USG 110 - SSL VPN - policy route
Hello together,
Sorry - I checked so many settings and it is still not working, maybe someone knows what to do.
I want to set up an SSL VPN tunnel. We are already using two IPSec tunnels and L2TP tunnels.
Main problem if the SSL VPN tunnel is - not traffic is coming back!
I checked the default SSL VPN policies, changed them a lot of times - but nothing it working.
Internal router IP: 10.100.100.182/16 (lan1)
Internet net: 10.100.0.0/16
SSL VPN range: 192.168.80.1/24
SSL VPN Gateway: 192.168.80.1
I checked the conntion with Wireshark.
As example, if I try to get access to server 10.100.1.45, port 80 - The packet capture tool/Whireshark is always trying to send the packages (TCP Retransmission).
Source: 192.168.80.1, Destination 10.100.1.45 - TCP Retransmission
Source: 10.100.1.45, Destination 192.168.80.1 - TCP Retransmission
Added policies:
From SSL_VPN to any, Source any, Dest. any, allow
From SSL_VPN to ZyWall, Source any, Dest. any, allow
Added policy routes:
Incoming any, Source SSL VPN Range, Destination any, Next-Hop auto
Incoming any, Source any, Destination SSL VPN Range, Next-Hop auto
I would be very thanksfull if someone has further ideas.
Thanks a lot and best regards
David
All Replies
-
Hi @David582
Welcome to Zyxel Community. ?
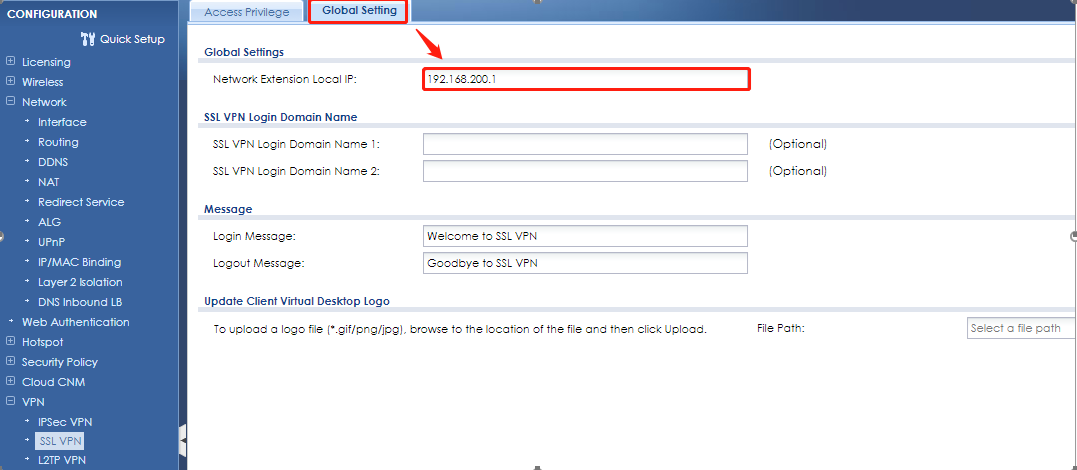
The SSL VPN Gateway IP address should not within SSL VPN range.
You can change Network Extension Local IP to default IP 192.168.200.1 and try it again.
CONFIGURATION > VPN > SSL VPN > Global Setting
0 -
Hello @Zyxel_Cooldia
Thanks a lot for your reply!
I changed the GW - but still not change.
Tunnel is connecting and I can ping/access the router (local ip 10.100.100.182), but no other server in the local net.
By the way.. I am using the latest SecuExtender, version 4.03 and
the latest USG 110 firmware, V4.33(AAPH.0).
Again, thanks - best regards
David
Edit: Picture of log firewall attached.
0 -
Hi @David582
There is no need to add policy route for SSL VPN connection in USG.
Please delete policy route related to SSL VPN(or subnet 192.168.80.0/24), and try it again.
0 -
Oha - I was sure that there is only a "small" problem - but I couldn't find it.
Thanks for your reply. I deleted all policy route related to SSL VPN. First there was no change - but then I saw that "Use IPv4 Policy Route to Override Direct Route" was activated. I don't know why and I don't know why I did not see that till now. After deactivating the SSL tunnel was able to get access to the local net (10.100.0.0).
If it is ok for - another small question.
It would be nice if the SSL VPN tunnel can access some server through a IPSec tunnel (172.30.107.0). For this I need a policy route, correct?! Tried it with:
SSL VPN --> USG 110 --> IPSec
Incoming SSL VPN, Source any, Destination IPSec range, Next-Hop IPSec Tunnel.
Thanks and best regards, have a nice day
David
0 -
Hi @David582
It’s doable. The following configuration guide for your reference.
How do I allow SecuExtender clients to access servers in the remote site/company through VPN tunnel?
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 602 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 480 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Freshman Member
Freshman Member

 Zyxel Employee
Zyxel Employee