Flex H - Camtive portal
 Freshman Member
Freshman Member
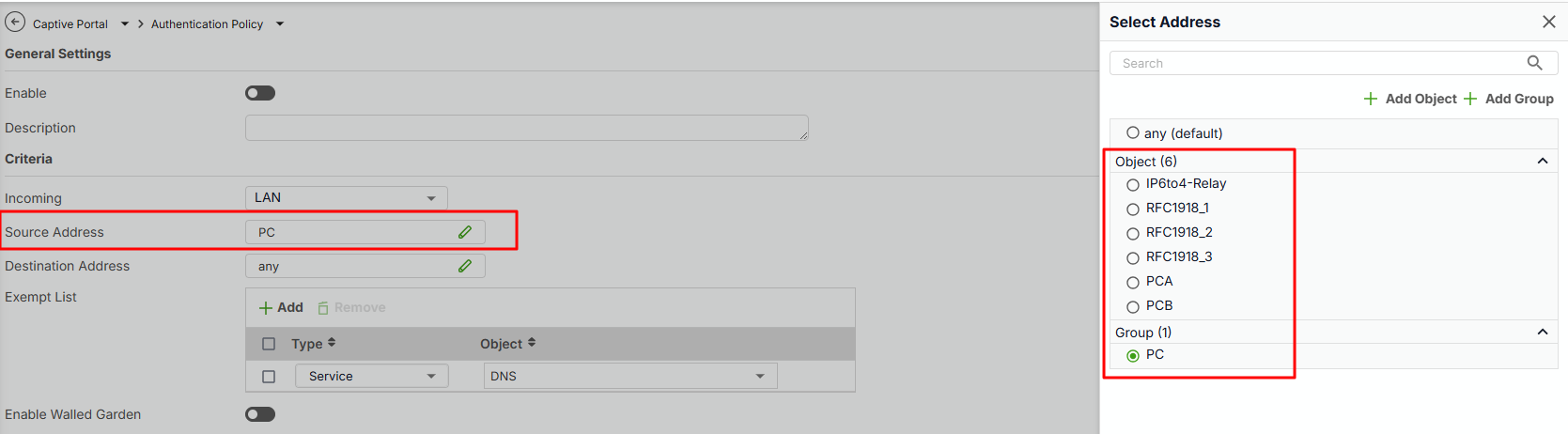
We verified a configuration that the customer requested, which was to define only certain PCs on the LAN that would be restricted via captive portal. We contacted Zyxel support, and they confirmed that, as with the ATP series, it's not possible to specify an IP range excluded from the captive portal feature managed on the same network. Only individual IPs, interfaces, or services can currently be excluded. This limitation is very frustrating and limits the functionality often used on the ATP series.
All Replies
-
Could you describe more details with us? The specific LAN has lots of devices, like printer, IP phone, IoT devices, PCs, and you want only PCs need to authenitcation by captive portal?
Zyxel Melen0 -
The next firmware, V1.36, will support selecting an address or address group in the source address for specific interface.
Does this match your requirement?
Zyxel Melen0 -
Hello!
How can I select Incoming "WAN" as source for the captive portal?
Best regards,
MJR
0 -
Hi @mjr
Captive portal is a gatekeeper positioned between clients and the internet. You cannot freely access the internet until you complete the actions it requires. If you want to access LAN from WAN, what you should configure is the security policy/firewall rule. Or, connect the remote access VPN.
Zyxel Melen0 -
with the Usg flex (pre H) it was possible to configure a security policy/firewall rule/NAT (access LAN from WAN), which was bound to a specific user/user group. the user had to logon to the firewall (via webinterface), authenticate and afterwards the connection was allowed.
1 -
@Zyxel_Melen I'd also really like this feature to be added to the H Series, as @mjr says, it was available on the legacy USG Flex series.
Our issue is that some of our customers would like 2FA (via google authenticator or otherwise) for VPN clients, we've even seen some cyber insurance companies requesting 2FA as a requirement for remote VPN access. Currently on the USG Flex H series there is no way to redirect VPN clients to a captive portal before granting them access to the network.
I think this would be a fantastic feature to add in, and would definitely increase the security of the H series devices.
0 -
this issue was answered here:
1 -
To clarify, I'm aware that the 2FA feature comes with the licence-based (paid) SecuExtender client, and upon connection the user is then redirected to the firewall for 2FA, but I feel as though this should be available with the native Windows or Mac VPN clients. If the IKE VPN could be selected as an incoming interface for captive portal, I feel as though this would solve the problem.
0 -
The native VPN clients doesn't support auto-redirect/auto-popout 2FA authentication page. And the captive portal is to recognize the user when accessing specific zone/interface/subnet, not for authentication part of remote access VPN connecting. These are different scenarios.
Zyxel Melen0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 589 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Zyxel Employee
Zyxel Employee