Captive Portal – Auth Policy List and New Matching Criteria
 Zyxel Employee
Zyxel Employee



As part of our continuous effort to improve user experience and network security, Zyxel Networks has introduced a USG FLEX H Series of enhancements to the Captive Portal feature. In this article, we’ll walk you through the key updates, including the newly designed Auth Policy List UI and the addition of matching criteria for web authentication.
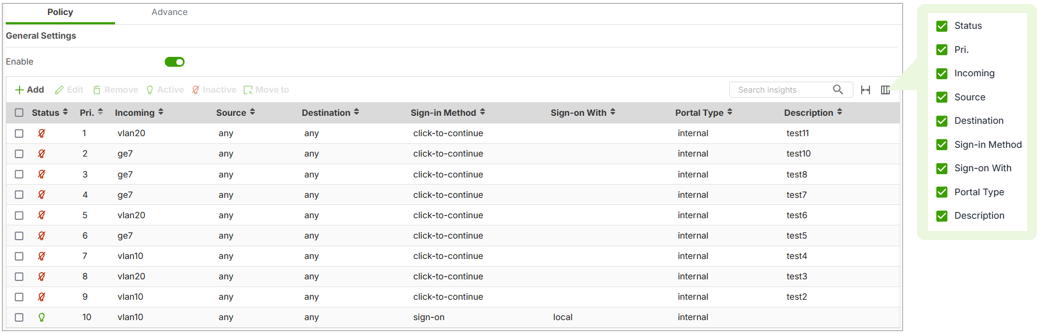
1. Redesigned Auth Policy List with Filterable Columns
In previous firmware versions, the Captive Portal Auth Policy List had a simple interface with limited visibility and customization. Users had no way to filter or customize the displayed data, making it harder to manage large configurations.
With the new firmware upgrade, the Auth Policy List has been added with a filterable UI, allowing administrators to select and display only the information they need. This makes it significantly easier to manage complex policies and improves the overall usability of the Captive Portal settings.
To access this feature:
- Navigate to Captive Portal > Authentication Policy > Policy
- You will now see an enhanced interface where you can filter columns based on policy attributes, helping you quickly locate and edit specific entries.
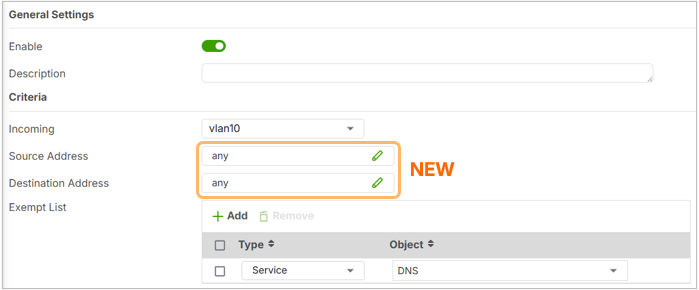
2. Expanded Matching Criteria for Authentication Policies
Another major upgrade in this firmware release is the introduction of additional matching criteria for triggering Captive Portal authentication. Previously, policies could only be applied based on the incoming interface. Now, you have more granular control through these new options:
Source Address
You can now define policies based on the source address, which can be:
- An IP address or subnet
- An address object for dynamic policy referencing
This is particularly useful in environments like large departments or campuses where only certain devices or user groups within a subnet need to be authenticated. For example, you can apply web authentication only to specific IP ranges, avoiding unnecessary authentication prompts for all users.
Destination Address
In scenarios where internal resources (e.g., intranet servers) must be secured, you can now define policies that enforce authentication when users access specific destination addresses. This ensures that access to sensitive internal systems is gated behind proper user verification.
Ensure redirection can occur when accessing the specific Destination Address.
3. Updates to Walled Garden and Exempt Lists
Prior to this update, Zyxel devices allowed configuration of Exempt Lists to specify resources that users could access before completing web authentication. However, in the new release:
- In the Exempt List, Destination IP has been removed and repurposed to Walled Garden setting.
The enhanced Walled Garden now supports both:
- Domain names
- IP addresses
This allows you to configure trusted destinations (like DNS services or support sites) that users can access even before logging into the Captive Portal.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight