How to get different privileges by RADIUS authentication
 Zyxel Employee
Zyxel Employee



Background:
In the ZyWALL USG, you can configure local users with different privileges such as admin, limited-admin, users and guests. This allows users to have different privileges when they login to the USG. For ext-user accounts, which are authenticated by an external RADIUS server, the USG sets the privilege for account to “user” by default if the RADIUS server does not have the user type information. How do we assign the user type as defined on the USG to the ext-user account on the RADIUS server so that the USG is able to get the user type once a RADIUS user has been authenticated? In this guide, we will show you how to configure a vendor specific attribute to set user type for each user group on the RADIUS (NPS) server.
Configuration Guide:
Conditions
RADIUS server: Windows Server 2008 R2
Create three groups on the RADIUS server: csoadmin, csosecurity and csoguest. Add members in each group.

Goals to achieve
Assign the user type for each user group on the RADIUS server.
RADIUS Server Configuration
1. Go to Administrator Tools > Network Policy Server.
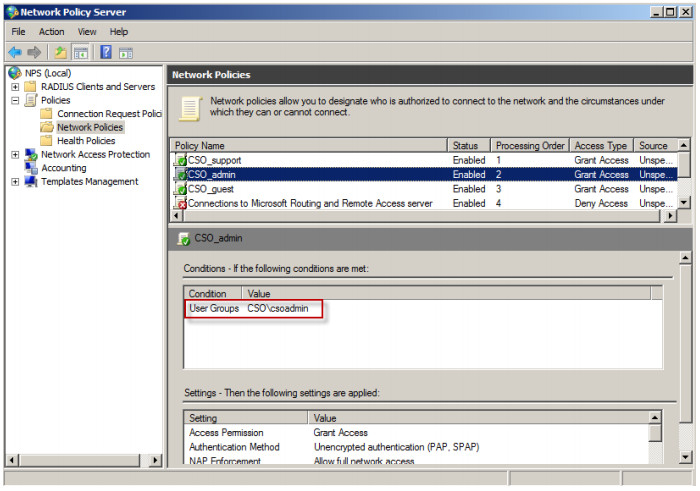
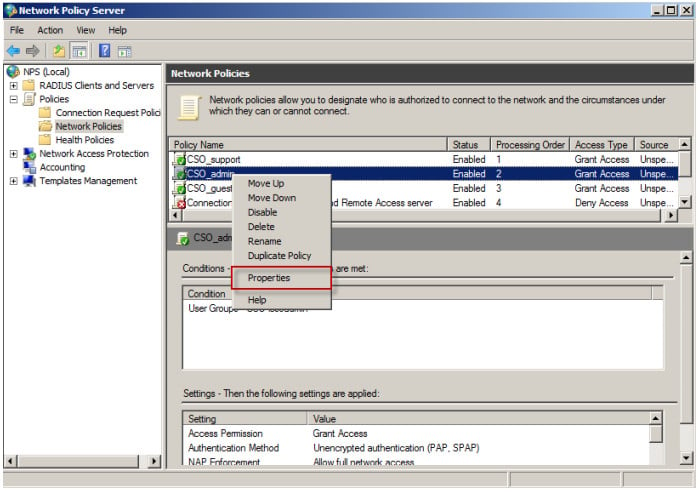
2. Select CSO_admin and go to Properties.
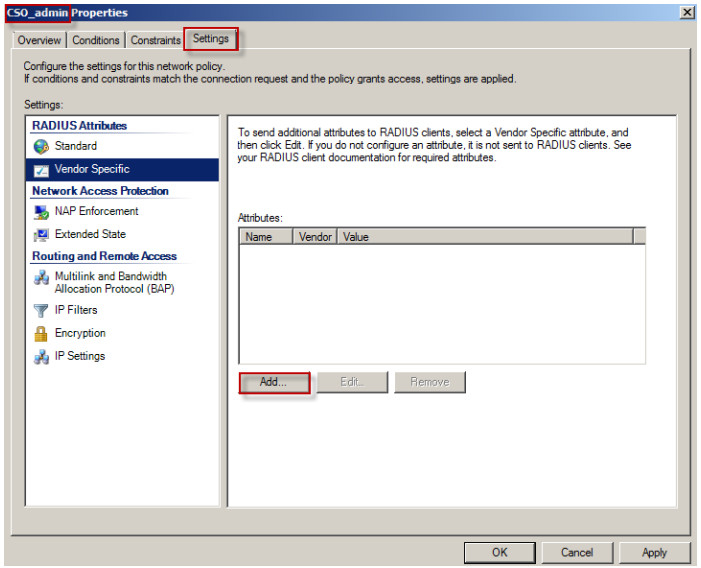
3. Go to Settings > RADIUS Attributes > Vendor Specific. Click on the Add button.
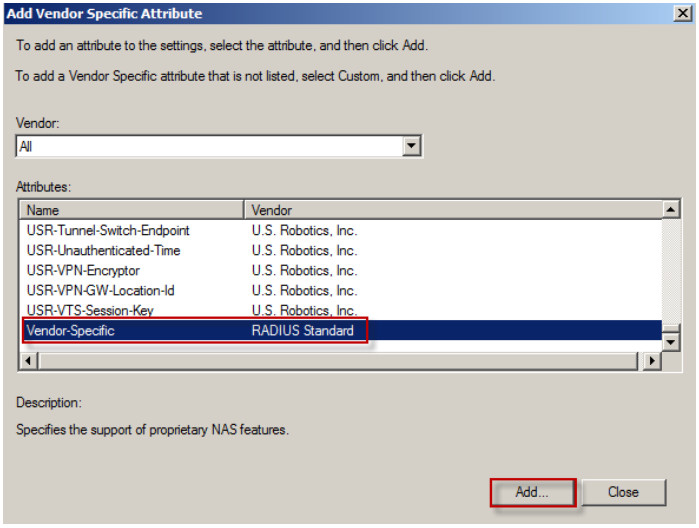
4. Select Vendor-Specific and click on the Add button.
5. Click on the Add button.
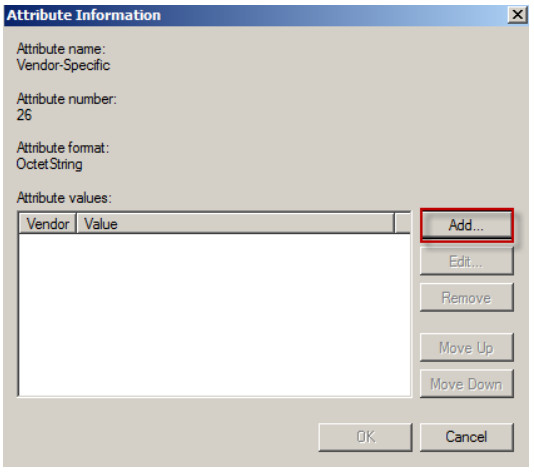
6. Enter ZyXEL’s vendor code: 890. Click on the Configure Attribute button.
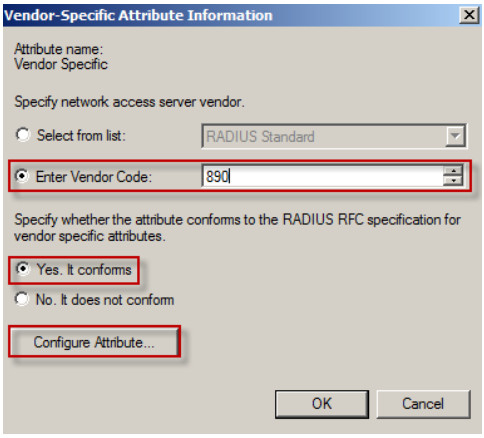
7. You need to configure user type, lease-time and reauth-time in each attribute.
On ZyXEL USG series, we support four types of users: admin, limited-admin, user and guest.
In this example, we set “admin” as the privilege of this group.
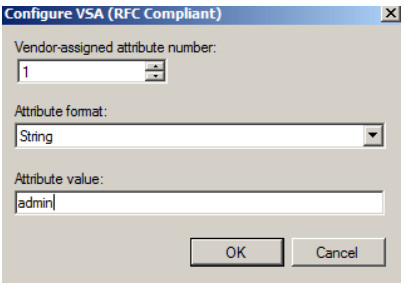
User type
Vendor-assigned attribute number: 1 Attribute format: String
Attribute value: admin
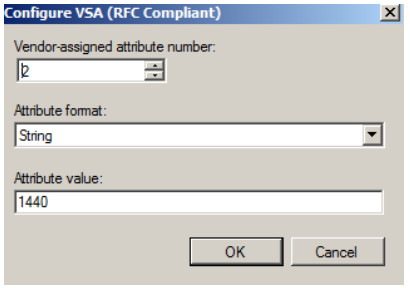
Lease-time
Vendor-assigned attribute number: 2 Attribute format: String
Attribute value: 0~1440
Reauth-time
Vendor-assigned attribute number: 3 Attribute format: String
Attribute value: 0-1440
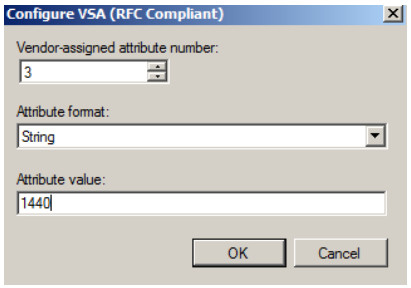
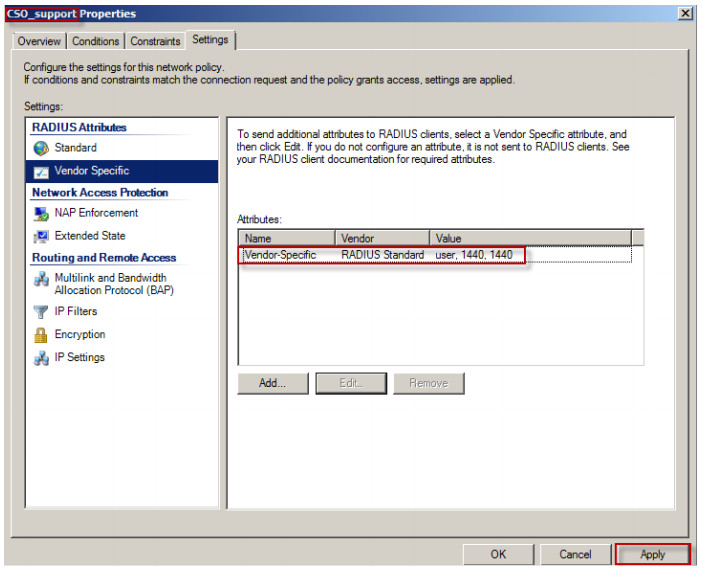
8. User type, lease-time and reauth-time are configured in each attribute for the group CSO_admin.
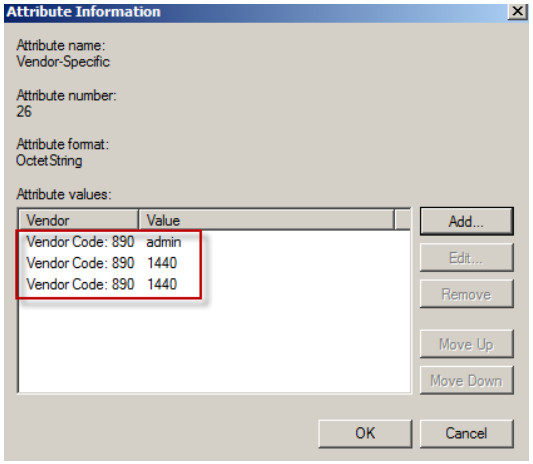
9. Click on the Apply button to finish the privilege setting.
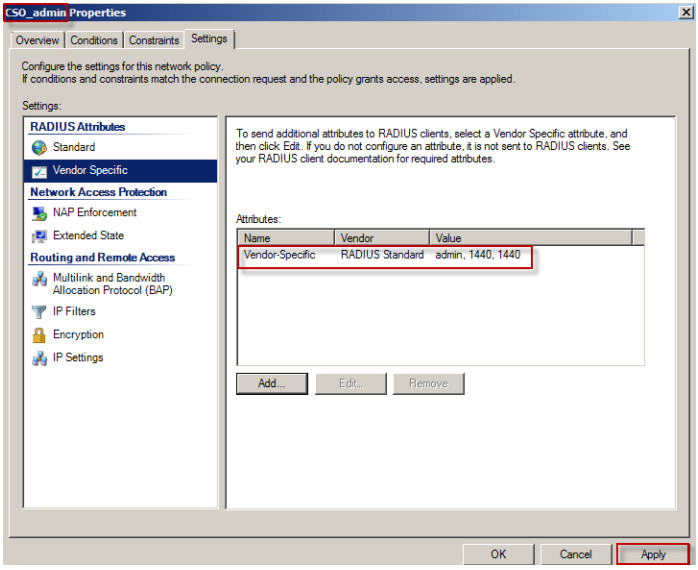
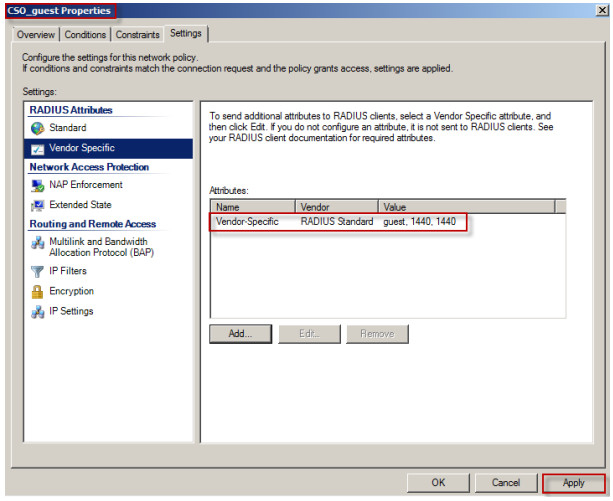
10. Repeat steps 1 to 9 to complete the vendor specific attribute configuration for Network Policy CSO_guest and CSO_support.
Verification
Use the web authentication to check the user type of the logged-in user.
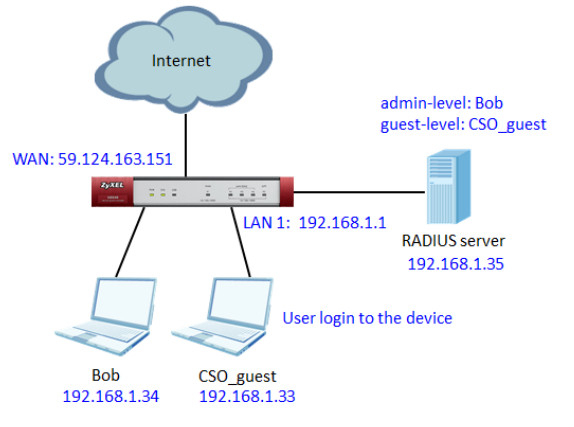
Topology
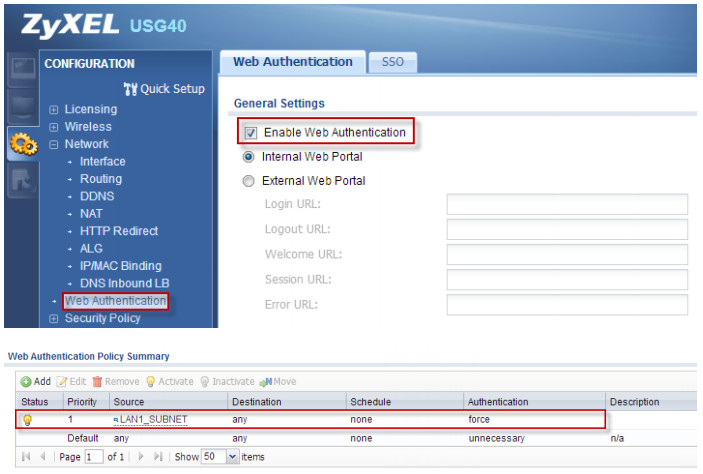
1. Place a check in the Enable Web Authentication checkbox on the USG.
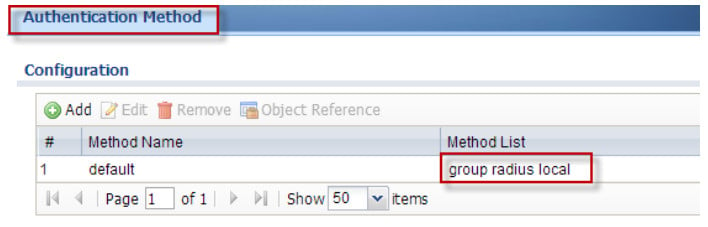
2. Go to CONFIGURATION > Object > AAA Server > RADIUS and configure RADIUS server on the USG
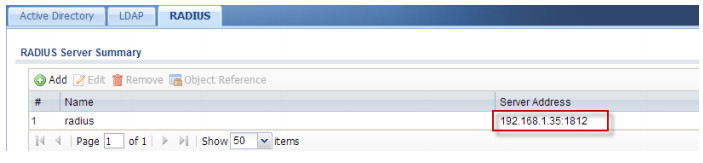
3. Go to CONFIGURATION > Object > AAA Server > RADIUS and configure RADIUS server on the USG
4. Use the guest-level account “CSO_guest” and admin-level account “Bob”to login to the device respectively
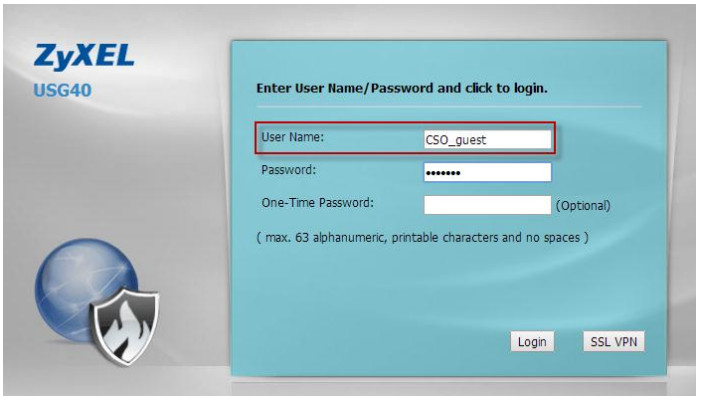
Test Result for account “CSO_guest”
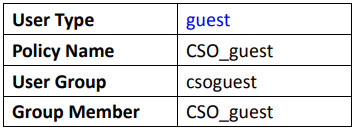
Without configuring vendor specific attribute for the group of the account “CSO_guest”, it belongs to the type “User” when you go to check the logged-in users in the USG.

After following the configuration guide
to set vendor
specific attribute for the group
“CSO_guest” and using
the same guest-level account “CSO_guest” to login to the
device again, the user type becomes “Guest”

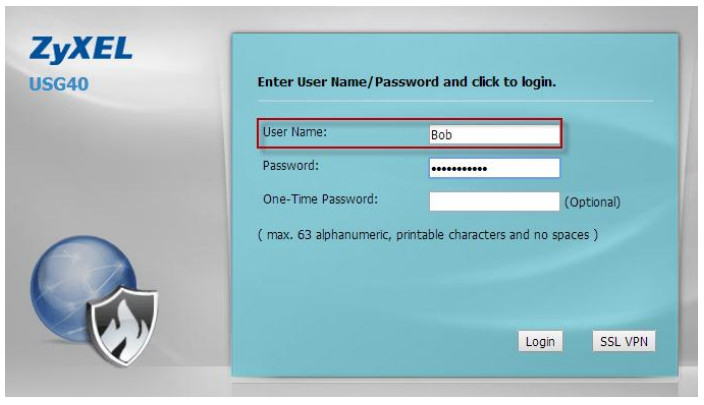
Test Result for account “Bob”

Without configuring vendor specific attribute for the group
of the account
“Bob”, it belongs to the type
“User” when you go to check
the logged-in users
in the USG.

After following the configuration guide
to set vendor
specific attribute for the
group “CSO_admin” and using
the same admin-level account “Bob” to login to the device again, the user type
becomes “Administrator”.

Conclusion:
By following this guide, you can assign different user types for RADIUS group accounts according to their privilege just like the local users. ZyWALL USG will then get the user type, lease time, and re-auth time from the RADIUS server once the logged-in user is authenticated which used to control access of services in the USG.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight