How to Configure 802.1x with Dynamic VLAN by Using External AAA server?
 Zyxel Employee
Zyxel Employee


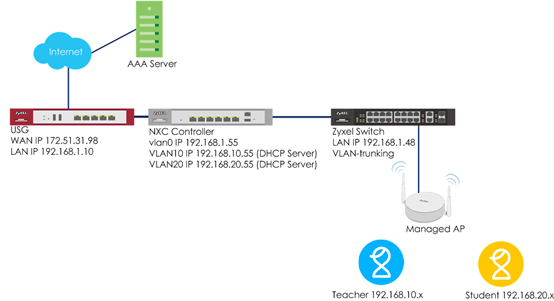
When the station wants to connect with the AP, you can use an AAA server to provide access control to your network. In this example, assuming there are two stations in different groups and they can connect to the same SSID for accessing the Internet, but get IPs in different subnets because of the dynamic VLAN settings.
There are two ways for dynamic VLAN settings. One is to use the radius server attribute, and the other is to use the NXC controller external user group with radius or AD server. The example instructs how to set up dynamic VLAN by using external AAA servers with these two ways.
Configure Interface
1 Go to CONFIGURATION > Network > Interface > VLAN, click vlan0 and Edit it.
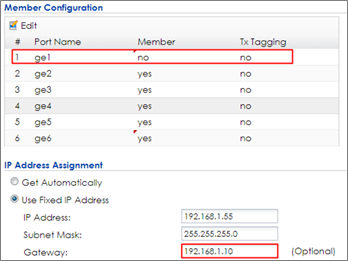
2 Set ge1 (P1) to not be vlan0’s member by selecting no in Member Configuration. Set the gateway IP in IP Address Assignment. Click OK to save. Connect ge1 (P1) to the USG’s LAN port.
3 Connect Switch to NXC ge2 (P2), and APs all connect to the switch.
4 In the NXC, go to CONFIGURATION > Network > Interface > VLAN. Click Add to create a new VLAN configuration.
5 In General Settings, check Enable.
In Interface Properties, key in Interface Name: vlan10; VID: 10
In Member Configuration, set ge2 to be Member and Tx Tagging.
In IP Address Assignment, Use Fixed IP Address and key in IP Address, Subnet Mask, and Gateway.
In DHCP Setting, select DHCP server and key in IP Pool Start Address and Pool Size. First DNS server change to Customer Defined 8.8.8.8. The users in VLAN 10 get an IP from this DHCP server. Click OK.
6 Click Add to create vlan20 in CONFIGURATION > Network > Interface > VLAN.
7 In General Settings, check Enable.
In Interface Properties, key in Interface Name: vlan20; VID: 20
In Member Configuration, set ge2 to be Member and Tx Tagging.
In IP Address Assignment, Use Fixed IP Address and key in IP Address, Subnet Mask, and Gateway.
In DHCP Setting, select DHCP server and key in IP Pool Start Address and Pool Size. First DNS server change to Customer Defined 8.8.8.8. The users in VLAN 20 get an IP from this DHCP server. Click OK.
8 Go to CONFIGURATION > Network > Interface > Ethernet, select ge1 and Edit it. Change the Interface Type to external and Get Automatically in IP Address Assignment.
9 Go to CONFIGURATION > Network >Routing > Policy Route and click Add to add a policy route. Select Interface ge1 in Next-Hop, and outgoing-interface in Address Translation after clicking Show Advanced Settings.
Configure AP Profile
1 Configure the AP profile to use 802.1x authentication that the user needs to log in with their ID and Password when connecting to the AP’s SSID. Go to CONFIGURATION > Object > AP Profile > SSID > Security List, select the default AP profile and edit.
In General Settings, enter the Profile Name and change Security Mode to wpa2.
In Radius Settings, change to Internal and it means the authentication needs NXC to communicate with external radius server.
In Authentication Settings, change to 802.1x and Auth. Method is default. Click OK.
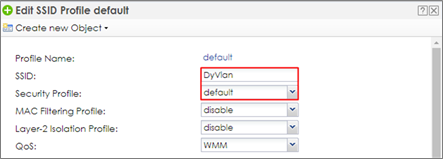
2 Go to CONFIGURATION > Object > AP Profile > SSID > SSID List, and select the default AP profile and edit. Key in the Profile Name and SSID, and change Security Profile to default which is created in step1. Click OK to save.
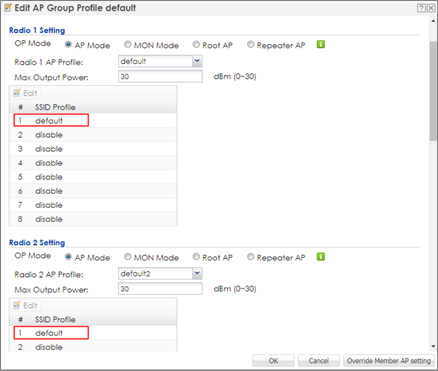
3 Go to CONFIGURATION > Wireless > AP Management > AP Group, select the default AP profile and edit. Select default in the SSID Profile #1 in both radio1 and radio2. Click OK to apply the settings.
Comments
-
Configure AAA Server Setting
Dynamic VLAN by radius server attribute
A. Settings on Radius Server
Here is an example by using Windows 2008 server with NPS and AD server.
1 Add the user to a group in AD server.
2 Go to Member Of to check if the member, Teacher, is added successfully in the group.
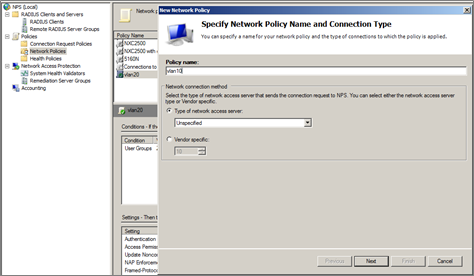
3 Add a new Network Policy of NPS server for a group and then click ‘Next’.
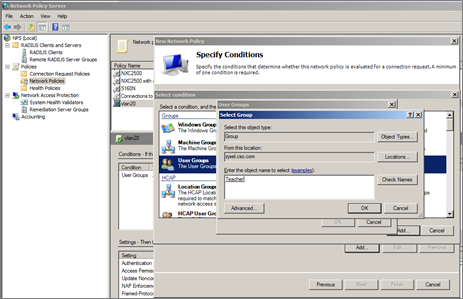
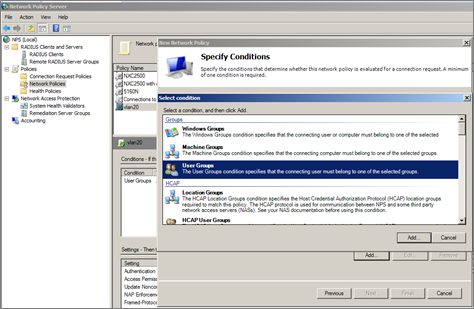
4 Add ‘User Group’ condition.
5 Select the group which is set in AD server.
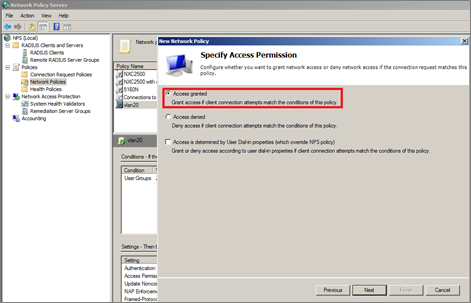
6 Set the access permission and click ‘Next’.
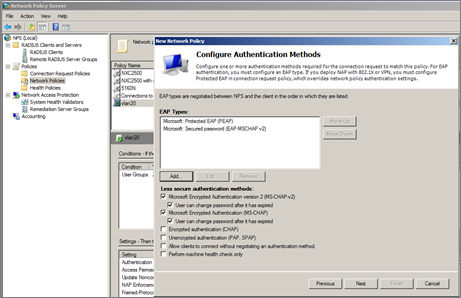
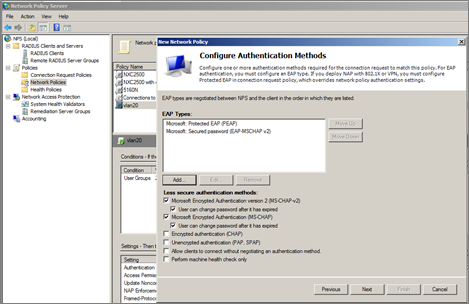
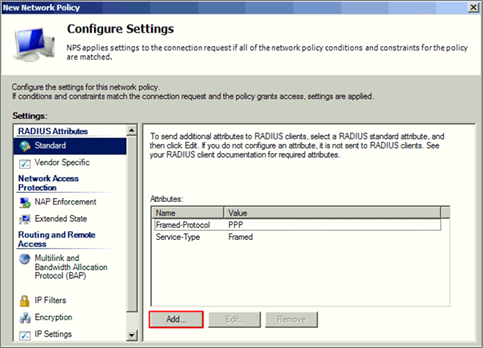
7 Configuration Authentication Methods and click ‘Next’.
8 There are three attribute needed to add, Tunnel-Medium-Type, Tunnel-Pvt-Group-ID, Tunnel Type. Set the attribute configuration and click ‘Next’.
9 Do the same steps to create the other group for other users.
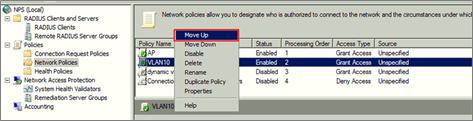
10 Move up the policies to top in Network Policies of NPS to make sure it’s the first one to hit when the traffic is come.
B. Settings on NXC Controller
1 Go to CONFIGURATION > Object > AAA Server > RADIUS, click #1 radius, and then click Edit. Set the Server Address, and Authentication Port is 1812. Enter the Key for Radius server and click OK.
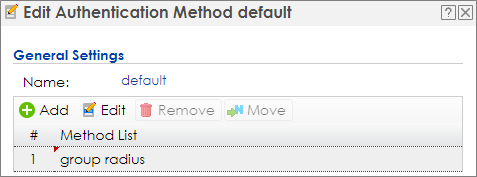
2 Go to CONFIGURATION > Object > Auth. Method, click #1 default, and then click Edit. Change the Method to group radius. Click OK to save.
0 -
Topic: Dynamic VLAN by radius attribute
Dynamic VLAN by External User Group
When users use dynamic VLAN by external user group, the radius and AD server are supported. Here are two examples for settings these two servers and NXC controller.
A. Settings on Radius/AD Server
1 Add the user to a group in AD server.
2 Check the user’s properties about its group in Member Of.
3 Add a new Network Policy of NPS server for a group and then click ‘Next’.
4 Add ‘User Group’ condition.
5 Select the group which is set in AD server.
6 Set the access permission and click ‘Next’.
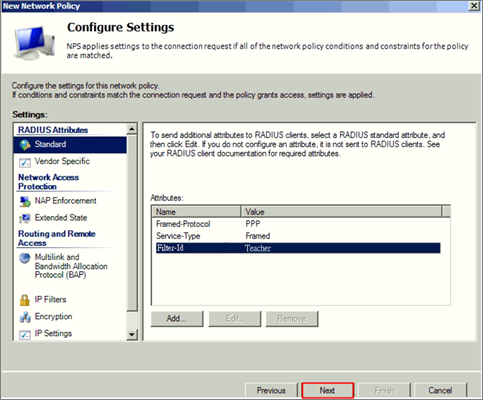
7 Configuration Authentication Methods and click ‘Next’.
8 There are three attribute needed to add Filter-ID as Teacher.
9 Do the same steps to create the other group for other users.
B. Settings on NXC Controller
b1. Using Radius Server
1 Go to CONFIGURATION > Object > AAA Server > RADIUS, click #1 radius, and then click Edit. Set the Server Address, and Authentication Port is 1812. Enter the Key for Radius server and click OK.
2 Go to CONFIGURATION > Object > Auth. Method, click #1 default, and then click Edit. Change the Method to group radius. Click OK to save.
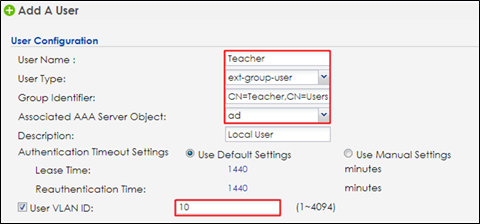
3 Go to Configuration > Object > User/Group > User > Add/Edit
When user type is ‘ext-group-user’, set the corresponded value in ‘Group Identifier’ field, then enable and set the ‘User VLAN ID’ option.
b2. Using AD Server
1 Go to CONFIGURATION > Object > AAA Server > Active Directory, click #1 ad, and then click Edit to configure AD server’s information.
2 In Server Settings, enter Server Address. Here use 172.51.31.112 as the example. Go to AD server to check Base DN. Here is an example for checking the Base DN on Windows server, and it can be copied from clicking right on the domain name > properties > Attribute Editor> distinguished Name > View.
3 In Server Authentication, enter Bind DN and Password. You can check Bind DN in the AD server. In the AD server, clicking right on the Administrator > properties > Attribute Editor > distinguished Name > View. The Password is Administrator’s password in the AD server.
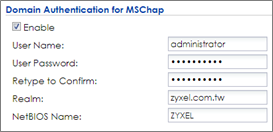
4 In Doman Authentication for MSChap, check Enable and enter the User Name, User Password, Realm, and NetBIOS Name. The Realm is the domain name of the AD server.
5 After finishing the configuration, enter administrator as the Username and click Test in Configuration Validation.
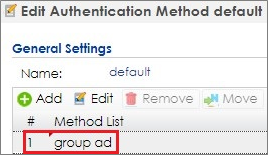
6 Go to CONFIGURATION > Object > Auth. Method. Select to the default method, and click Edit. Select the AD server you create. Click OK.
7 Go to Configuration > Object > User/Group > User > Add/Edit. When user type is ‘ext-group-user’, set the corresponded value in ‘Group Identifier’ field, then enable and set the ‘User VLAN ID’ option. There are two Filter-ID in radius server and the ‘Group Identifier’ of each ext-group-user is the same as the radius server’s setting.
The Group Identifier is the distinguishedName of the group in AD server.
8 Setting the other ext-group-user for student group as the step 4.
Test the Result
Dynamic VLAN by radius server attribute
1 Use mobile phone to connect with SSID DyVlan. Enter the Username and Password which are in VLAN 10 group, and then click Join to connect with the AP.
2 The logged-in client gets an IP in VLAN10.
3 Use the mobile phone to connect with SSID DyVlan. Enter the Username and Password which is in VLAN 20 group, and then click Join to connect with the AP.
4 The logged-in client gets an IP in VLAN20.
Dynamic VLAN by External User Group
1 Use mobile phone to connect with SSID DyVlan. Enter the Username and Password which are in VLAN 10 group, and then click Join to connect with the AP.
2 The logged-in client gets an IP in VLAN10.
3 Use the mobile phone to connect with SSID DyVlan. Enter the Username and Password which is in VLAN 20 group, and then click Join to connect with the AP.
4 The logged-in client gets an IP in VLAN20.
What Could Go Wrong
1 When you set the dynamic VLAN in the NXC controller, the radius server needs to set the corresponding VLAN groups for authentication.
2 Because the dynamic VLAN setting is in the NXC controller, it only supports radius server type “Internal” in CONFIGURATION > Object > AP Profile > SSID > Security List.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight