How to Configure 802.1x to Secure the Wireless Environment with an External AD Server?
 Zyxel Employee
Zyxel Employee


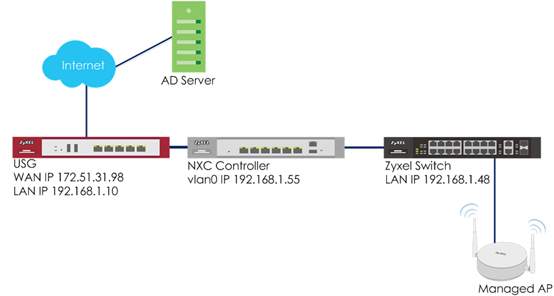
The example instructs how to set up the NXC controller with an external AD server. When the station wants to connect with the AP, you can use an AAA server to provide access control to your network. In this example, the AD server is external but not embedded in the NXC controller, and the controller is already set to use the AD server for authentication.
Configure AD Server Setting
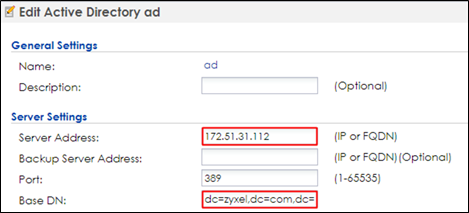
1 Go to CONFIGURATION > Object > AAA Server > Active Directory, click #1 ad, and then click Edit to configure AD server’s information.
2 In Server Settings, enter Server Address. Here use 172.51.31.112 as the example. Go to AD server to check Base DN. Here is an example for checking the Base DN on Windows server, and it can be copied from clicking right on the domain name > properties > Attribute Editor> distinguished Name > View.
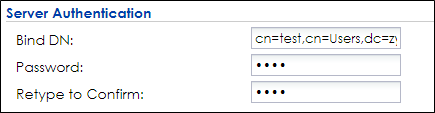
3 In Server Authentication, enter Bind DN and Password. You can check Bind DN in the AD server. In the AD server, clicking right on the Administrator > properties > Attribute Editor > distinguished Name > View. The Password is Administrator’s password in the AD server.
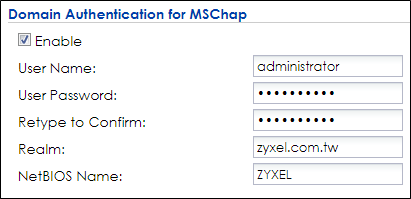
4 In Doman Authentication for MSChap, check Enable and enter the User Name, User Password, Realm, and NetBIOS Name. The Realm is the domain name of the AD server.
5 After finishing the configuration, enter administrator as the Username and click Test in Configuration Validation.
6 Go to CONFIGURATION > Object > Auth. Method. Select to the default method, and click Edit. Select the AD server you create. Click OK.
7 Go to CONFIGURATION > System > Date/Time and check Current Time and Date. The date and time must be the same as the date and time of the AD server. If it’s different, you can select the correct time zone in Time Zone Setting.
8 Go to CONFIGURATION > System > Host Name. Set the domain name as you set on the AD server.
9 Go to CONFIGURATION > System > DNS for setting domain zone information. In Domain Zone Forwarder, click Add to add a new domain zone. Enter the Domain Zone and Public DNS Server which is the AD server’s IP.
Configure AP Profile
1 Configure AP profile to use 802.1x authentication that the user needs to log in with their ID and Password when connecting to AP’s SSID. Go to CONFIGURATION > Object > AP Profile > SSID > Security List, click Add to add security for 802.1x.
In General Settings, enter the Profile Name and change Security Mode to wpa2.
In Radius Settings, select to Internal and it means the authentication needs NXC to communicate with an external AD server.
In Authentication Settings, select to 802.1x and Auth. Method is default. Click OK.
2 Go to CONFIGURATION > Object > AP Profile > SSID > SSID List, click add to add a SSID for the connection with 802.1x security. Key in the Profile Name and SSID, and change Security Profile to ADtest which you configured in step1. Click OK to save.
3 Go to CONFIGURATION > Wireless > AP Management > AP Group, select the default AP profile and edit. Select ADtest in the SSID Profile. Click OK to apply the SSID to AP.
Comments
-
Test the Result
1 Before connecting the SSID, the computer needs to do some settings to make a connection successfully. Here is an example for Windows 7.
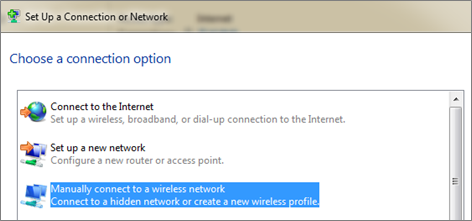
Open Network and Sharing Center in the computer, click Set up a new connection or network to build up a new network.
2 Select Manually connect to a wireless network. Click Next.
3 Key in the SSID in Network name, set the Security type to WAP2-Enterprise, and the Encryption type is AES. Click Next.
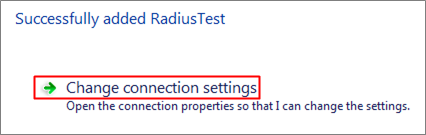
4 Select Change connection settings.
5 Change Security type to WPA2-Enterprise, and Encryption type is AES. Click Settings.
6 Uncheck Validate server certificate and click Configure.
7 Uncheck the selection of the pop-up window. Click OK.
8 Go back to the security setting page and click Advanced settings.
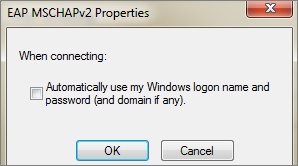
9 Check Specify authentication mode. Click OK to save.
10 Select and connect to the pre-defined SSID "ADTest". Enter user credentials for authentication. After entering the correct ID and password, the wireless connection is set up successfully.
What Could Go Wrong
1 There are two kinds of Radius Server Types in security profile setting. Internal means the authentication is doing between the NXC controller and the AD server.
2 When the Radius Server Types change to External, it means the authentication is doing between the Managed AP and the Radius server. However, the AD server does not support EAP protocol, so it’s necessary to install IAS or NPS on the AD server for EAP protocol.
3 Check the AD server whether receive the information from NXC5500 and add the NXC5500 in the computers list automatically.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight