Full VPN tunnel from FlexH 1.32 FW to Nebula Org firewall
All Replies
-
Its black because you enabled Connectivity Check try with it off when its black it mean ping failed
is the VPN connected?
0 -
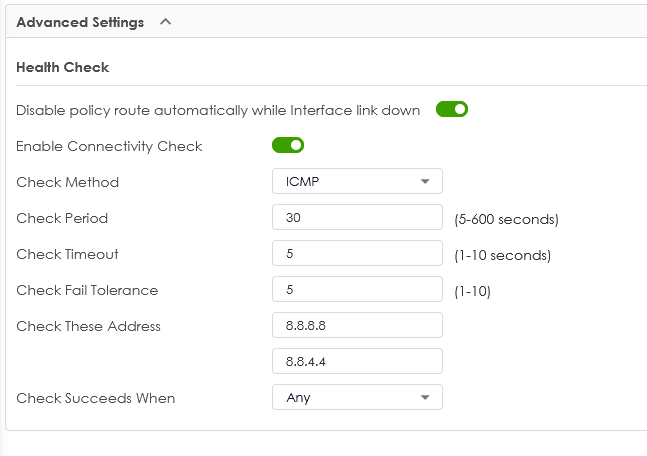
Yes of course, that icon is black because I wanted to use the option to deactivate the routing rule (LAN via VTI interface) so if the VPN goes down the firewall allows at least web navigation:
Anyway I deactivated that advanced option, now the status is green:
but I prefer to see if the rule is working properly or not.
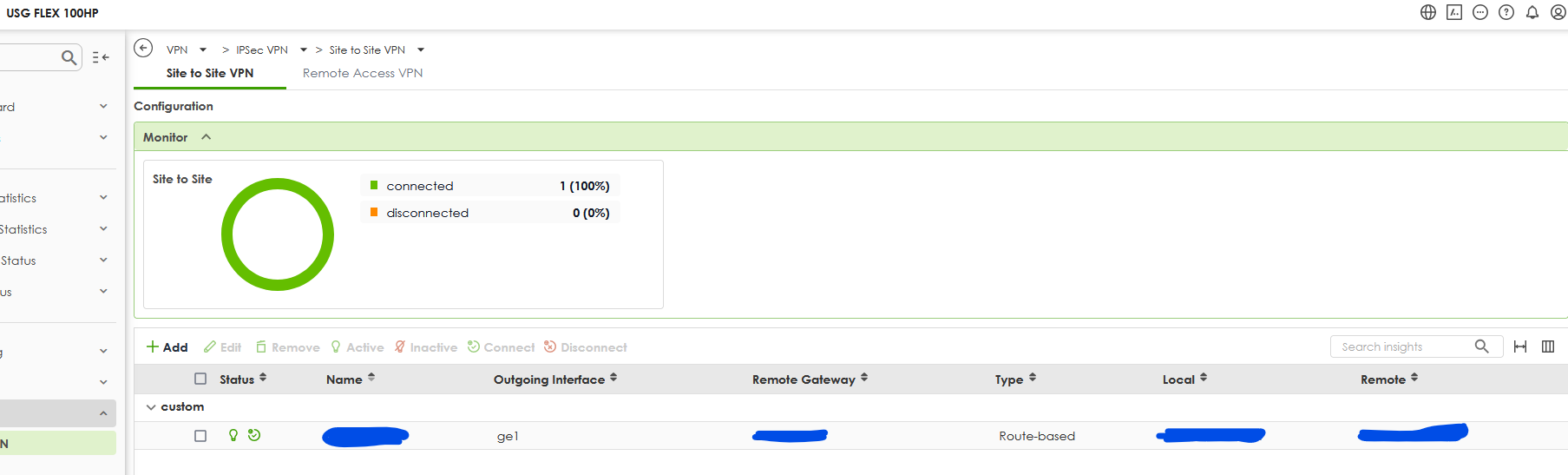
The VPN is connected:
what am I missing to have the connectivity check working properly?
0 -
run at your end
ping -t 1.1.1.1
check logs, maybe make firewall rules, packet capture the tunnel
have you setup the other end right with static route?
0 -
Hello @Zyxel_Melen
I followed your infos and also @PeterUK ideas, but VTI seems to be offline, I went onsite (of Flex100H) but I do not find what I'm missing.
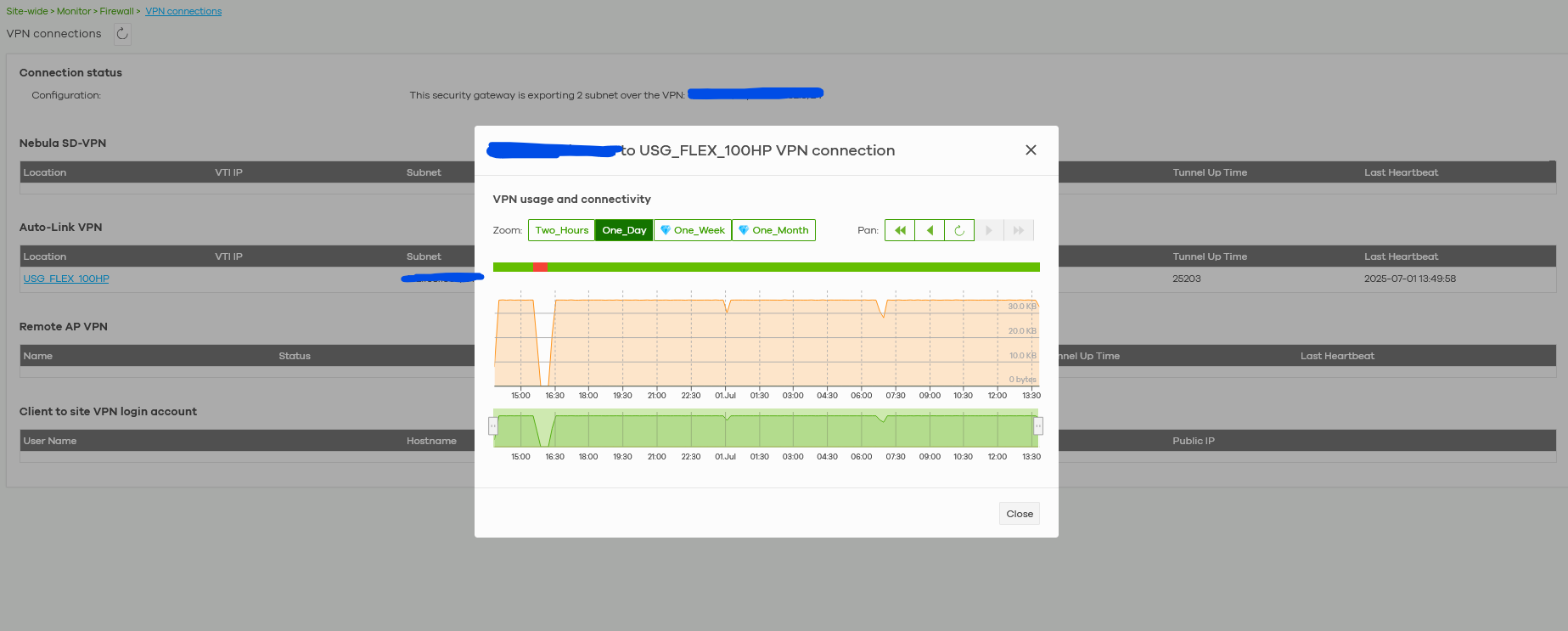
On Nebula Site (destination ORG) I see the VPN connected:
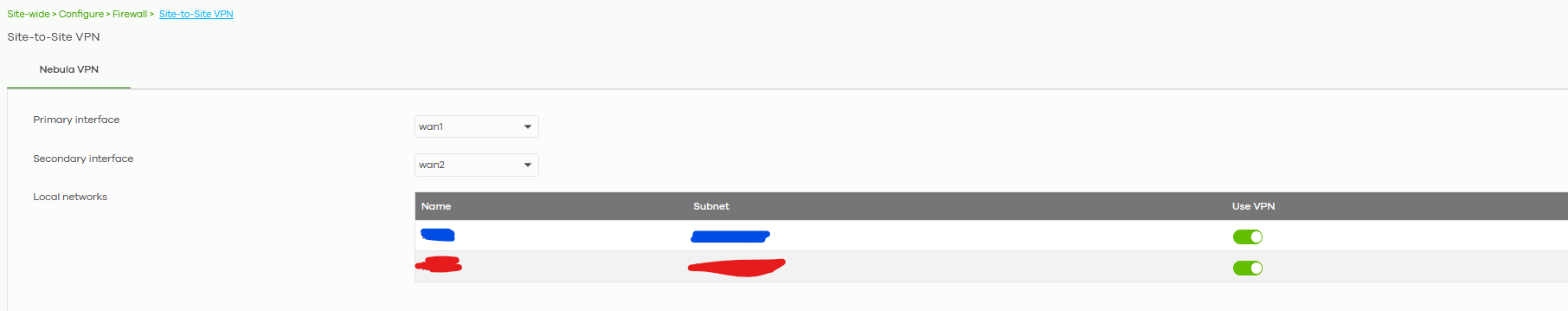
I have both LANs enabled for VPN too (local LAN in blu, specific LAN in red for remote VPN):
I checked also that in the "Implicit allow rules" red LAN was allowed to go online.
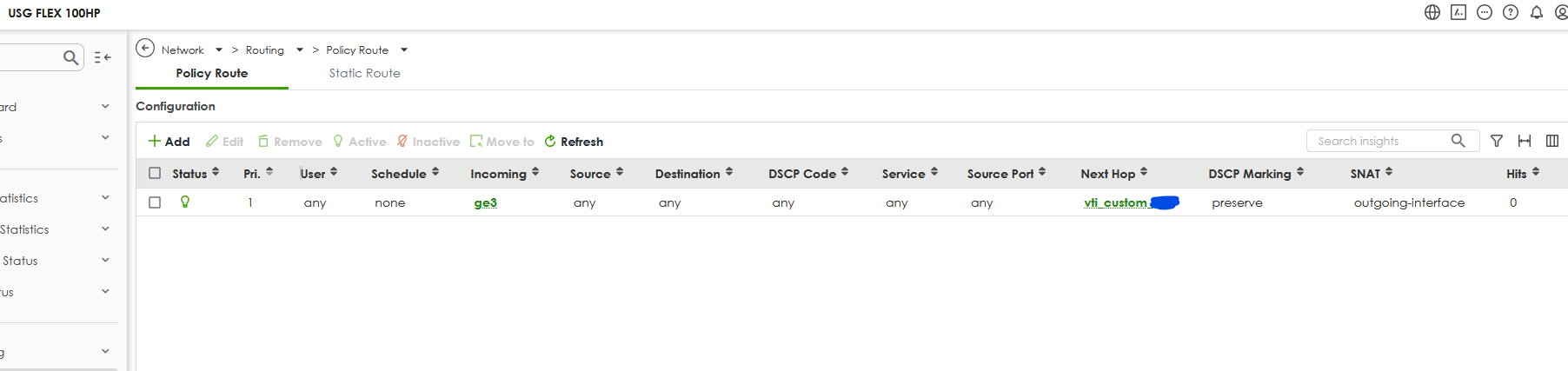
So the problem seems to be on the origin, I did these steps:
- created the route based VPN (it is connected as you can see)
- created the routing policy for ge3 via VTI
In any case the VTI tunnel goes offline if I set the connectivity check so I have not full tunnel VPN working.
0 -
why have you covered up local and remote when both would be 0.0.0.0/0 by default?
0 -
Mine are not 0.0.0.0/24
The VPN panel asked me which local LAN subnet should connect remotely, so I put on "local" and "remote" values the specific LANs.
For example if local LAN is 192.168.200.0/24 and remote is 192.168.201.0/24 you can find those values there.
Should be both 0.0.0.0/24 ?
0 -
yes that how I got it working with 0.0.0.0/0
0 -
Hi @GiuseppeR
I didn't encounter this in my lab.
Here is my configuration:
If you still encounter the issue after comparing PeterUK's suggestion and my configuration, please provide the organization access and login credential so I can access the device and help to check.
Zyxel Melen0 -
Hello @PeterUK and @Zyxel_Melen
I made a mistake configuring VTI addresses.
I used the same value on Nebula page (Site-to-Site VPN) and on FlexH on prem.
Now the tunnel seems stable, but I'll update you tomorrow morning.
Right now it seems that the VPN goes to the first available subnet (like 192.168.1.1): how can I tell the VPN to go to another remote subnet?
How can I tell the FlexH on prem to connect to remote subnet 192.168.201.0/24 so I can make Security policies on Nebula to manage the VPN resources?
0 -
The VTI addresses just need to be both in the same subnet and not in use by any other interface LAN.
In my setup I take the incoming LAN by routing rule and SNAT none now if that LAN subnet is not used by the other end then its fine the other end then does routing rule from VTI to the WAN then you need a static route to send your LAN subnet traffic down the VTI.
If you do incoming LAN by routing rule and SNAT outgoing interface now that LAN subnet is SNAT by the VTI IP to the other end.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 601 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 480 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Guru Member
Guru Member



 Master Member
Master Member



 Zyxel Employee
Zyxel Employee





