Configure Site-to-Site IPSec VPN between Zyxel Gateway and AWS Virtual Private Gateway
Options
Zyxel_Kevin
Posts: 981  Zyxel Employee
Zyxel Employee




 Zyxel Employee
Zyxel Employee



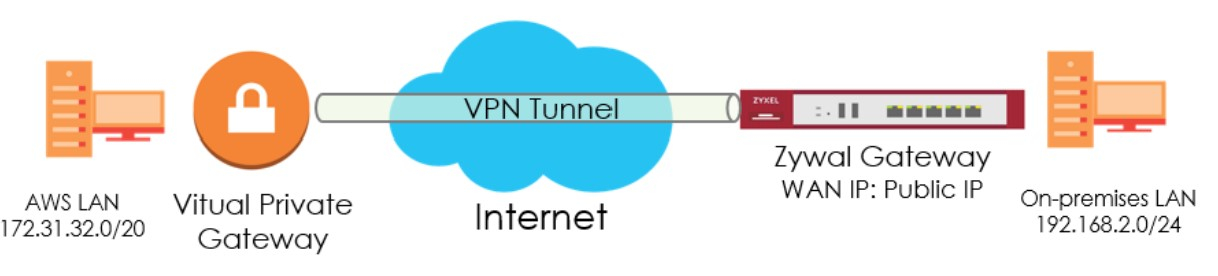
This article describes the procedure to create a site-to-site IPsec connection between
an AWS VPN gateway and Zyxel ATP500 gateway.
Please note that this configuration assumes that the public IP address is directly configured on the Zyxel gateway. Your configuration will be slightly different if your Zyxel gateway sits behind a NAT device.
 A.Configure VPN and Static Route on AWS
A.Configure VPN and Static Route on AWS
1. Create AWS Customer Gateway
1) Go to the AWS Portal: https://aws.amazon.com/console/ and sign in with your credentials
2) Under 'Services', search and click on 'VPC'.
3) Filter your VPC, for the ease of navigation. In this case, I used the default VPC
4) On the left navigation pane, scroll down to VIRTUAL PRIVATE NETWORK (VPN). Click on 'Customer Gateways'.
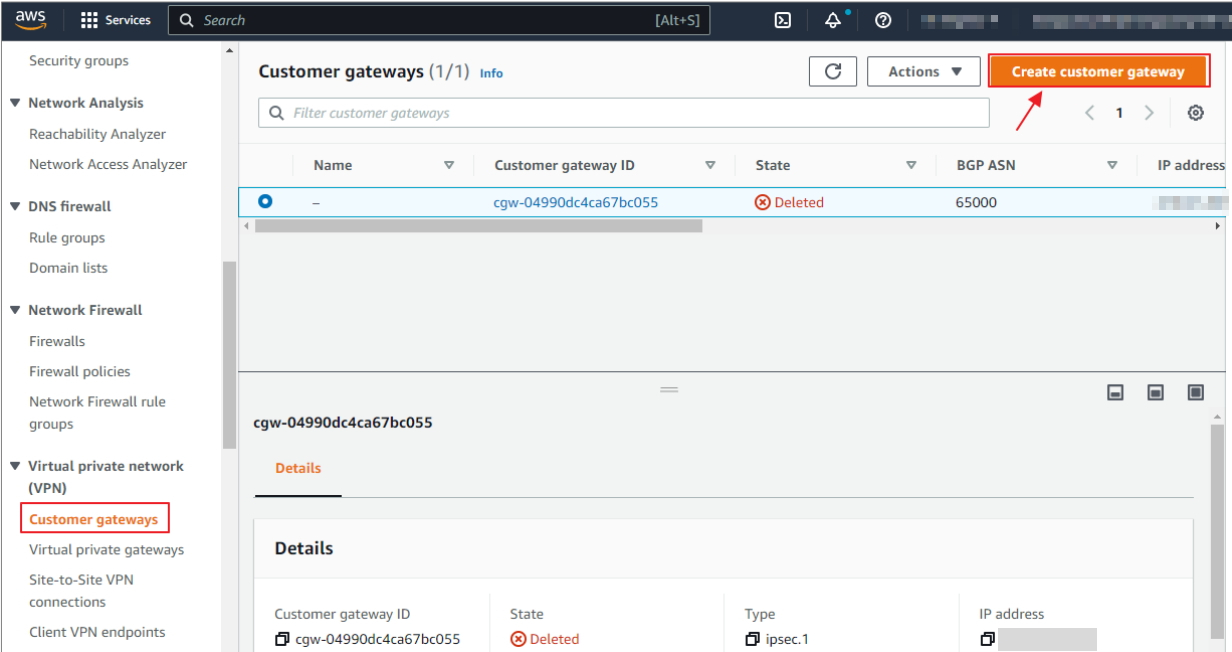
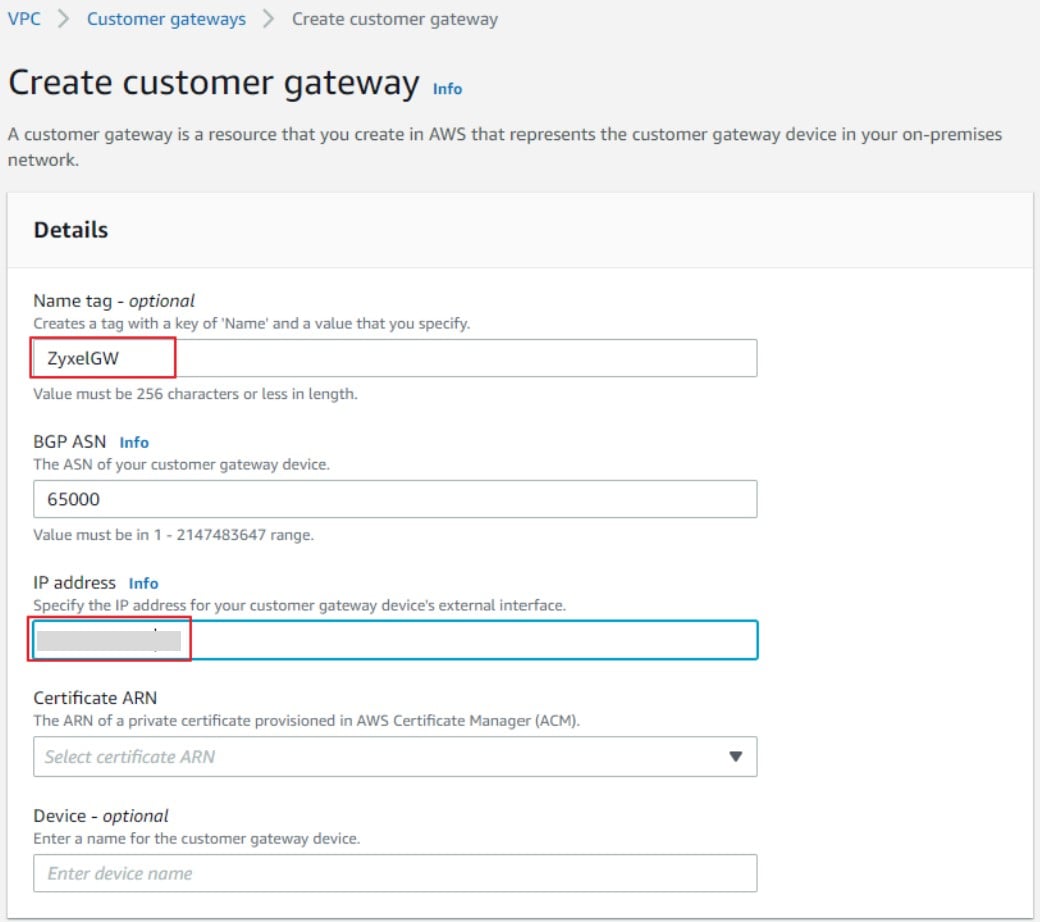
5) In the "Create customer gateway" blade, configure the following:
- Name: Specify any descriptive name.
- BGP ASN: leave as default value (65000)
- IP Address: Specify the public IP address of your Zyxel gateway.
- Certificate ARN (optional): In our scenario, no Certificate is selected.
- Device (optional): In our scenario, no Device is selected
2. Create a Virtual Private Gateway ( Attaching the VGW with your VPC)
1) Select the virtual network for which you want to create a virtual network gateway. In the left navigation pane, scroll down to VIRTUAL PRIVATE NETWORK (VPN). Click on 'Virtual Private Gateways'.
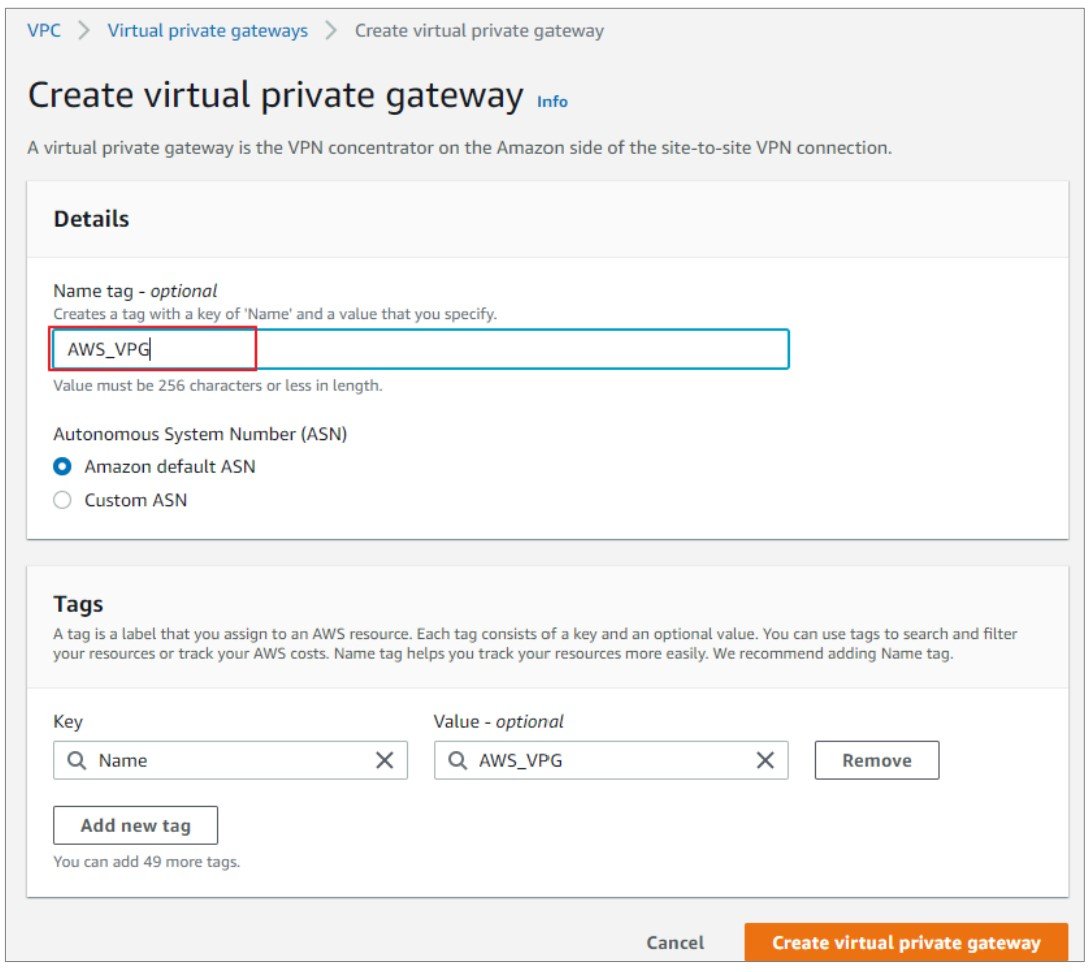
2) In the "Create Virtual Private Gateway" blade, configure the following:
- Name tag: Specify a descriptive Name
- ASN: Select the applicable option. In our scenario, select Amazon default ASN
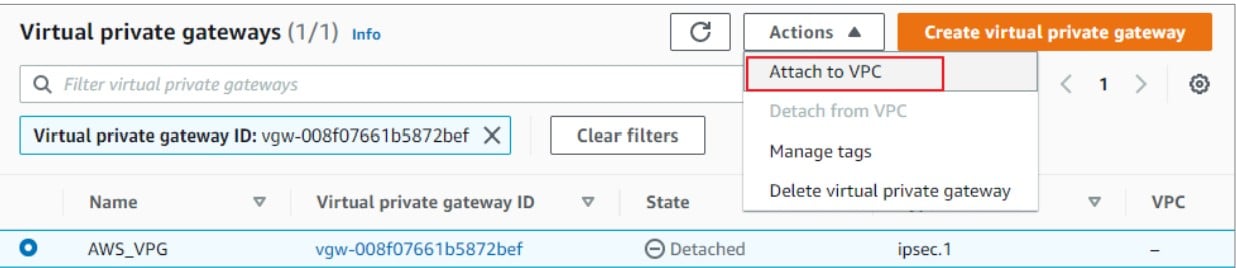
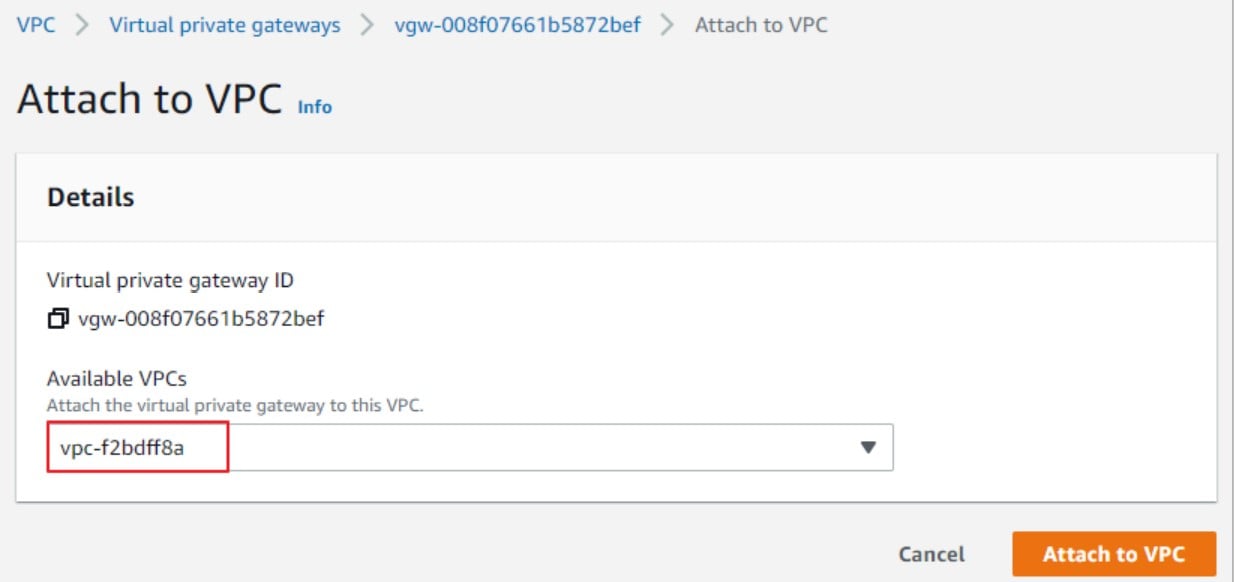
3) Attach Virtual Private Gateway (VGW) to the VPC.
- Select the newly created VGW.
- Click on Actions and select Attach to VPC. Once the VGW is attached to the VPC, reapply the filter on your VPC as described above step
3. Create the Site-to-Site VPN connection
1) In the left navigation pane, scroll down to Site-to-Site VPN Connections. Click on 'Create VPN Connection'.
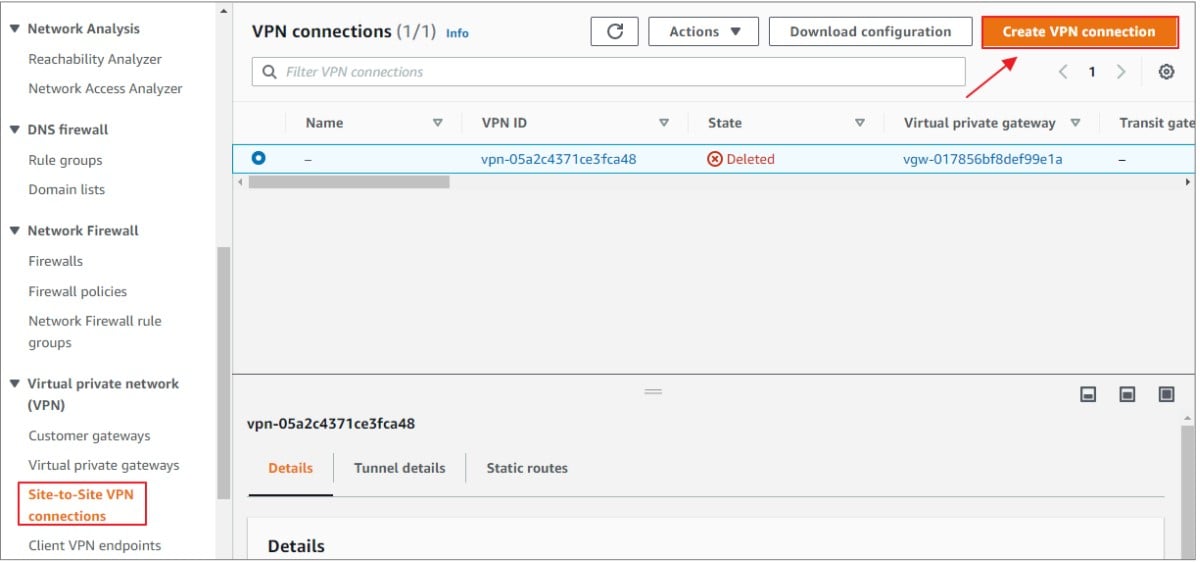
2) In the "Create VPN Connection" blade, configure the following:
- Name Tag: Specify a descriptive Name for the VPN connection
- Target Gateway Type: Select Virtual Private Gateway
- Virtual Private Gateway: From the drop-down box, Select the gateway created in above step
- Customer Gateway: Select Existing.
- Customer Gateway ID: From the drop-down box, Select the gateway created in above step
- Routing Options: Select Static.
- Static IP Prefixes: Provide the LAN address range behind the Zyxell Gateway
- Local IPv4 Network: Zyxel gateway LAN resources
- Remote IPv4 Network: AWS side resources
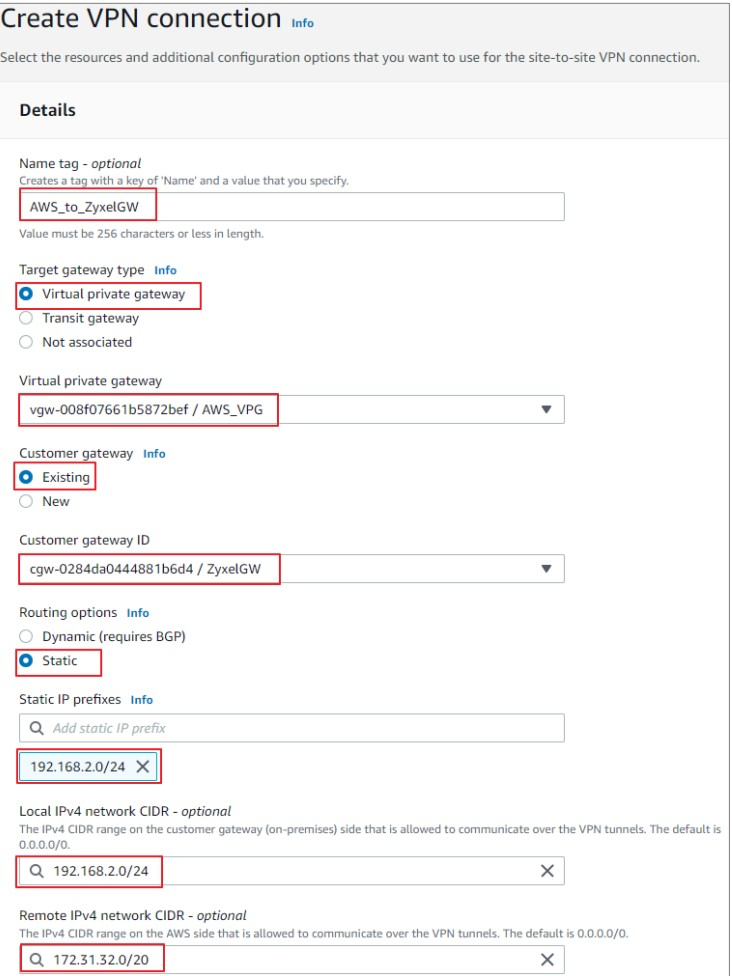
3) (Optional) Enable VPN logging. . For troubleshooting, you only have this option to enable the VPN logs when creating the VPN connection on AWS. You can not enable the option using AWS Console once the VPN connection created. The VPN logs will send to CloudWatch logs, specify the log group and format file to store.
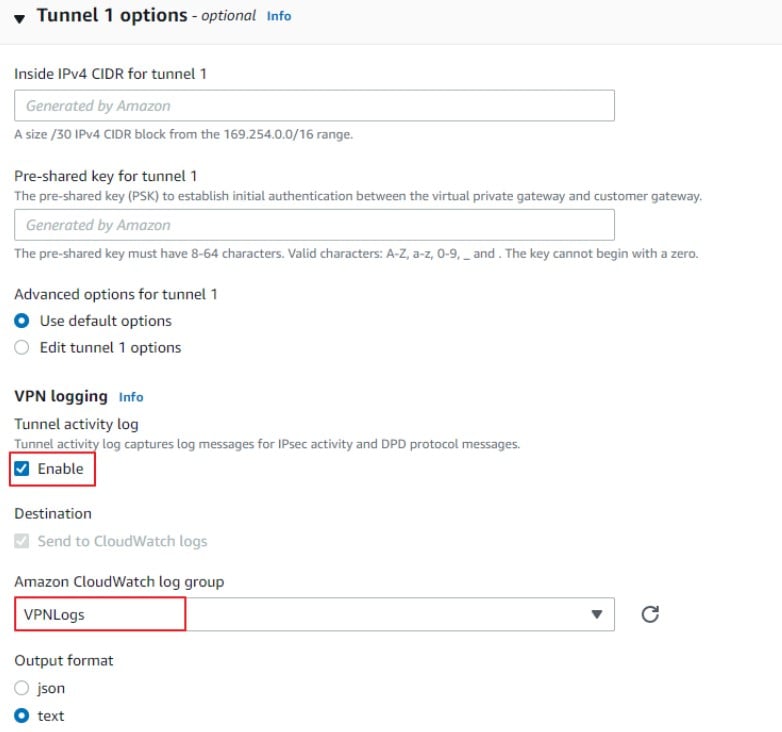
4. Download and extract needed information from the configuration file
1) Select the newly created VPN connection and click on Download Configuration.
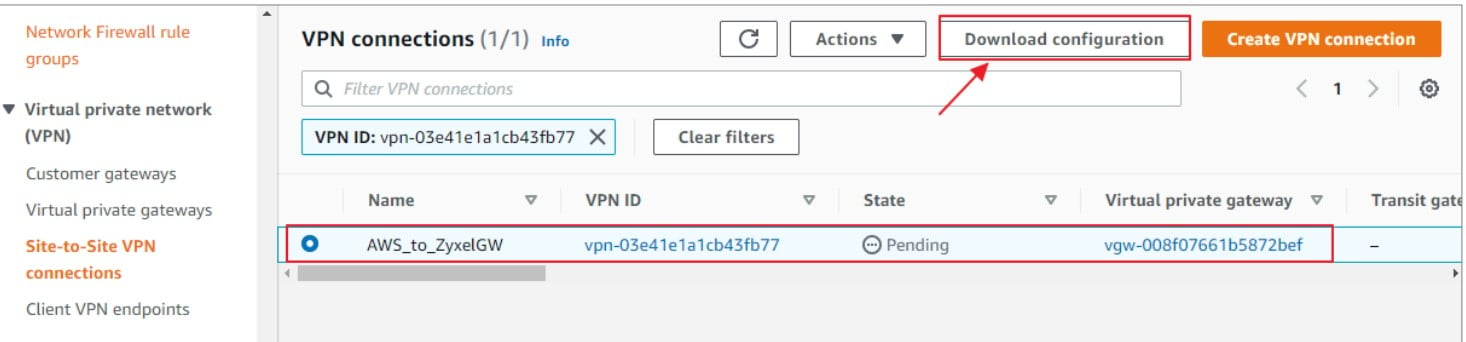
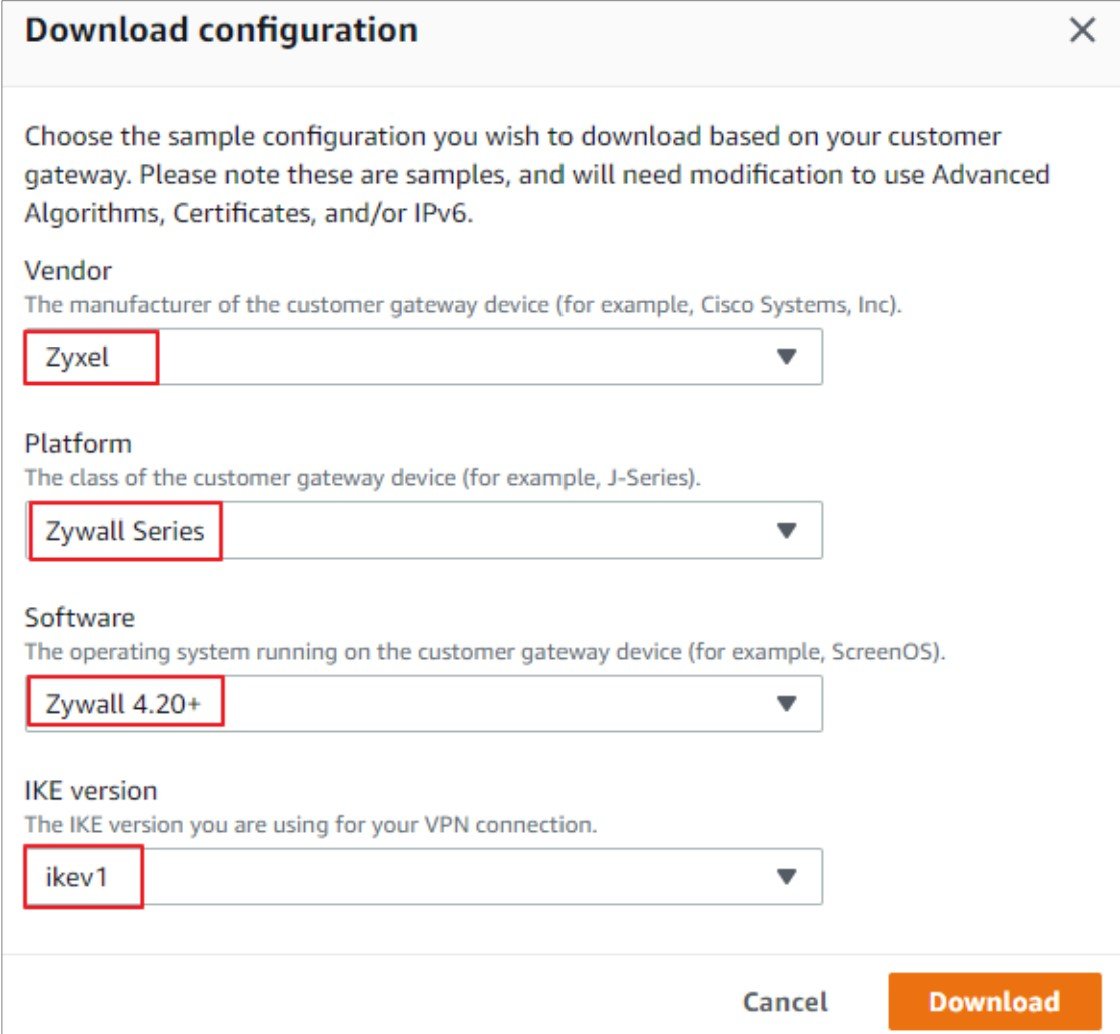
 2) In the "Download configuration" blade, select the following:
2) In the "Download configuration" blade, select the following:
- Vendor: Zyxel
- Platform: Zywall Series
- Software: Zywall ZLD4.20+
- IKE version: ikev1
Click on "Download"
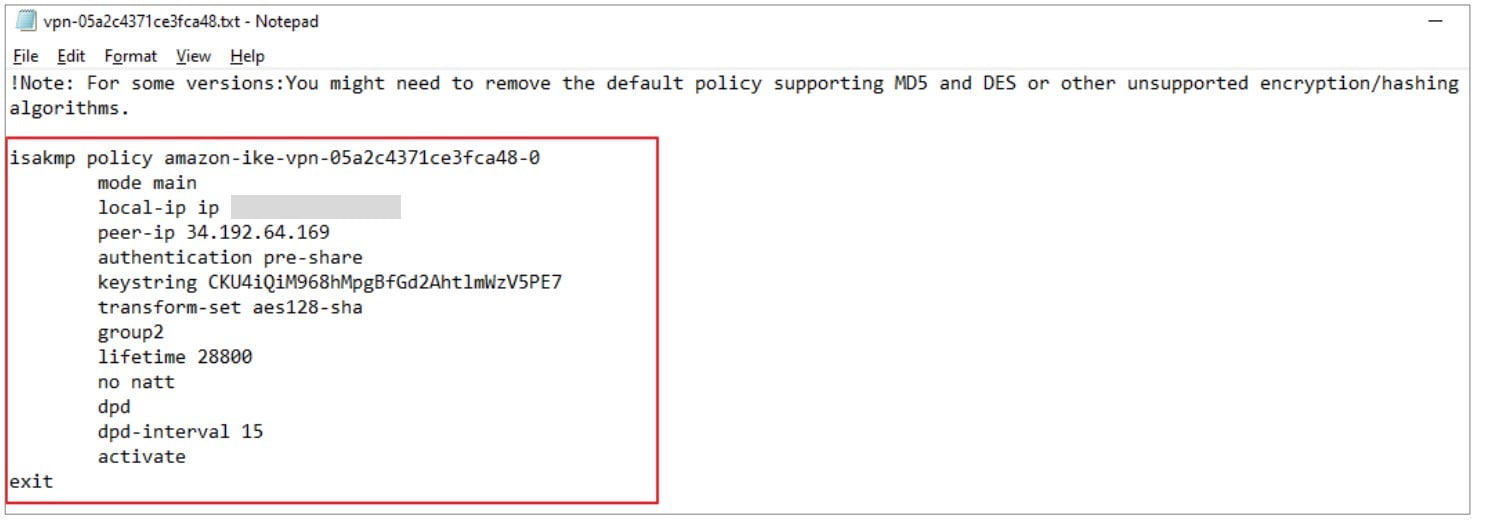
The configuration file is downloaded in txt format. The parameters given in the downloaded file should match the Phase 1 & Phase 2 parameters in the on-premises Zyxel gateway IPSec policy
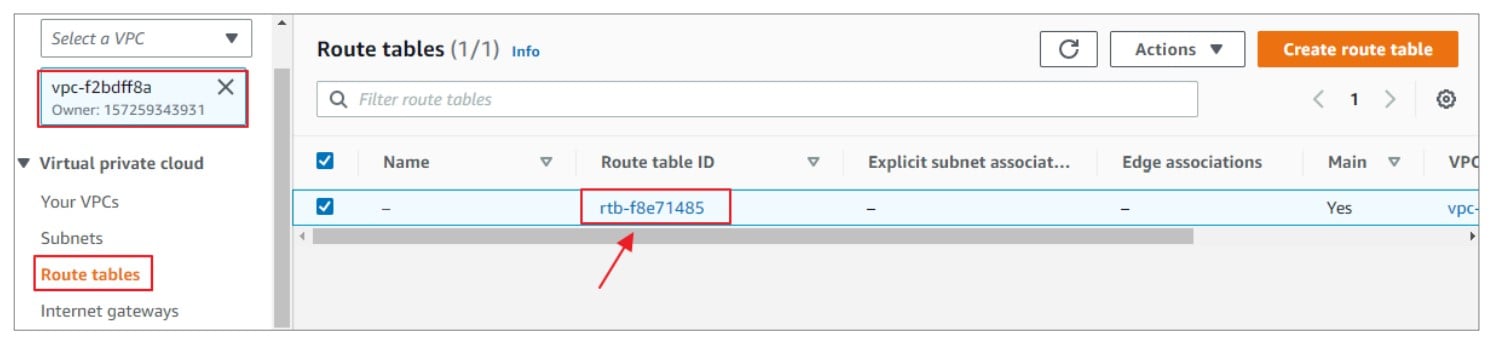
5. Create a route in the route table associated with your VPC
1) In the left navigation pane, select your VPC. Navigate to VIRTUAL PRIVATE CLOUD > Route Tables. Select the associated Route Table.
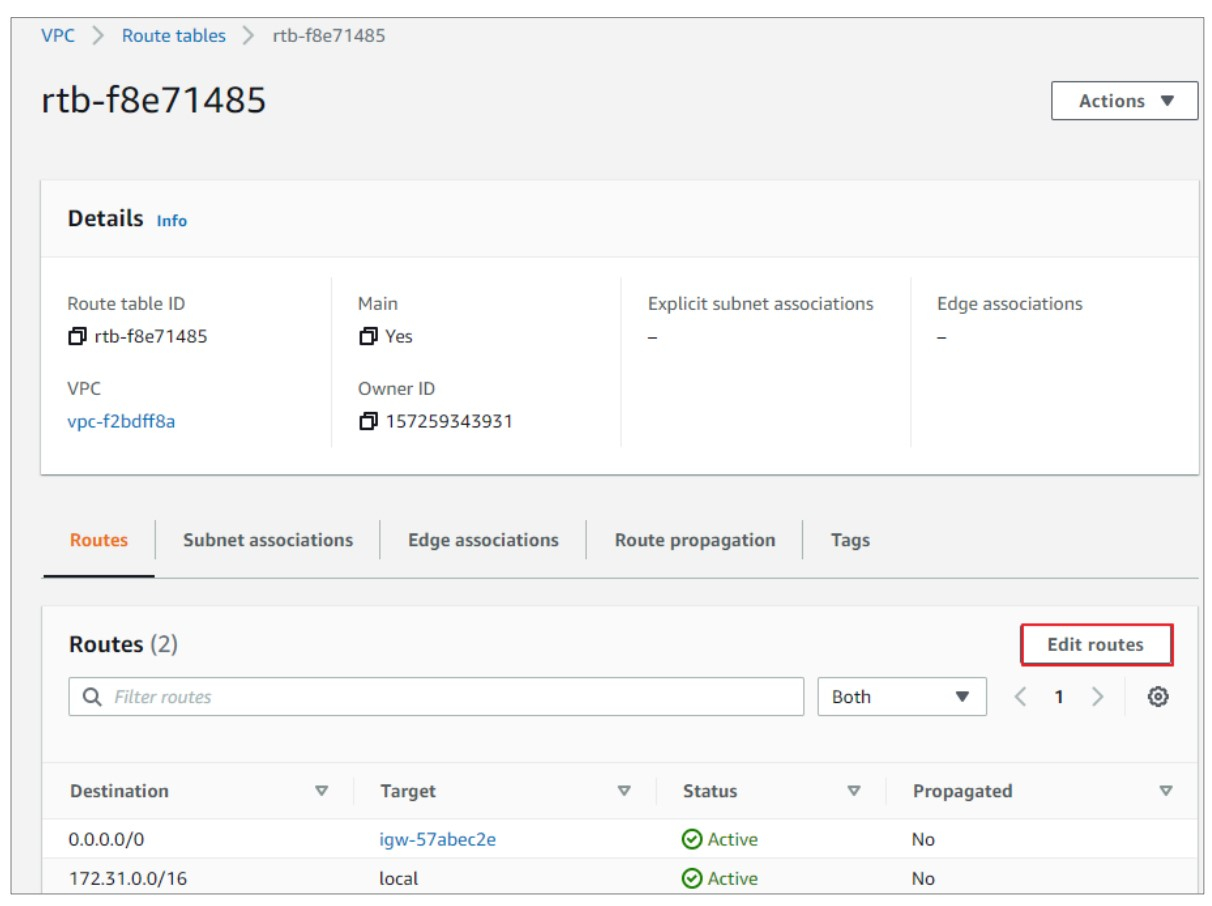
2) In the bottom navigation:
- Select the Routes tab.
- Click on Edit routes.
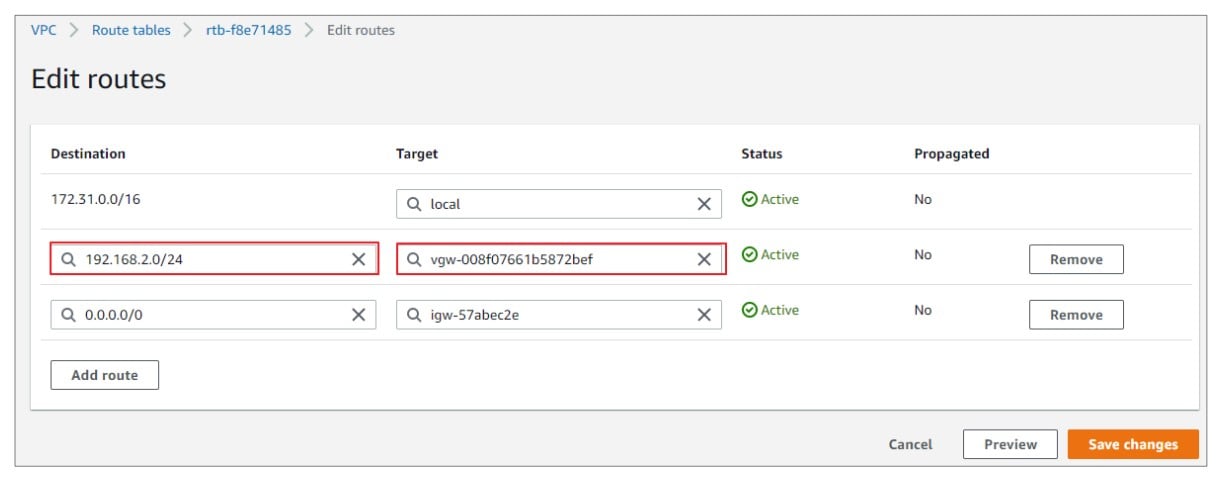
3) Click on Edit routes and configure the following:
- Destination: LAN subnet behind Zyxel Gateway
- Target: Select the Virtual gateway created in Step 2.
- Click on Save routes.
B. Configure VPN and Static Route on Zyxel Gateway
AWS suggest you to establish 2 VPN connections to AWS, you can refer the txt file to create the VPN gateway, VPN connection, VTI interface, and static route. Note: Zyxel gateway does not support “-” character for VPN gateway and connection name, you must to modify.
1. Configure 2 VPN gateways as same as the txt file you download
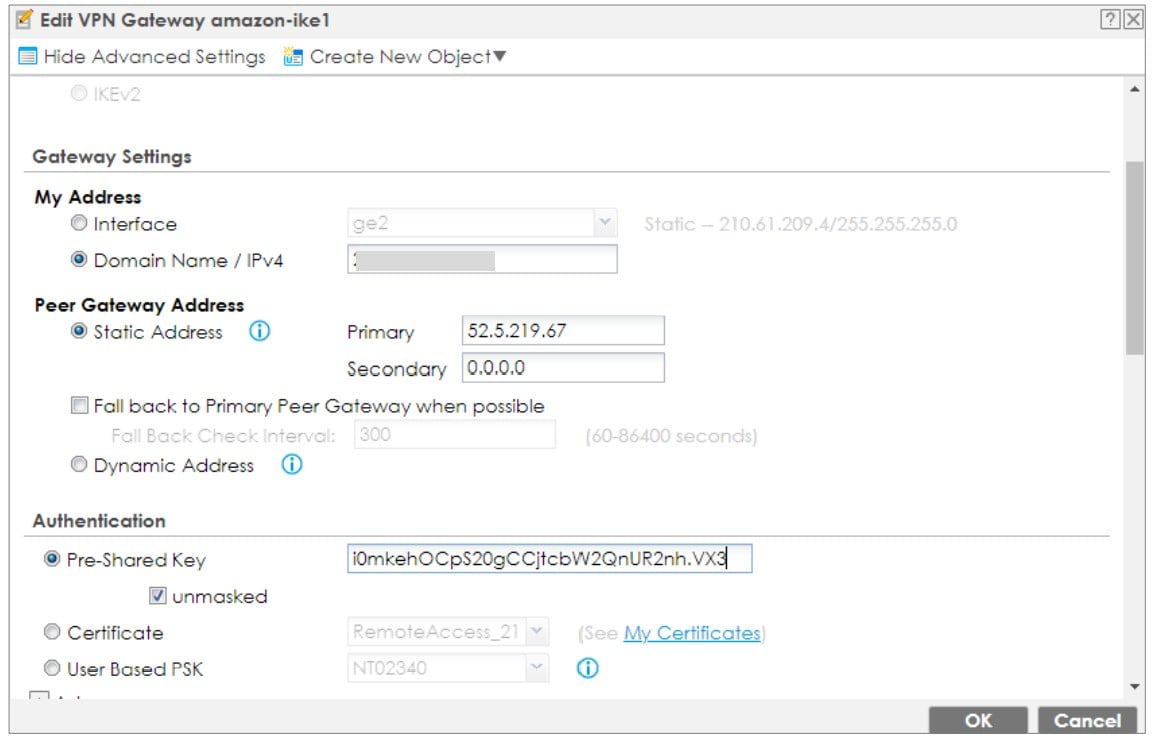
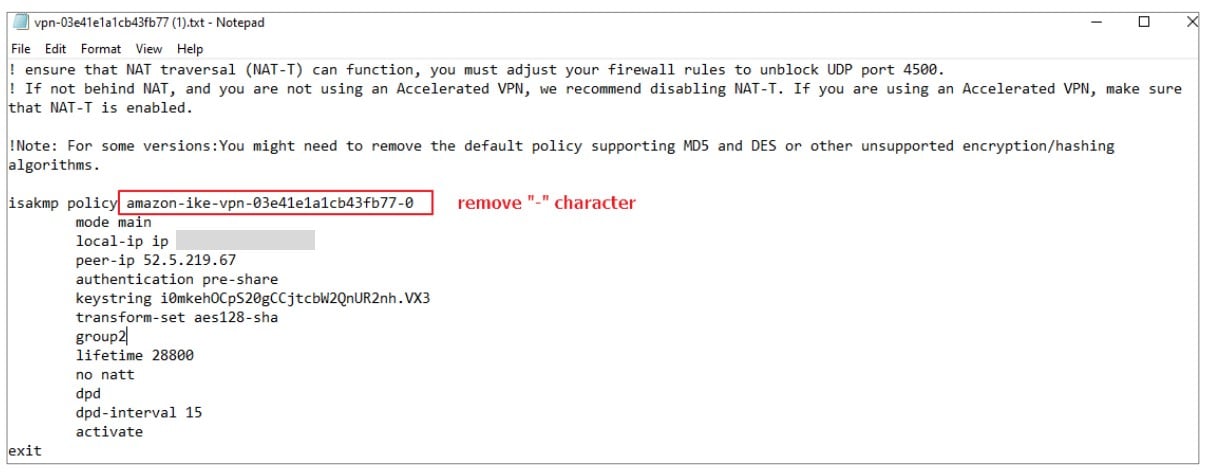
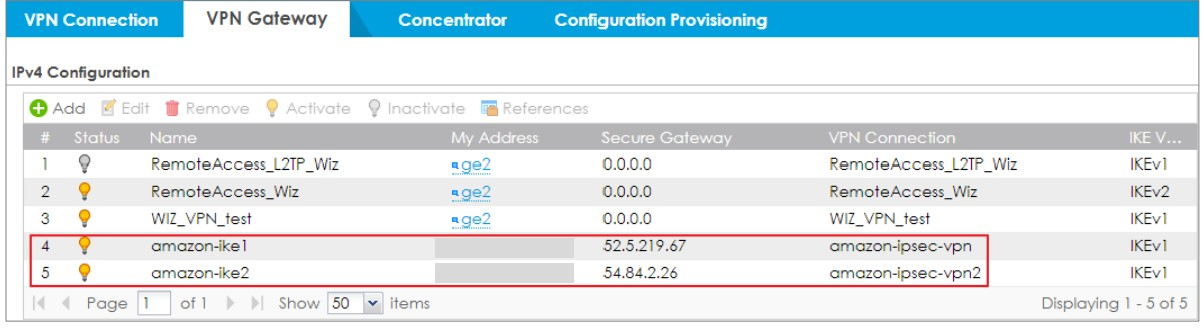
2. Configure 2 VPN connection as same as the txt file you download
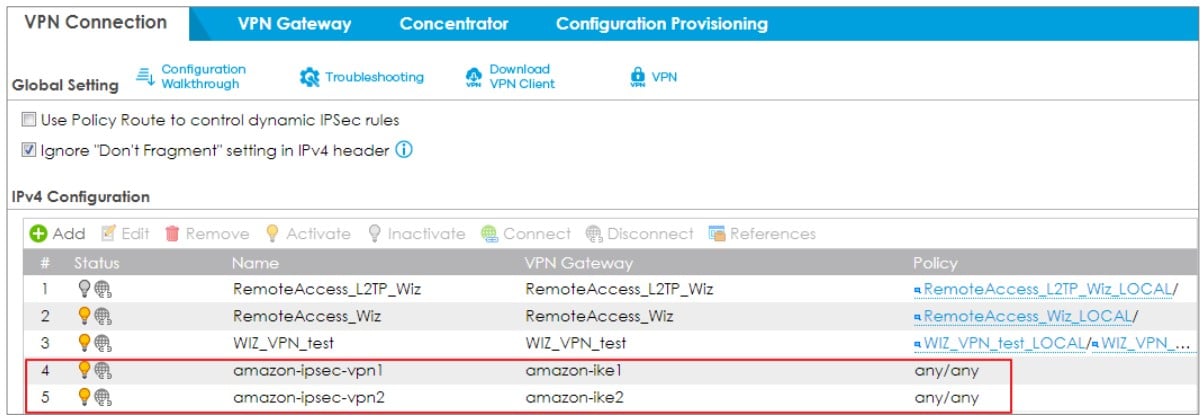
3. Configure 2 VTI interfaces corresponding to 2 VPN rules
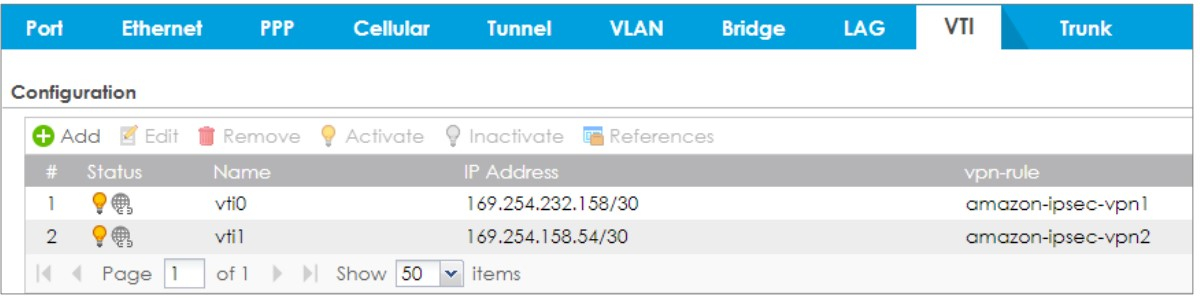
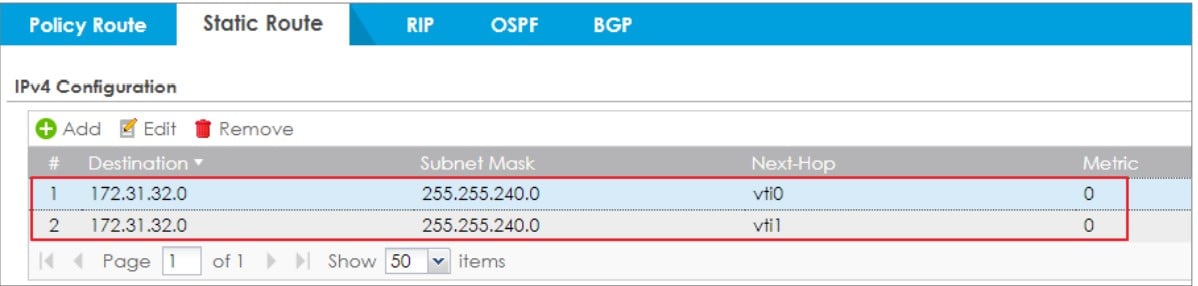
4. Configure static route to forward the traffic to AWS LAN via VTI interfaces
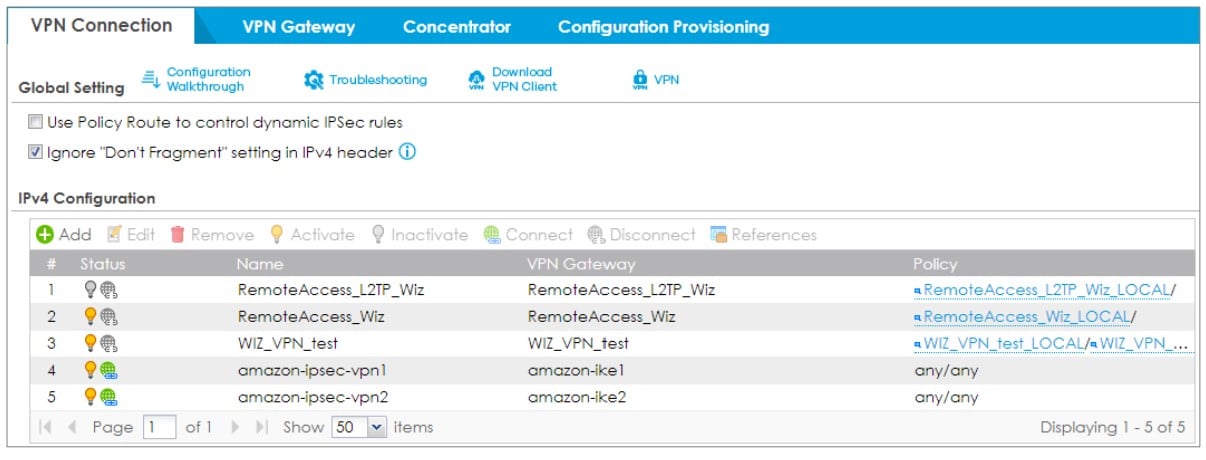
5. Go to VPN connection tab, choose the VPN rule to connect.
C.Verification and Troubleshooting
1. PC under Zyxel Gateway LAN try to ping the EC2 Instance under the AWS LAN
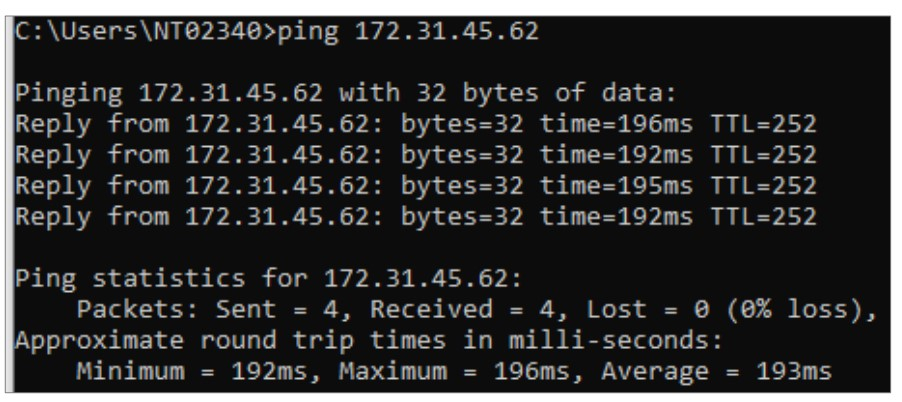
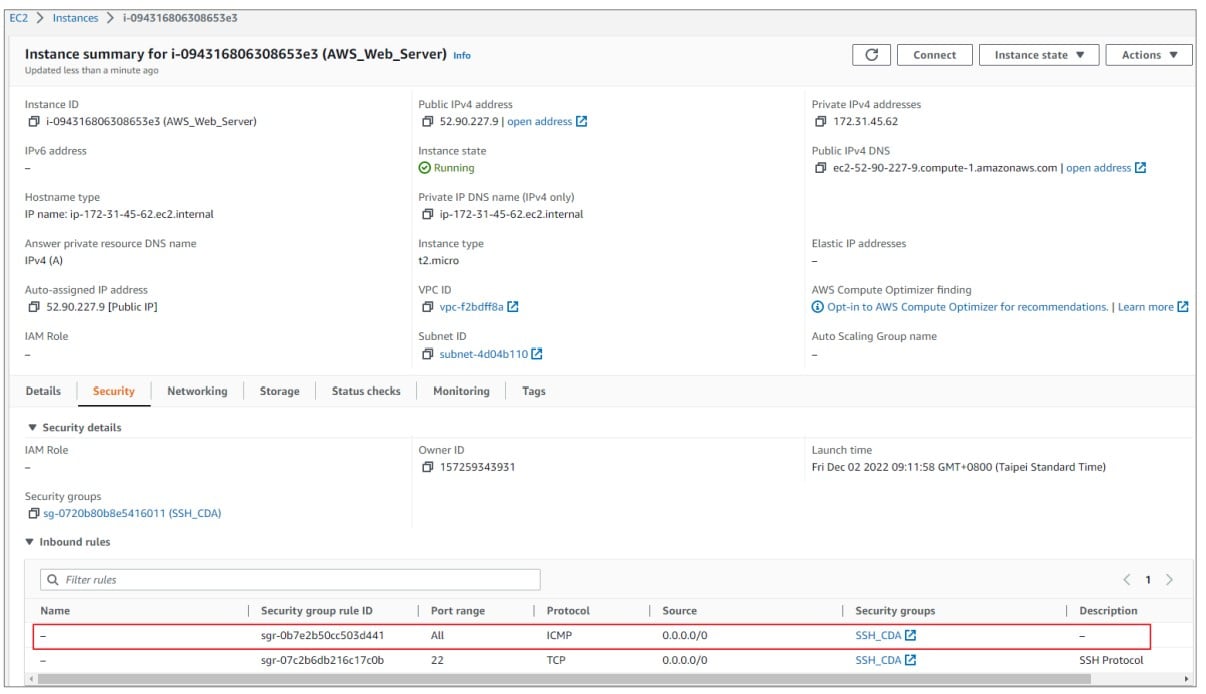
2. If the ping check fails, check the Security Group of the EC2 Instance. Make sure it allows the ICMP from the Internet
3. You also can check the VPN logs in CloudWatch for further investigate
1) Under 'Services', search and click on 'CloudWatch'.
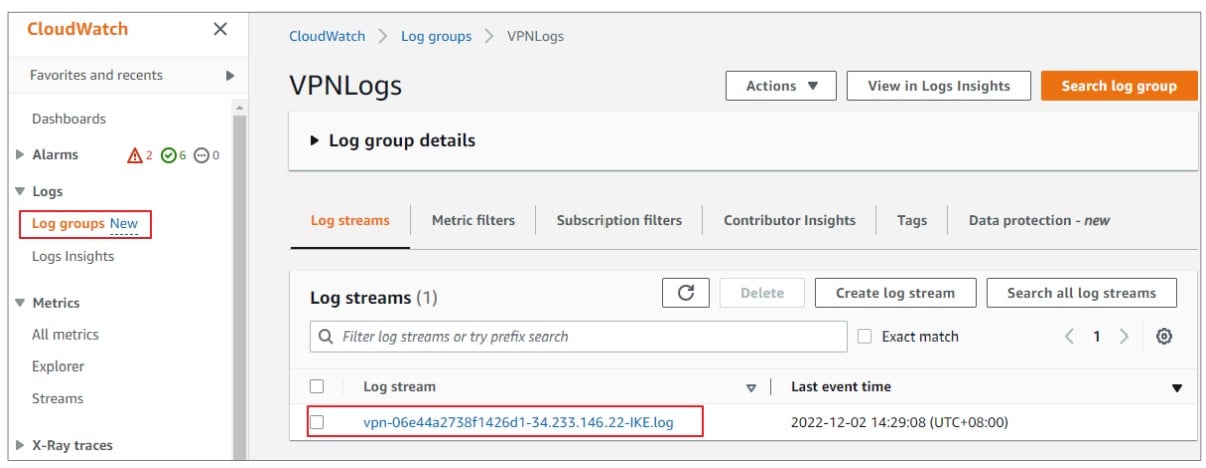
2) On the left navigation pane, scroll down to Logs. Click on ‘Log groups’. Choose the log group you store in above step, then you can see the detail log or export to cvs file
Please note that this configuration assumes that the public IP address is directly configured on the Zyxel gateway. Your configuration will be slightly different if your Zyxel gateway sits behind a NAT device.
 A.Configure VPN and Static Route on AWS
A.Configure VPN and Static Route on AWS 1. Create AWS Customer Gateway
1) Go to the AWS Portal: https://aws.amazon.com/console/ and sign in with your credentials
2) Under 'Services', search and click on 'VPC'.

3) Filter your VPC, for the ease of navigation. In this case, I used the default VPC

4) On the left navigation pane, scroll down to VIRTUAL PRIVATE NETWORK (VPN). Click on 'Customer Gateways'.

5) In the "Create customer gateway" blade, configure the following:
- Name: Specify any descriptive name.
- BGP ASN: leave as default value (65000)
- IP Address: Specify the public IP address of your Zyxel gateway.
- Certificate ARN (optional): In our scenario, no Certificate is selected.
- Device (optional): In our scenario, no Device is selected

2. Create a Virtual Private Gateway ( Attaching the VGW with your VPC)
1) Select the virtual network for which you want to create a virtual network gateway. In the left navigation pane, scroll down to VIRTUAL PRIVATE NETWORK (VPN). Click on 'Virtual Private Gateways'.
2) In the "Create Virtual Private Gateway" blade, configure the following:
- Name tag: Specify a descriptive Name
- ASN: Select the applicable option. In our scenario, select Amazon default ASN

3) Attach Virtual Private Gateway (VGW) to the VPC.
- Select the newly created VGW.
- Click on Actions and select Attach to VPC. Once the VGW is attached to the VPC, reapply the filter on your VPC as described above step


3. Create the Site-to-Site VPN connection
1) In the left navigation pane, scroll down to Site-to-Site VPN Connections. Click on 'Create VPN Connection'.

2) In the "Create VPN Connection" blade, configure the following:
- Name Tag: Specify a descriptive Name for the VPN connection
- Target Gateway Type: Select Virtual Private Gateway
- Virtual Private Gateway: From the drop-down box, Select the gateway created in above step
- Customer Gateway: Select Existing.
- Customer Gateway ID: From the drop-down box, Select the gateway created in above step
- Routing Options: Select Static.
- Static IP Prefixes: Provide the LAN address range behind the Zyxell Gateway
- Local IPv4 Network: Zyxel gateway LAN resources
- Remote IPv4 Network: AWS side resources

3) (Optional) Enable VPN logging. . For troubleshooting, you only have this option to enable the VPN logs when creating the VPN connection on AWS. You can not enable the option using AWS Console once the VPN connection created. The VPN logs will send to CloudWatch logs, specify the log group and format file to store.

4. Download and extract needed information from the configuration file
1) Select the newly created VPN connection and click on Download Configuration.

- Vendor: Zyxel
- Platform: Zywall Series
- Software: Zywall ZLD4.20+
- IKE version: ikev1
Click on "Download"

The configuration file is downloaded in txt format. The parameters given in the downloaded file should match the Phase 1 & Phase 2 parameters in the on-premises Zyxel gateway IPSec policy

5. Create a route in the route table associated with your VPC
1) In the left navigation pane, select your VPC. Navigate to VIRTUAL PRIVATE CLOUD > Route Tables. Select the associated Route Table.

2) In the bottom navigation:
- Select the Routes tab.
- Click on Edit routes.

3) Click on Edit routes and configure the following:
- Destination: LAN subnet behind Zyxel Gateway
- Target: Select the Virtual gateway created in Step 2.
- Click on Save routes.

B. Configure VPN and Static Route on Zyxel Gateway
AWS suggest you to establish 2 VPN connections to AWS, you can refer the txt file to create the VPN gateway, VPN connection, VTI interface, and static route. Note: Zyxel gateway does not support “-” character for VPN gateway and connection name, you must to modify.
1. Configure 2 VPN gateways as same as the txt file you download



2. Configure 2 VPN connection as same as the txt file you download

3. Configure 2 VTI interfaces corresponding to 2 VPN rules

4. Configure static route to forward the traffic to AWS LAN via VTI interfaces

5. Go to VPN connection tab, choose the VPN rule to connect.

C.Verification and Troubleshooting
1. PC under Zyxel Gateway LAN try to ping the EC2 Instance under the AWS LAN

2. If the ping check fails, check the Security Group of the EC2 Instance. Make sure it allows the ICMP from the Internet

3. You also can check the VPN logs in CloudWatch for further investigate
1) Under 'Services', search and click on 'CloudWatch'.

2) On the left navigation pane, scroll down to Logs. Click on ‘Log groups’. Choose the log group you store in above step, then you can see the detail log or export to cvs file


0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 480 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight