- 461 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 86 About Community
- 99 Security Highlight

 Zyxel Employee
Zyxel Employee