VPN Failover and Fallback – Enhanced Redundancy for Site-to-Site Tunnels
 Zyxel Employee
Zyxel Employee



USG FLEX H Series Firewall now supports VPN Failover and Fallback - a powerful enhancement that ensures high availability in site-to-site VPN deployments. This feature enables firewalls to automatically switch to a backup VPN tunnel when the primary connection fails and revert back once the primary is restored.
In this article, we’ll explain how VPN failover and fallback works, and how to configure it.
1. Why This Feature Matters
Traditionally, site-to-site VPN configurations only supported a single peer gateway IP. If that link failed, VPN traffic would be interrupted. With VPN Failover and Fallback, the system now supports:
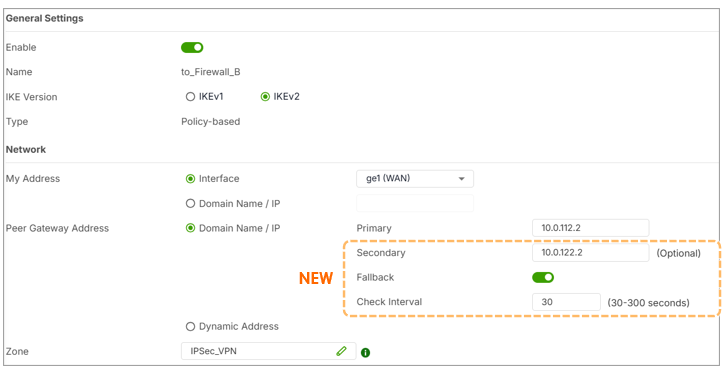
- Primary and secondary peer gateway IPs
- Automatic tunnel failover if the primary tunnel is down
- Automatic fallback to the primary tunnel once it recovers
2. VPN Failover vs. VPN Fallback
Both can be enabled to ensure uninterrupted VPN connectivity.
VPN Failover is switches to a backup VPN tunnel if the primary connection fails, VPN Fallback Reverts to the primary VPN tunnel once it is back online.
3. Configuration Overview
You can configure these settings either through the local firewall GUI or Nebula Control Center:
On the Local Firewall:
- Go to VPN > IPSec VPN >
- Enter Primary and Secondary Peer Gateway IPs
- Enable Failover
- (Optional) Enable Fallback and configure the interval (30–300 seconds)
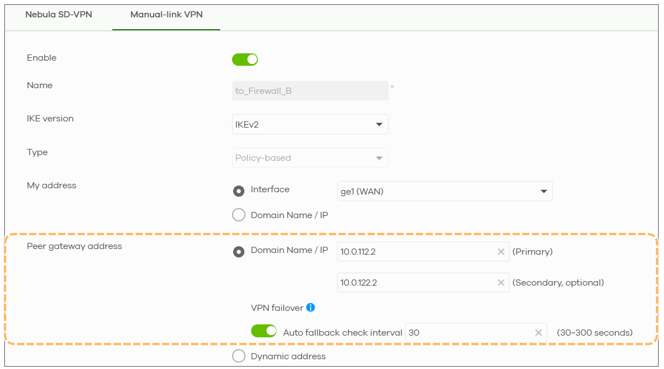
On Nebula:
- Navigate to Site-wide > Configure > Firewall > Site-to Site VPN
- Configuration interface mirrors the local firewall
4. How Failover Works
- When the primary tunnel goes down (e.g., WAN1 is unreachable), the firewall:
- Detects the failure using DPD (Dead Peer Detection)
- Attempts to establish a tunnel to the secondary IP
- Does this every 15 seconds by default
5. VPN Fallback: Return to Primary
Once failover has occurred, the firewall will periodically attempt to reconnect to the primary tunnel based on the Fallback Interval (default: 30 seconds, up to 300 seconds).
- As soon as the primary tunnel becomes available again, the firewall switches back to it.
- The process does not depend on whether the secondary tunnel is active or down.
6. Monitor and Troubleshoot Failover
VPN Status Page:
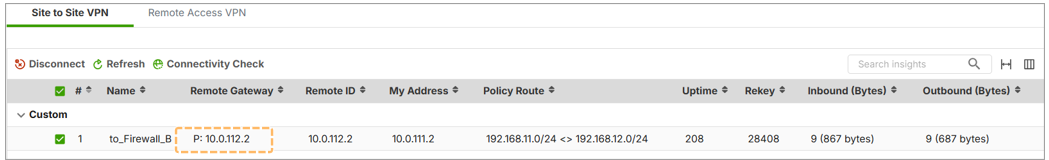
How can we verify which link the VPN is using?
- Navigate to VPN Status > IPSec VPN > Site-to-Site
- Look for:
- P = Primary peer IP is active
- S = Secondary peer IP is active
- D = Dynamic peer address (used when peer uses dynamic IP)
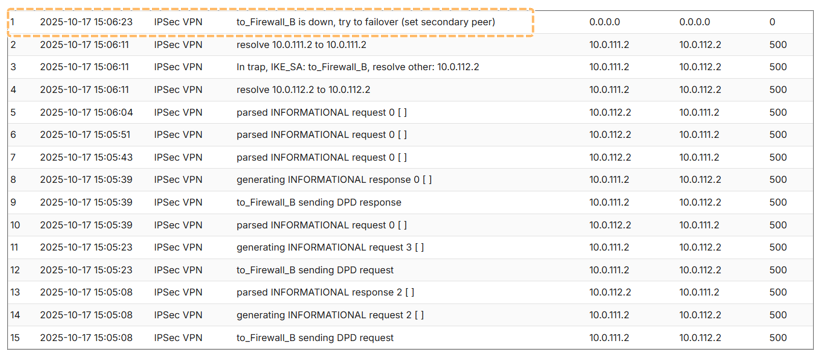
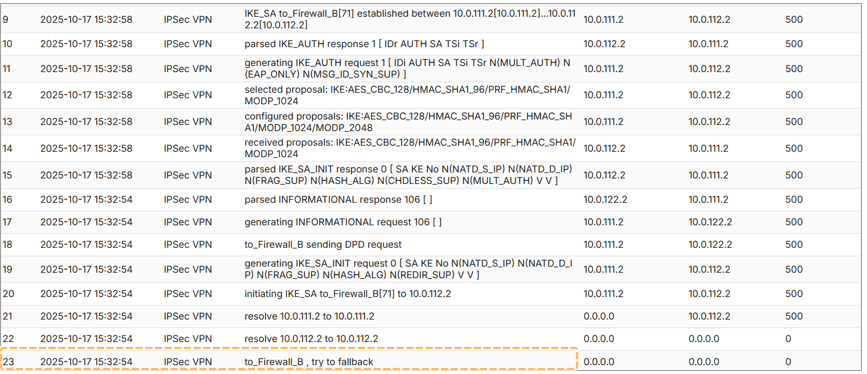
Event Logs:
- Found under Monitor > Log > System Events
- Logs display:
- DPD failure
- Failover to secondary peer
- Fallback to primary peer
Example: Failover Log
Example: Fallback Log
7. Adjusting Failover Interval (Advanced)
Failover timing can only be changed via CLI, not the GUI.
Notice: This setting is also related to Initiation – Nailed-up. Because this is a global option for VPN setting.
CLI Commands:
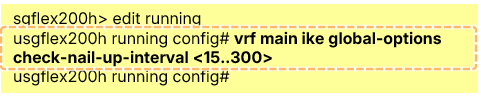
View settings:
- usgflex200h> show config vrf main ike global-options
Modify failover interval:
- usgflex200h running config# vrf main ike global-options check-nail-up-interval <15..300>
[Important] This interval affects all VPN tunnels configured for failover and VPN tunnel set to Nailed-up.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight