Collaborative Detection & Response (CDR) keeps your network more secured and healthy
 Zyxel Employee
Zyxel Employee


In recent years, rapidly-expanding attacks surface. More and more companies are encountering a higher risk of transgression than ever before as they are unable to retain security expertise to keep their network away from current threats.
Collaborative Detection and Response is a feature enhancement that further improves the function of regular UTM service. It can block all the client IP traffic when it detects an unsafe connection or when it reaches the pre-set threshold.
When a client’s traffic hits its threshold in CDR, the device will block the client routing traffic.

To use the CDR feature, it requires GSP/UTM Security Pack license and Nebula Pro Pack license; without valid licenses, CDR will discontinue its full or partial functionality.
|
CDR |
Without UTM Security Pack |
With UTM Security Pack |
After UTM Security Pack Expires |
|
With |
CDR
will not function: - Grey out all settings in the CDR GUI page |
CDR full functionality |
CDR will discontinue its full functionality: 1. For “Enabled” state, it will show
“Enabled” and being grey out. |
|
With Nebula Base/Plus Pack |
CDR
will not function: - Grey out all settings in the CDR GUI page |
CDR partially functions: 1. Every GUI page of CDR feature is still
configurable including block/quarantine. Configuration should be saved.
|
CDR will discontinue its full functionality: 1. For “Enabled” state, it will show
“Enabled” and being grey out. 5. Quarantine VLAN will remain kept, not being changed. |
How to configure CDR?

2. Here is the policy table where you could configure the criteria and the actions, as the figure below:
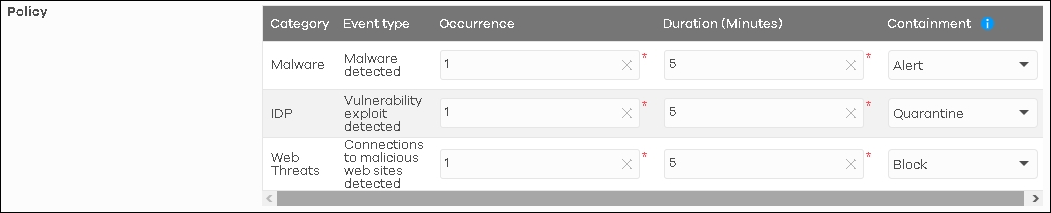
Duration: Within the time duration, CDR detects a threat.
Containment: the action when both criteria have been triggered.
Containment have 3 options:
- Alert: NCC sends an alert email to administrators when triggered. Illegal traffic will blocked by security service function.
- Block: NCC sends an alert email to administrators. Gateway or AP will block the traffic and redirect it to the block page
Note: Quarantine function only work on AP.
CDR database includes:
IDP Signatures:
- CVE-2019-0708(117760, 130797, 130801),CVE-2020-0796(130822,130823,130824,130825), 117723, 117724, 117726
Anti-Malware Signature:
- All Signatures
URL Threat Filter Categories:
- Browser Exploits, Malicious Downloads, Malicious Sites, Phishing
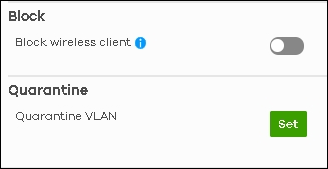
Block is to prevent malicious client to access wireless network
Quarantine is for AP (that supports CDR) that uses dynamic VLAN assignment to isolate clients.
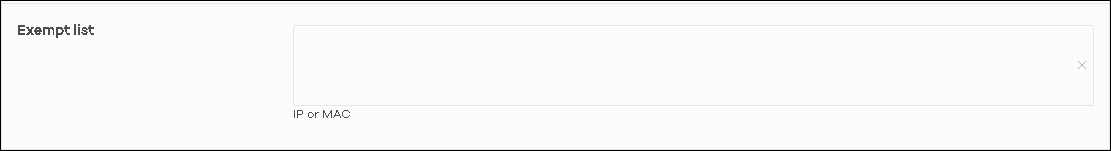
5. Exempt list is a white list where you could input the IP or MAC of the device which you don’t want to be blocked by CDR.
Example of a client blocked by CDR
1. When a client had surfed a malicious website and the act triggered the CDR criteria, the client browser will pop-out a warning message as the figure shown below:
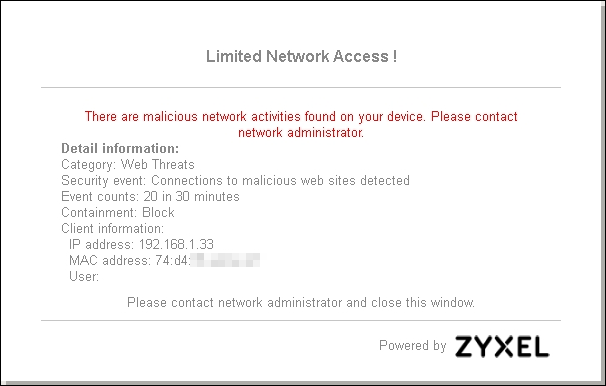
How can the administrator release the client?
1. Go to Site-wide > Monitor > Containment list, you may choose to “Release” or “Add to Exempt list”.
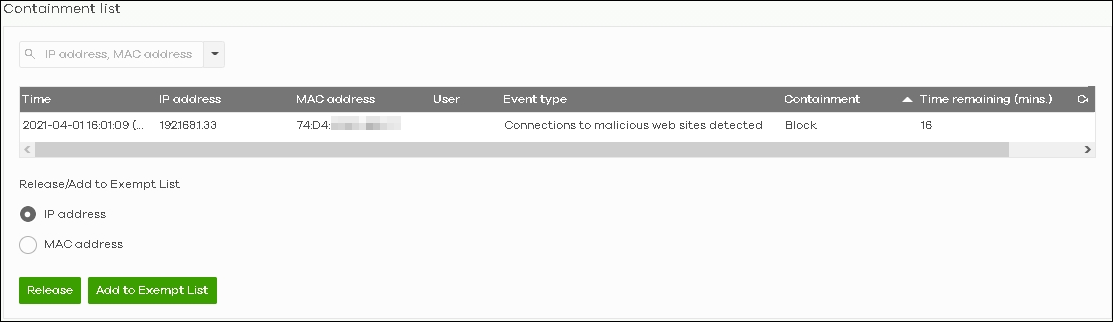
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight