Static IP assignation for SSL VPN clients
 Freshman Member
Freshman Member
Hello.
How to assign specific static IP adrress for SSL VPN clients, for example based on username/password? I have Split Tunnel configuration with two local networks and one client network pool. I would like to assign static IP for every VPN client so it will help me to analyze Security Reports and identify problematic clients. When IP is constantly changing it is very hard to track such client.
All Replies
-
There is no way to do this currently from the UI that I can see.
You would likely have to do this at the client side
0 -
Hi @KNowak
SSL VPN doesn't support static IP address for specific client/user. Would you like to share your use case for us to evaluate it?
Zyxel Melen0 -
Sure.
Business decided that if remote user is connected to company network, then he is technically 'at work', even when he is using his own PC. Therefore, I decided to filter and log remote users DNS traffic. In SSL VPN configuration, I've pointed Zyxel as only DNS.
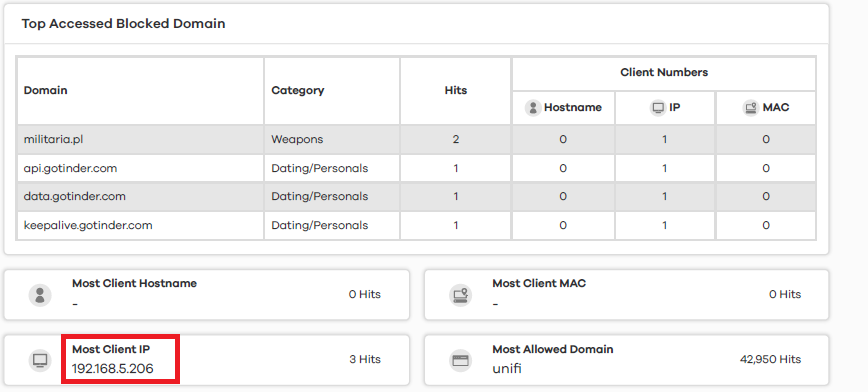
When 'Open VPN Connect' client is connoted to company network then my Zyxel becomes primary DNS for this PC. And this is working fine. Great, now I know which remote PC maybe infected or just risky. Here is example screen from weekly Summary Report:
Now I want to identify that user quickly to react for threat... How can I do this?
How to match vpn user with session time, with assigned IP and with security logs? If I will be able to create individual reservation for each user then this task would be simple.
I'm facing simmilar difficulty when in I have two internal DNS servers which are both forwarding queries to Zyxel. In DNS threat view I see my DNS servers as origin of blocked threat and to identify specific PC on local network I need to use packet trace.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Guru Member
Guru Member



 Zyxel Employee
Zyxel Employee