[NEBULA] How to setup L2TP VPN client connection with Authentication-Server?
Options
Zyxel_Chris
Posts: 739  Zyxel Employee
Zyxel Employee




 Zyxel Employee
Zyxel Employee



Nebula Cloud platform offers the option to allow L2TP VPN users to authenticate wired/wireless networks over radius and(or) AD servers, connecting to local domain controllers in the network.
Prerequisite: Client VPN IP addresses cannot overlap LAN subnet
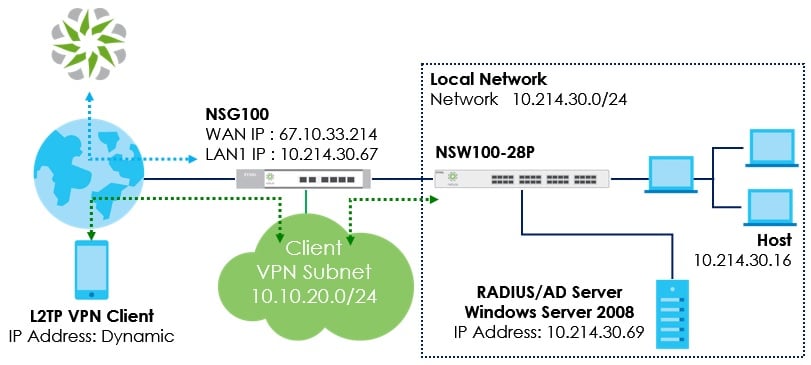
Scenario: Setup L2TP VPN connection with Radius/AD servers in Windows server 2008
Preparation: NSG100 *1, NSW100 *1, RADIUS Server *1 and AD Server *1 in Windows server 2008, iPhone 6S+ *1 and Laptop x1
NCC Configuration for authentication server
1. Configure > Security Gateway > Gateway settings > Authentication server > My RADIUS Server > Add
2. Enter information in My Radius Server > Save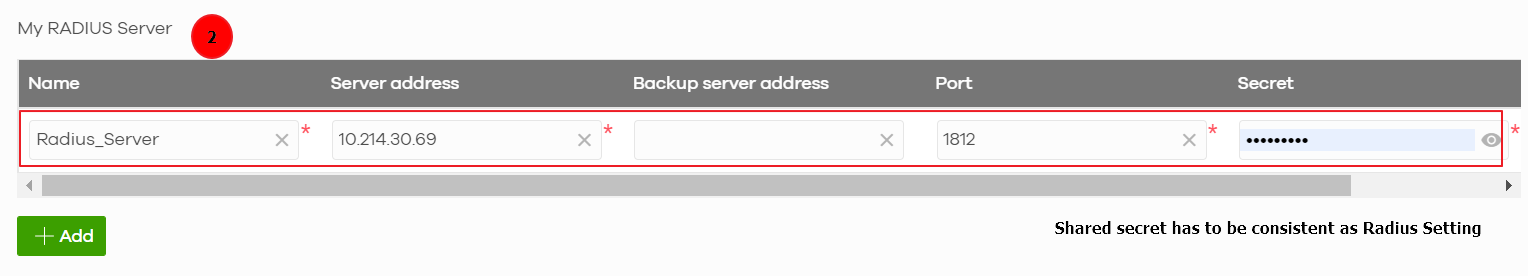
In order to use My RADIUS server option, user is required to configure the Radius server and Active Directory roles in the domain controller
Radius Server Configuration
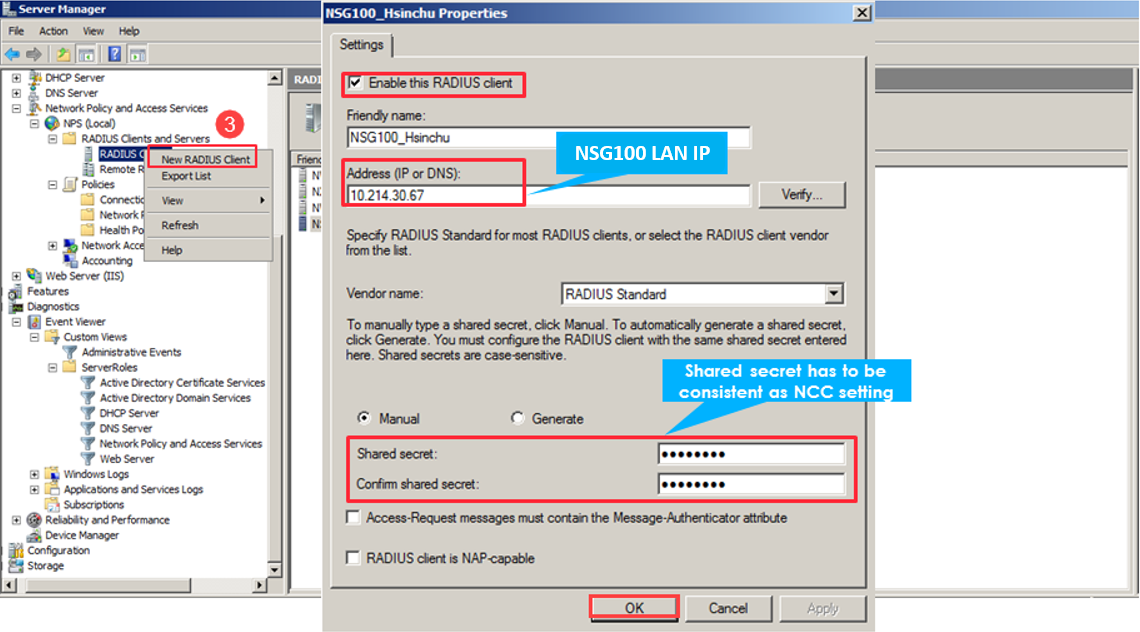
3. Add new RADIUS Client
Server Manager > Role > Network Policy and Access Services > NPS(local) > RADIUS Clients and Servers > RADIUS Client > New RADIUS Client > Enter information in red > OK
4. Add new RADIUS Client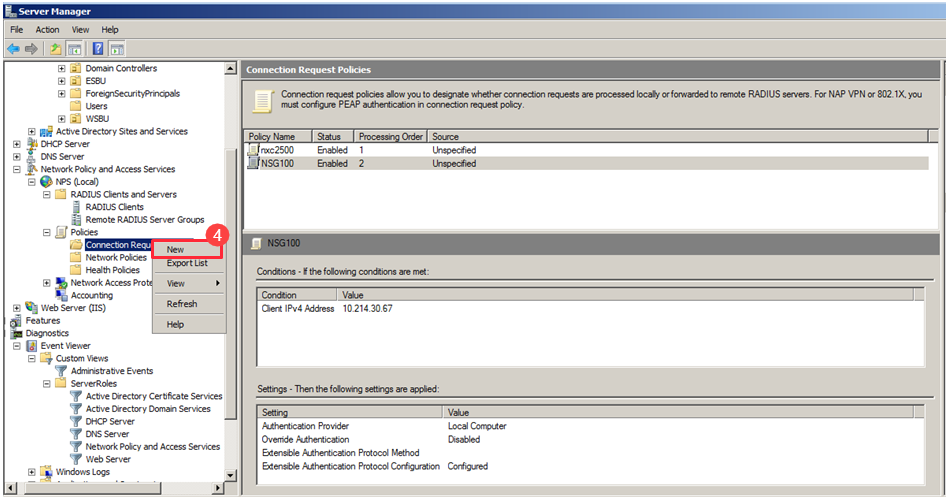
Enter Policy name (eg: USG) > Next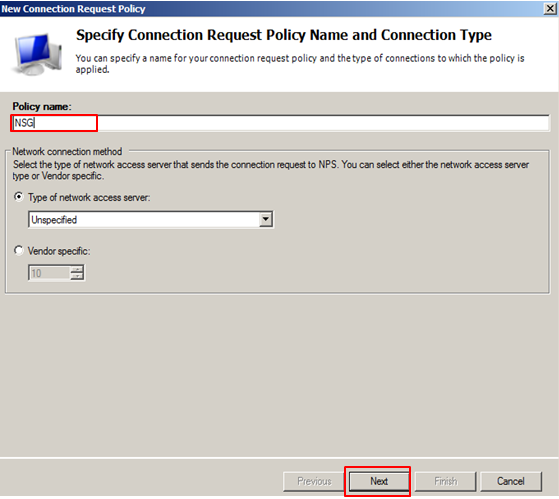
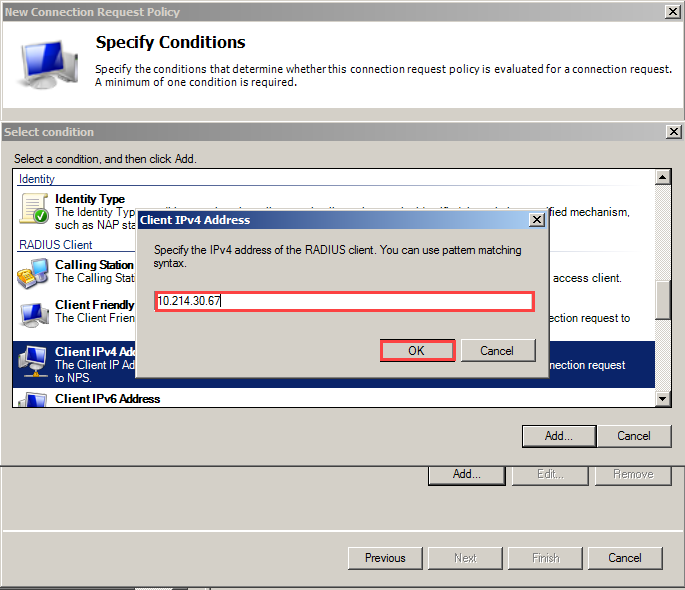
Select Client IPv4 Address > Add > Enter WAN NSG100 IP (eg: 10.214.30.67) > OK
Active Directory Server Configuration
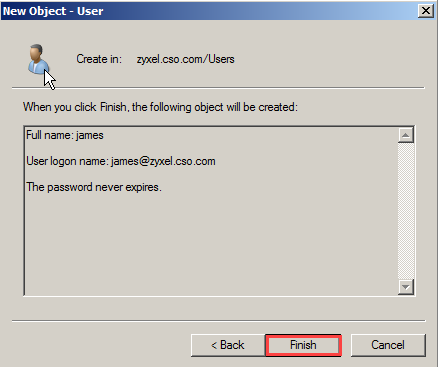
5. Add new AD user
Server Manager >Role > Active Directory Domain Services > Active Directory Users and Computers > zyxel.cso.com > Users > New > User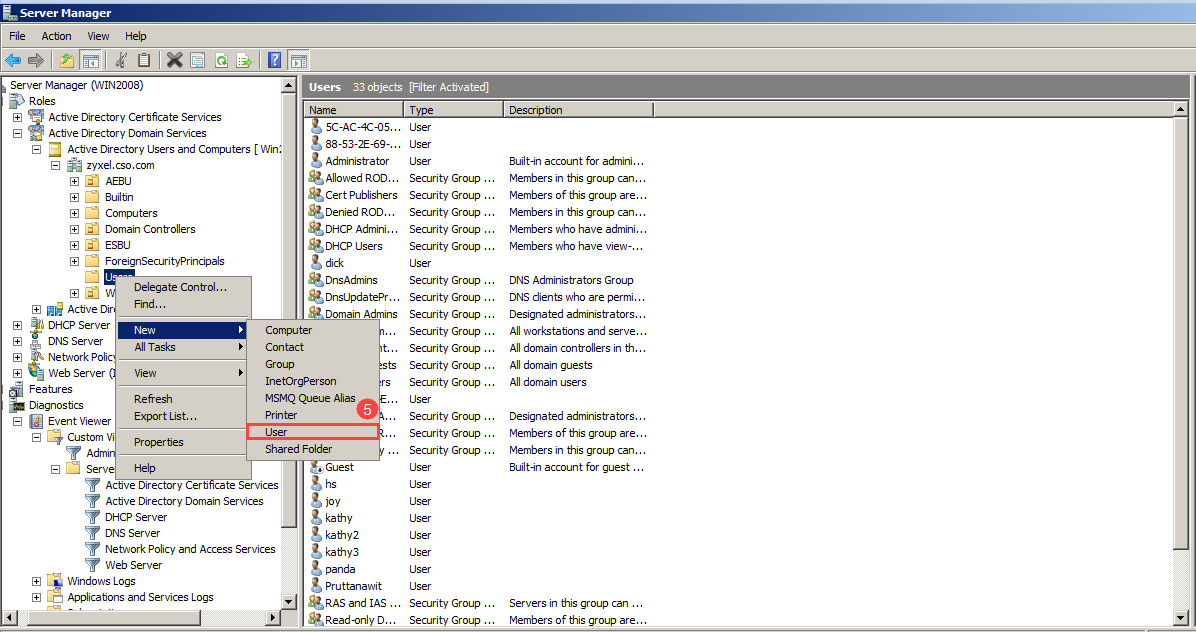
Enter user logon name (eg: james@zyxel.cso.com) > Next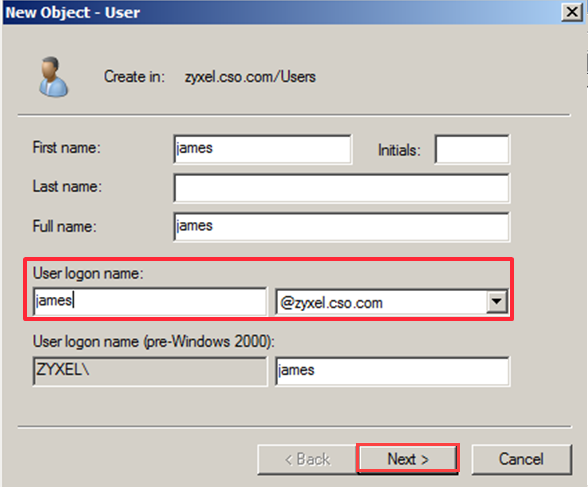
Enter password > Next > Finish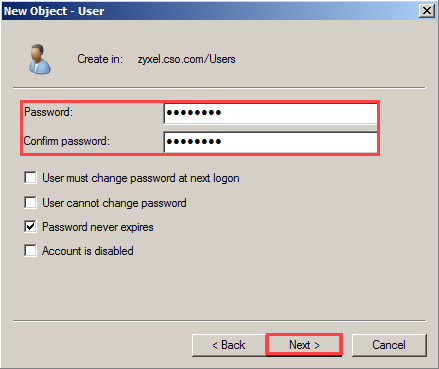
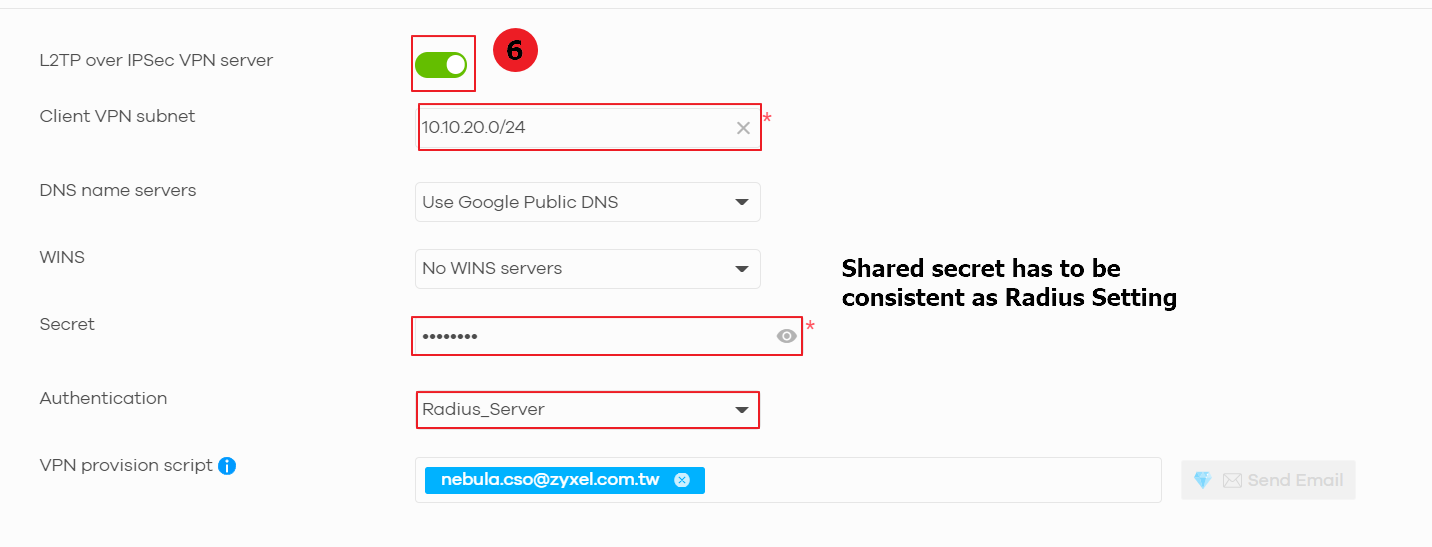
NCC for L2TP VPN client configuration
6. Configure > Security gateway > Remote access VPN
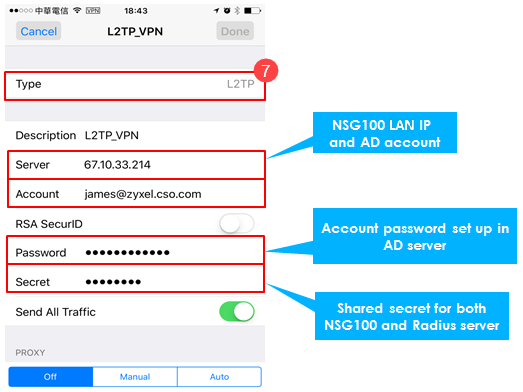
L2TP VPN configuration on the end user (eg: iOS device)
7. iPhone > Setting > General > VPN > Add VPN Configuration > Type > L2TP
Connecting L2TP VPN from the end user (eg: iOS device)
8. iPhone > Setting > Toggle on VPN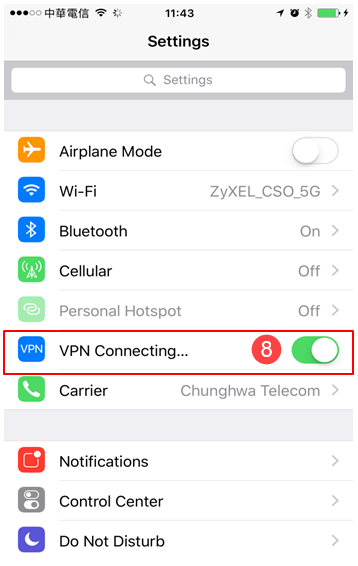
L2TP Connection Result in End Client (Eg: iOS device)
9. iPhone > Setting > General > VPN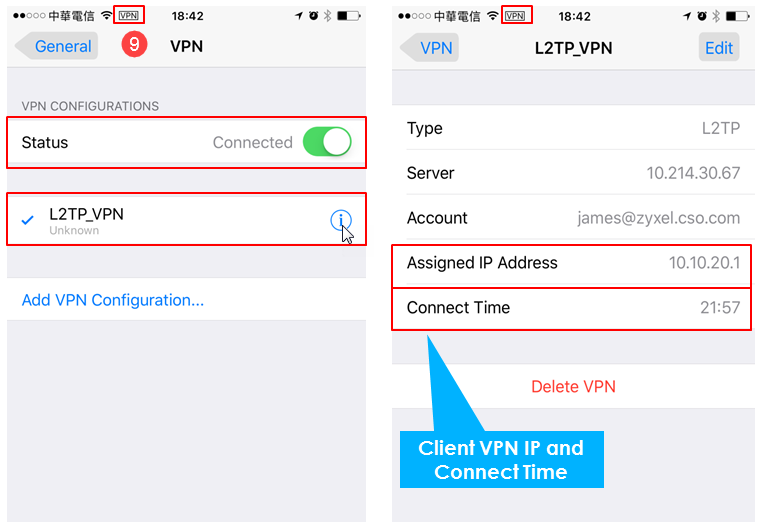
L2TP Connection Result on NCC
10. Monitor > Security gateway > Event log > Category > Enter Auth > Search
Event log displays L2TP client login information
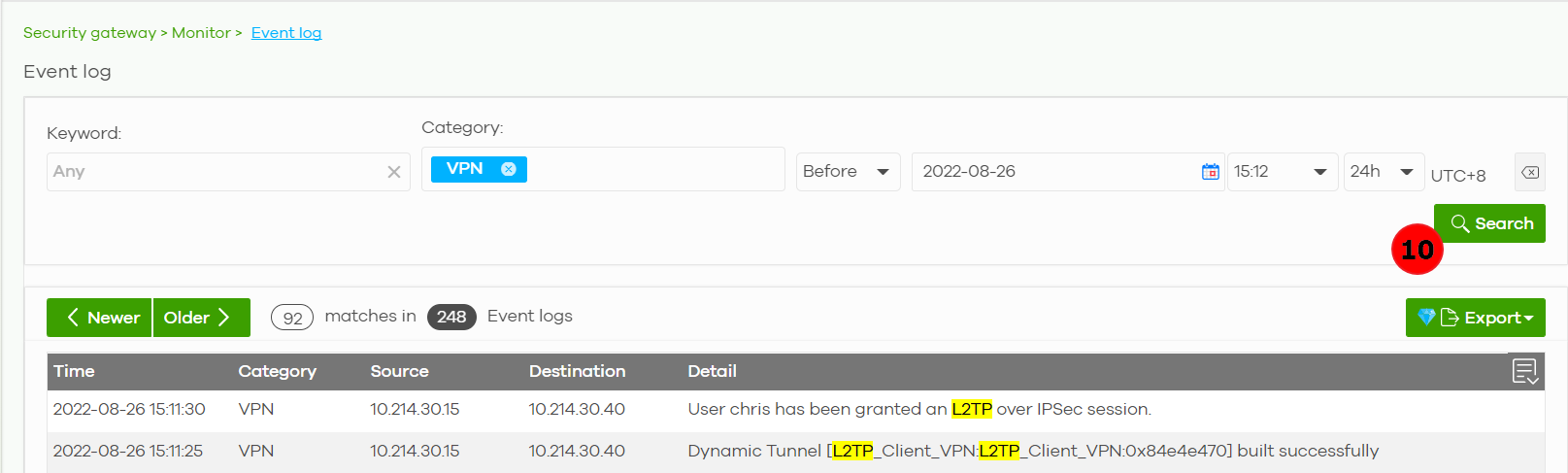
L2TP Connection Result on Event viewer in Windows Server 2008
Server Manager > Diagnostics > Custom views >Event Viewer> ServerRoles > Network Policy and Access Services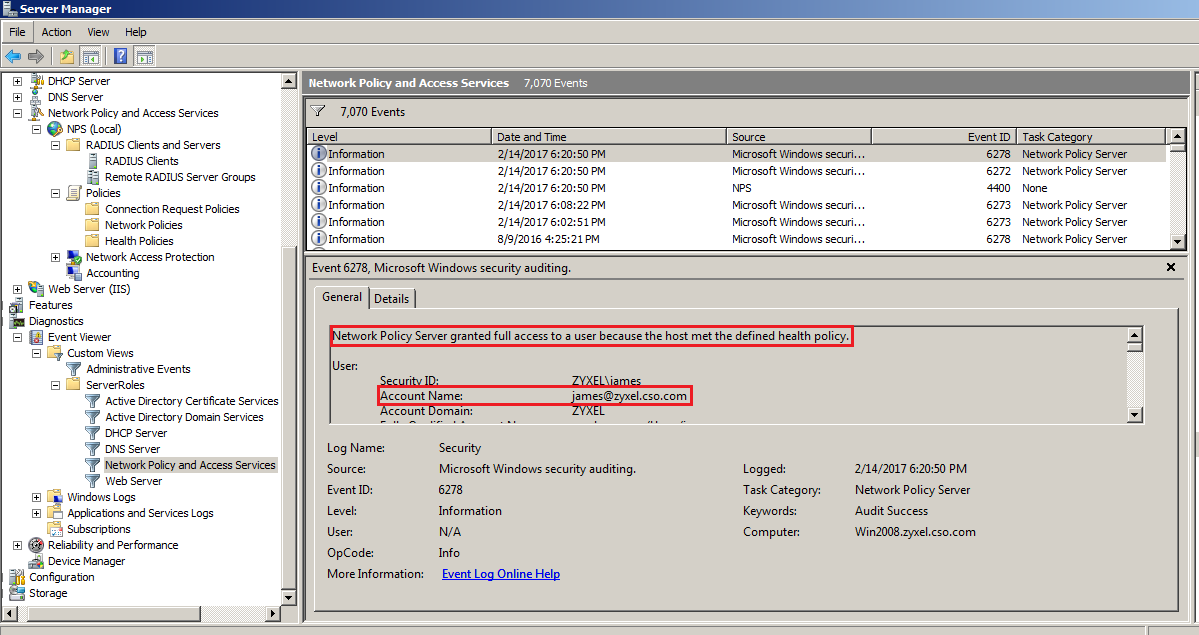
Scenario Result for authorizing L2TP Client over Authentication Server
L2TP Client IP 10.20.20.1 can access LAN host 10.214.30.16.
Prerequisite: Client VPN IP addresses cannot overlap LAN subnet
Scenario: Setup L2TP VPN connection with Radius/AD servers in Windows server 2008
Preparation: NSG100 *1, NSW100 *1, RADIUS Server *1 and AD Server *1 in Windows server 2008, iPhone 6S+ *1 and Laptop x1

NCC Configuration for authentication server
1. Configure > Security Gateway > Gateway settings > Authentication server > My RADIUS Server > Add

2. Enter information in My Radius Server > Save

In order to use My RADIUS server option, user is required to configure the Radius server and Active Directory roles in the domain controller
Radius Server Configuration
3. Add new RADIUS Client
Server Manager > Role > Network Policy and Access Services > NPS(local) > RADIUS Clients and Servers > RADIUS Client > New RADIUS Client > Enter information in red > OK

4. Add new RADIUS Client

Enter Policy name (eg: USG) > Next

Select Client IPv4 Address > Add > Enter WAN NSG100 IP (eg: 10.214.30.67) > OK

Active Directory Server Configuration
5. Add new AD user
Server Manager >Role > Active Directory Domain Services > Active Directory Users and Computers > zyxel.cso.com > Users > New > User

Enter user logon name (eg: james@zyxel.cso.com) > Next

Enter password > Next > Finish


NCC for L2TP VPN client configuration
6. Configure > Security gateway > Remote access VPN

7. iPhone > Setting > General > VPN > Add VPN Configuration > Type > L2TP

Connecting L2TP VPN from the end user (eg: iOS device)
8. iPhone > Setting > Toggle on VPN

L2TP Connection Result in End Client (Eg: iOS device)
9. iPhone > Setting > General > VPN

L2TP Connection Result on NCC
10. Monitor > Security gateway > Event log > Category > Enter Auth > Search
Event log displays L2TP client login information

Server Manager > Diagnostics > Custom views >Event Viewer> ServerRoles > Network Policy and Access Services

Scenario Result for authorizing L2TP Client over Authentication Server
L2TP Client IP 10.20.20.1 can access LAN host 10.214.30.16.
Tagged:
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight