Configure vlan in atp 200
Hello,
I have a Zyxell atp 200 firewall with 4 lan ports. and several unifi switches 16 and 24 ports.
right now I am connecting an unifi switch 16 ports to the firewall.
I would like to have:
firewall lan port 1 for vlan 1 and 20 connected to unifi switch port 1
firewall lan port 2 for vlan 10 connected to unifi switch port 2
firewall lan port 3 for vlan 30 connected to unifi switch port 3
firewall lan port 4 for vlan 40 connected to unifi switch port 4
The firewall should be giving the ip via dhcp for the vlans
In the firewall I configured:
lan 1 port to give an ip address via dhcp yyy.yyy.yyy.yyy
lan 2 port to give an ip address via dhcp aaa.aaa.aaa.aaa
lan 3 port to give an ip address via dhcp bbb.bbb.bbb.bbb
lan 4 port to give an ip address via dhcp ccc.ccc.ccc.ccc
vlan1 to give another range of addresses xxx.xxx.xxx.xxx
vlan 20 to give another range of addresses zzz.zzz.zzz.zzz
then selected for vlan 1 and vlan 20 to be on the lan 1 port of the firewal.
when i connect the swith to the firewall it gets the ip in the yyy.yyy.yyy.yyy range.
Is it the correct behaviour?
how can I check if the vlans are applied?
Kindest Regards.
Accepted Solution
-
Hi @Hoygen83 ,
After setup VLAN settings on ATP200.
You can setup setting on switch and try to connect client to switch to test if the client could get the VLAN IP address.
Here is the ATP 200 &switch settings below,
ATP200 settings
Go to Configuration > Network > Interface > VLAN > ADD VLAN
Set VLAN 20 settings
SWITCH GS-1900 settings
Add VLAN20 on switch
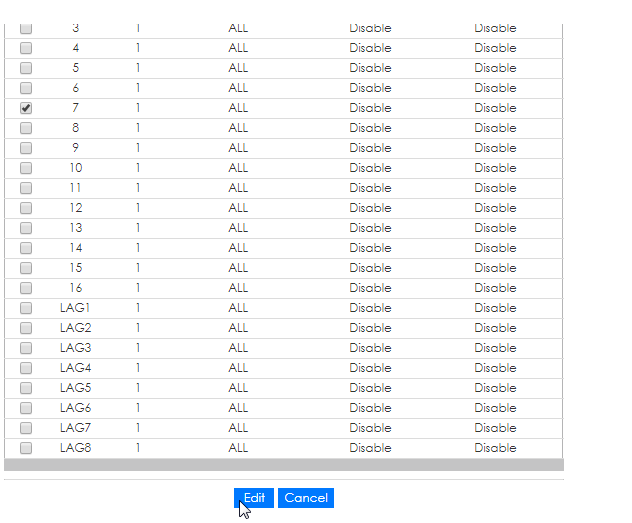
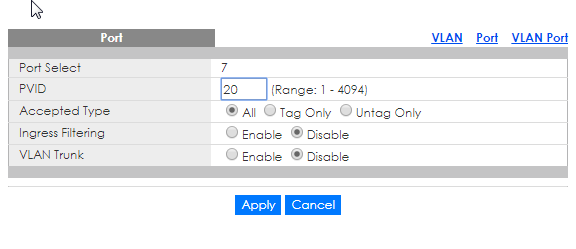
Go to port to add VLAN to the port on switch
Select the port on switch and click Edit
Select VLAN ID for the port and click apply
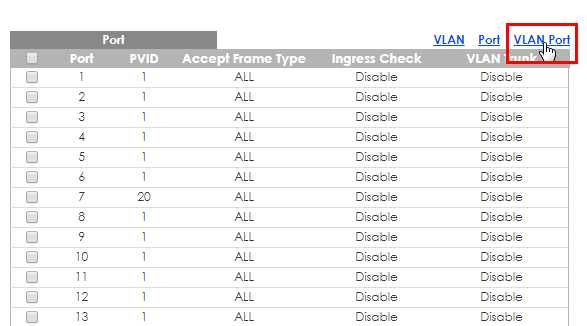
Go to VLAN Port
Select the VLAN ID to choose which port should tagged or not tagged VLAN ID
Select tagged or untagged port for VLAN20
Test Result
5
All Replies
-
Hi @Hoygen83 ,
After setup VLAN settings on ATP200.
You can setup setting on switch and try to connect client to switch to test if the client could get the VLAN IP address.
Here is the ATP 200 &switch settings below,
ATP200 settings
Go to Configuration > Network > Interface > VLAN > ADD VLAN
Set VLAN 20 settings
SWITCH GS-1900 settings
Add VLAN20 on switch
Go to port to add VLAN to the port on switch
Select the port on switch and click Edit
Select VLAN ID for the port and click apply
Go to VLAN Port
Select the VLAN ID to choose which port should tagged or not tagged VLAN ID
Select tagged or untagged port for VLAN20
Test Result
5 -
Thank you sir.
0 -
0
-
I read that quick. I need several different Vlan Configs like:a) a Guest Network with limited Access from the Contend Filter, Bandwith limit,...b) my own Vlan who I have my stuff in it.c) a Vlan for Device Manangment with no Internetd) a Vlan for Phones who is conect to my virtual PBX and to the Internet.Is there a easy way for that? Currently my USG300 run with one Lan only because not all switch are Vlan ready.0
-
Hi @ Username_is_reserved
Here is example settings of VLAN
a) a Guest Network with limited Access from the Contend Filter, Bandwidth limit,...
Go to Configuration > Network > Interface > VLAN to setup the settings

Go to Configuration > Anti-X > Content Filter > General to enable content filter

Go to Configuration > Anti-X > Content Filter > Filter Profile to create a profile for content filter
and go to Configuration > Anti-X > Content Filter > General > Policies to add a rule for guest

For the bandwidth limit, it can add a rule on BWM settings
Go to Configuration > BWM to setup the settings

b , c ,d, Go to Configuration > Firewall > Firewall to setup the rule,
below is the example setting to add a rule for these VLAN
b) my own Vlan who I have my stuff in it.
It can add a firewall rule for it

c) a Vlan for Device Management with no Internet
Add a rule to deny the access to the Internet

d) a Vlan for Phones who is connect to my virtual PBX and to the Internet.
Add a firewall rule for your phones rule

After setup VLAN settings on USG300, it also need to setup vlan setting on switch.
0 -
Interesting method to route the VLAN traffic (using the source filter). Curious if you all see pros/cons to doing that vs making each VLAN it's own Zone. For example, here is a fairly involved setup we have for a client needing extensive VLANs themselves and then VLANs for tenants in small offices they rent out:

You can see security camera access in. They have a bench LAN that's a sort of hotzone and for a time needed to print to a LAN based printer (inactive now). Then you see the LAN to any is gone and restricted to WAN. Then each VLAN is the same, with their own filtering profiles as needed. We just disable the VLAN and Security Policy (redundant probably) for spaces not rented out. We also use a restricted service group for the VLAN access to the Zyxel:
And for the VLANs they are tied to their own Zone:
This provides pretty solid isolation between the VLANs and makes management more logical since the Zone identifiers provide an easy to recognize label throughout the gateway configuration.
Do you all see downsides to this method vs the source/destination filtering? The LAN to any always felt 'wrong' in a VLAN scenario where the VLANs needed to be islands (vs just filtered routes).0 -
HI @ itxnc
Thanks for your sharing and yes there are different methods to achieve certain purpose.
One is per vlan per zone, this kind of settings help administrator to easily control the rules on the device.So that all the rules can be shown on the firewall rule page, however, if there’re multiple vlans in setting, per vlan per zone may lead to multiple firewall rules that need to be managed.
Or users can just put multiple vlans in a zone, this can help administrator to have fewer the managed firewall rules.
0
Categories
- All Categories
- 434 Beta Program
- 2.7K Nebula
- 174 Nebula Ideas
- 117 Nebula Status and Incidents
- 6.1K Security
- 418 USG FLEX H Series
- 297 Security Ideas
- 1.6K Switch
- 78 Switch Ideas
- 1.2K Wireless
- 43 Wireless Ideas
- 6.7K Consumer Product
- 270 Service & License
- 416 News and Release
- 87 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.1K FAQ
- 34 Documents
- 34 Nebula Monthly Express
- 83 About Community
- 87 Security Highlight
 Freshman Member
Freshman Member

 Zyxel Employee
Zyxel Employee











 Ally Member
Ally Member





