Policy-Based VPN with Policy Routes – Advanced Control for Multi-Subnet Environments
 Zyxel Employee
Zyxel Employee



USG FLEX H Series Firewall continues to offer flexible VPN deployment options with support for Policy-Based VPN using Policy Routing. While route-based VPNs are commonly used in modern deployments, policy-based VPNs still hold value for scenarios involving specific subnet-to-subnet communication and USG FLEX/ATP firewall compatibility.
In this article, we’ll explain how policy-based VPN works, how to configure it using policy routes, and how to ensure proper traffic flow across multiple subnets.
1. Multi-Subnet Challenges with Policy-Based VPN
Older firewall models (e.g., USG FLEX /ATP series) support only one VPN phase 2 selector, meaning only one local/remote subnet pair can be defined. However, Zyxel's newer USG FLEX H series support multiple phase 2 selectors, allowing more flexible subnet-to-subnet communication—even with policy-based VPN.
Some customers may still use the older ZLD firewall, while others use the new H Series firewall. So, if we want multiple VPN subnets ️to communicate between the two firewalls, we need to use a Policy-Based VPN with Policy Routes.
2. New Naming Rule of VPN Phase 2 Policy
When you create a policy-based VPN:
- The system automatically generates VPN interface names like test_SP1, test_SP2, etc.
- These are used as next-hop interfaces in policy routes
After the policy is applied, the VPN interface name becomes read-only, so define custom names before saving.
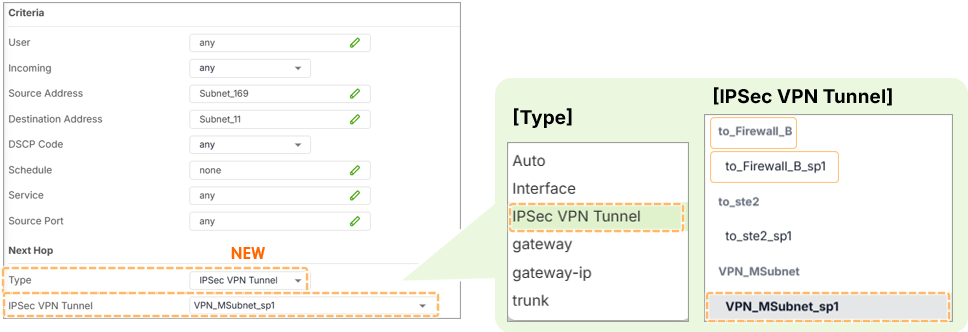
3. Configuring Policy Routes for VPN Tunnels
Steps (Local Firewall):
- Go to Network > Routing
- Add a Policy Route
- Set the next-hop type to IPSec VPN Tunnel
- Choose the corresponding VPN interface (e.g., test_SP1)
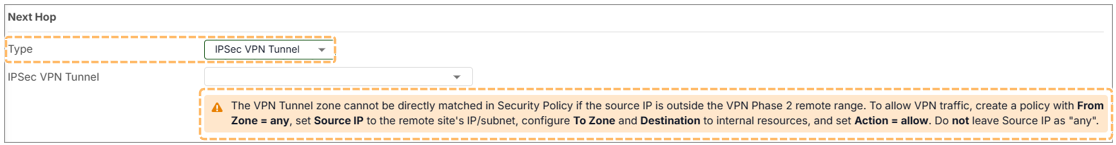
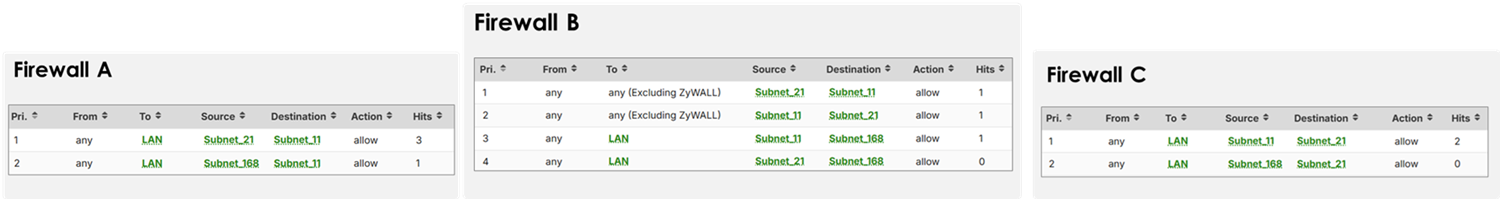
Policy Control Requirement
In current firmware (v1.36), additional policy control rules are required to allow traffic through the VPN tunnel:
- Go to Security Policy > Policy Control
- Add rules to allow VPN source/destination subnets
This is necessary because encrypted traffic cannot match zone in this firmware, otherwise be blocked by the default deny rule, we plan to implement this in the next release.
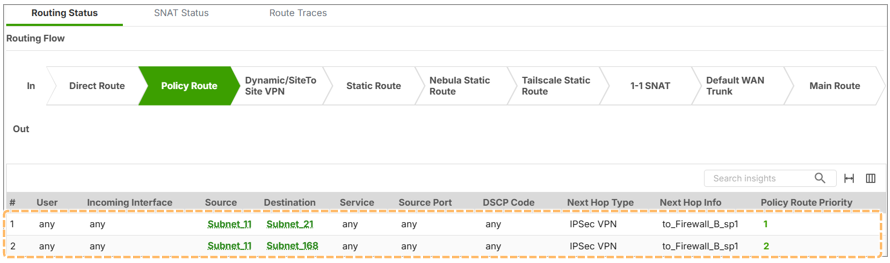
4. Monitoring and Troubleshooting
🔍 Use Packet Flow Explorer:
- Navigate to Maintenance > Packet Flow Explorer
- See how packets are routed (via policy route, VPN interface, etc.)
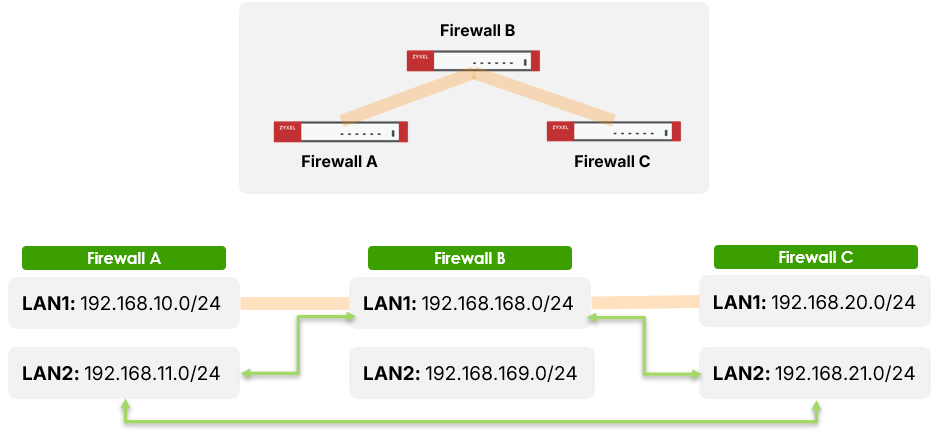
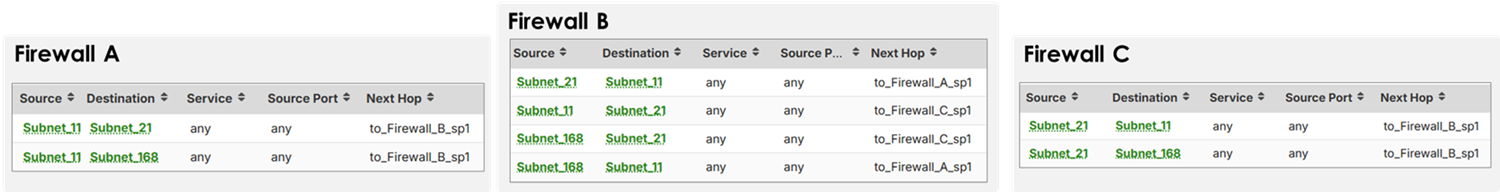
5. Scenario: Multi-Hop VPN with Policy Routing
In a 3-site setup (Firewall A ⇄ B ⇄ C):
- Step 1: Establish VPN tunnels A–B and B–C and verify VPN connection
- Step 2: Use policy routes to allow subnet traffic from C to A via B
- Step 3: Ensure policy control rules are in place across all firewalls
Policy-based VPN with policy routes is fully supported on Nebula as well. VPN interface naming and routing references follow the same behavior as on standalone firewalls
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight